Up to 50,000 servers were infected over the past four months as part of a high-profile cryptojacking campaign, believed to orchestrated by Chinese-language adversaries.
Researchers with Guardicore Labs, who disclosed the campaign Wednesday, said that the Nansh0u campaign (named due to a text file string in the attacker’s servers being called Nansh0u) is “not another run-of-the-mill mining attack.”
The cryptomining malware, which targets an open source cryptocurrency called TurtleCoin, is being spread via a sophisticated campaign relying on techniques often utilized by advanced persistent threat (APT) groups, such as using certificates and 20 different payload versions.
“Breached machines include over 50,000 servers belonging to companies in the healthcare, telecommunications, media and IT sectors,” researchers said in an analysis. “Once compromised, the targeted servers were infected with malicious payloads. These, in turn, dropped a crypto-miner and installed a sophisticated kernel-mode rootkit to prevent the malware from being terminated.”
The Campaign
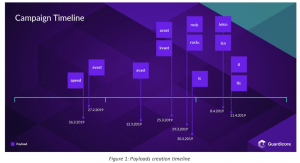
The campaign has been ongoing since February, researchers said. In April, researchers noticed three similar attacks – all had source IP addresses originating in South Africa, shared the same attack process and used the same breach method.
“Looking for more attacks with a similar pattern, we found attacks dating back to February 26, with over seven hundred new victims per day,” said researchers. “During our investigation, we found 20 versions of malicious payloads, with new payloads created at least once a week and used immediately after their creation time.”
The campaign was rapidly infecting servers – in fact, within the timeframe of April 13 to May 13, researchers observed the number of infections double to 47,985.
Victims were mostly located in China, the U.S. and India – however, attackers also reached victims in up to 90 countries, Guardicore researchers told Threatpost.
Researchers also believe that China-linked attackers are behind the attack, as the hackers chose to write their tools with Chinese-based programming language EPL, and many log files and binaries on the servers included Chinese strings.
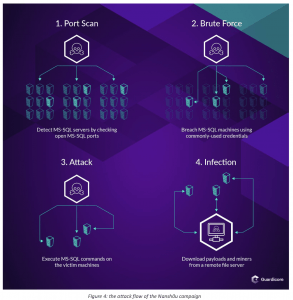
The Attack Process
Attackers would seek out MS-SQL servers by scanning IP addresses for open MS-SQL ports. They then would use brute force methods to breach those exposed machines (using commonly-utilized credentials).
“The tool attempts to login to each MS-SQL server using tens of thousands of common credentials,” researchers said. “Once authentication succeeds – the server’s address, username and password are saved to a file for future use.”
From there, the bad actor logged into the victims’ systems, execute MS-SQL commands on the machines, and download payloads and cryptocurrency miner malware from a remote file server.
The commands specifically execute a known privilege escalation exploit (CVE-2014-4113) that runs the malicious payload with SYSTEM privileges.
Researchers also collected 20 payload samples from the attacker servers – all which had several functionalities, including the abilities to execute a crypto-currency miner and protect the miner process from termination through a kernel mode rootkit. Specifically, the closed-source JCE miner and open source XMRig miner were utilized to target the TurtleCoin cryptocurrency.
“The attacker’s overt goal was cryptomining,” Daniel Goldberg, security researcher with Guardicore Lab, told Threatpost. “This is what takes up the victims’ resources and directly generates money. A side goal is access. The attacker kept careful logs of breached servers that he could later reuse or sell.”
When asked how much the attackers were profiting from the cryptomining malware, researchers told Threatpost that TurtleCoin is a privacy oriented cryptocurrency, making it extremely difficult to get an accurate and reliable count of the amount in the wallet.
Sophisticated Arsenal
The campaign “uses techniques often seen in APTs such as fake certificates and privilege escalation exploits,” researchers said. “While advanced attack tools have normally been the property of highly skilled adversaries this campaign shows that these tools can now easily fall into the hands of less than top-notch attackers.”
One such technique is that many payloads in the campaign drop a kernel mode driver and used digital signatures to mask suspicious activity. Kernel-mode drivers are executable files run within the operating system’s kernel. As such, they have high-privileged access to sensitive data structures and resources.
This particular driver had a digital signature issued by Certificate Authority Verisign. That certificate has the name of a fake Chinese company (Hangzhou Hootian Network Technology). Researchers contacted Verisign and informed them of the certificate resulting in the certificate being revoked.
The driver was also protected and obfuscated with VMProtect, a software tool “that attempts to frustrate reverse engineers and malware researchers,” said researchers.
The Need for Strong Credentials
Researchers pointed to weak authentication username and passwords on Windows MS-SQL servers as a main reason behind the attack – and urged system administrators to consider strong credentials.
“This campaign demonstrates once again that common passwords still comprise the weakest link in today’s attack flows,” they said. “Seeing tens of thousands of servers compromised by a simple brute-force attack, we highly recommend that organizations protect their assets with strong credentials as well as network segmentation solutions.”
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.