 UPDATE: After announcing that it was accelerating a critical patch of its Reader program last week, Adobe pushed out a large patch on Tuesday, fixing 23 separate vulnerabilities in its Reader and Acrobat applications.
UPDATE: After announcing that it was accelerating a critical patch of its Reader program last week, Adobe pushed out a large patch on Tuesday, fixing 23 separate vulnerabilities in its Reader and Acrobat applications.
The huge quarterly security update included company issued Security Bulletin APSB10-21, patching Adobe Reader up to and including Version 9.3.4 for Windows, mac and UNIX, and Acrobat 9.3.4 for Windows and Macintosh. The patches had originally be scheduled for October 12, 2010 as part of the company’s regularly scheduled quarterly security update.
Included in the patch are fixes for two vulnerabilities, CVE-2010-2883 and CVE-2010-2884, that are rated critical and that are already being exploited. Adobe said last week that it would move up the patch to plug the hole in Reader that was first disclosed in September and could give remote attackers control over host systems. That hole, described as a stack overflow in the CoolType.dll used by both Reader and Acrobat, could allow an attacker to crash reader and run their own code on vulnerable systems. It is actively being exploited. The CVE-2010-2884 vulnerability is “unspecified” but effects Reader, Acrobat and Flash and could be used both in denial of service attacks and to run malicious code on vulnerable systems, Adobe said. It is reported to have been used to compromise instances of Flash Player on Windows.
The two vulnerabilities have been targeted for at least two months, said Kurt Baumgartner, a senior security researcher at Kaspersky Lab.
Baumgartner demonstrated at the Virus Bulletin Conference last week how both vulnerabilities, coupled with return-oriented programming techniques, might be used to evade the latest hardware based protections, dubbed Data Execution Prevention, or DEP, in Windows Vista and Windows 7.
Kaspersky data shows that most attacks using the CoolType.dll vulnerability (2883) rely on malcrafted Adobe .pdf variants and have targeted victims in Western Europe and the U.S., as well as Russia. The exploits have been linked to attempts to propagate common malware like the Zeus and Zbot online banking Trojans.
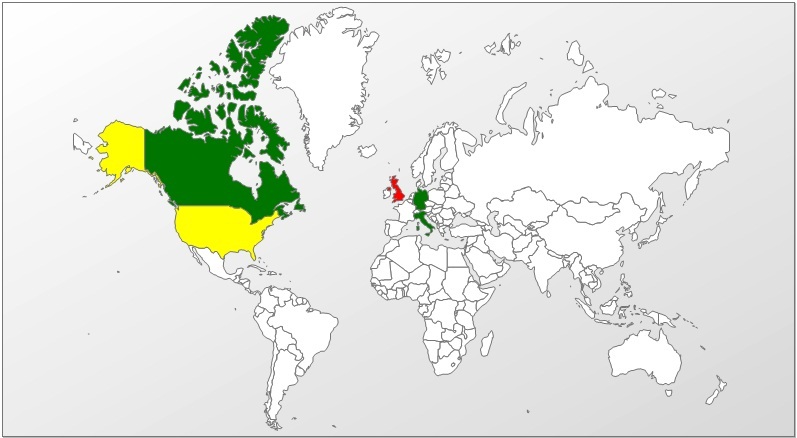
“Users are probably lured in to
opening the file with targeted attacks and blackhat SEO tactics,” Baumgartner wrote in an e-mail.
The 2884 vulnerability affects Flash and Reader and is also being exploited, though fewer attacks have been spotted using that hole. Kaspersky has detected gaming password stealers and other payloads being
delivered with it, Baumgartner said.
In its bulletin, Adobe recommends applying the patches immediately on vulnerable systems.









