Adobe has issued patches for critical flaws across its Adobe Flash Player and Acrobat Reader products, which could enable arbitrary code execution.
Overall, the company fixed 87 vulnerabilities across Acrobat and Reader, Flash Player and Adobe Media Encoder as part of its regularly-scheduled updates this month. Adobe said that it is not aware of any flaws being actively exploited at this time.
“Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS,” Adobe said on Tuesday. “These updates address critical and important vulnerabilities. Successful exploitation could lead to arbitrary code execution in the context of the current user.”
The majority of flaws (84 in total) exist in Adobe Acrobat and Reader, Adobe’s family of products allowing users to create and manage PDF files. That includes 36 important information disclosure flaws and 48 critical-severity arbitrary code execution vulnerabilities.
Those critical flaws include six out-of-bounds write flaws (CVE-2019-7829, CVE-2019-7825, CVE-2019-7822, CVE-2019-7818, CVE-2019-7804, CVE-2019-7800), a type confusion glitch (CVE-2019-7820), two heap overflow flaws (CVE-2019-7828, CVE-2019-7827), a buffer error bug (CVE-2019-7824) a double free vulnerability (CVE-2019-7784) and a security bypass (CVE-2019-7779).
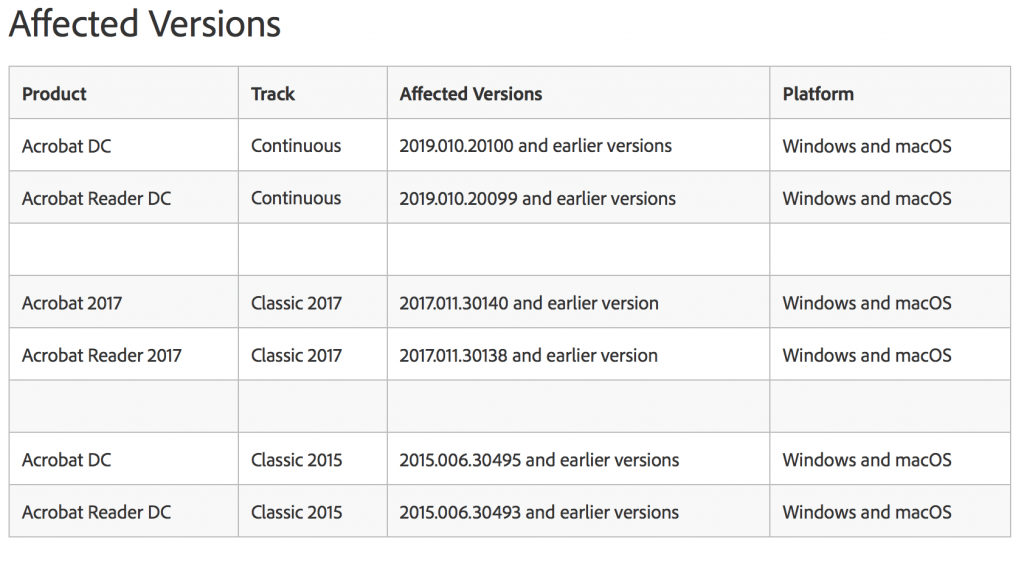
Below are impacted Acrobat and Reader versions. Users are urged to update to the latest versions of the products, with the priority update rating “2,” meaning the update resolves vulnerabilities in a product that has historically been at elevated risk.
Adobe Flash Player, meanwhile, has a critical use-after-free vulnerability that could enable arbitrary code execution “in the context of the current user,” on impacted systems. The flaw was anonymously reported via Trend Micro’s Zero Day Initiative.
The bug, CVE-2019-7837, is in Adobe Flash Player for Desktop Runtime, Google Chrome, Microsoft Edge and Internet Explorer 11 (versions 32.0.0.171 and earlier). Users are urged to update to version 32.0.0.192.
Finally, two flaws exist in Adobe Media Encoder version 13.0.2, a product which allows users to easily encode audio and video in a variety of formats. This product has a critical use-after-free glitch (CVE-2019-7842) which could enable remote code-execution; as well as an important out-of-bounds read information disclosure flaw (CVE-2019-7844). Users are encouraged to update to Media Encoder version 13.1. Mat Powell of the Trend Micro Zero Day Initiative is credited with reporting the two flaws.
“Adobe has released an update for Adobe Media Encoder,” according to the advisory. “This update resolves a critical file parsing vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user.”
Acrobat Reader also represented the bulk of security flaws in April’s regularly-scheduled patches– while Adobe issued fixes for 43 different CVE numbers across eight different products, Acrobat Reader had 21 vulnerabilities overall, 11 of which were critical arbitrary code execution flaws.
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.