 It’s no secret to anyone who has been paying attention that Adobe Reader and Acrobat have become prime targets for attackers in the last year or so, but new research shows just how dramatic the increase has been in the number of high-risk vulnerabilities identified in Adobe products recently.
It’s no secret to anyone who has been paying attention that Adobe Reader and Acrobat have become prime targets for attackers in the last year or so, but new research shows just how dramatic the increase has been in the number of high-risk vulnerabilities identified in Adobe products recently.
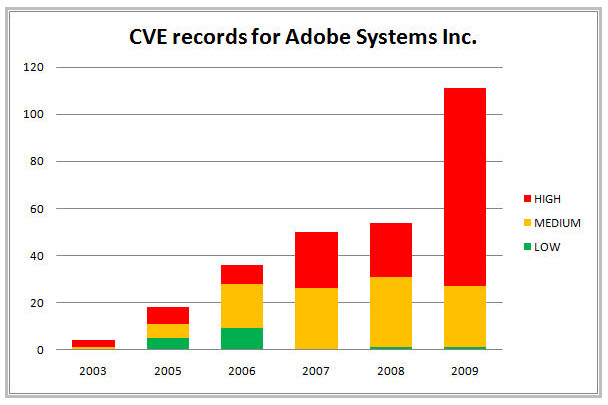
Researchers at McAfee have taken a look at the volume of serious vulnerabilities entered into the Common Vulnerabilities and Exposure database in the last few years and found that there was a huge jump from 2008 to 2009, with the pattern continuing in the first few months of this year. In 2008 there were nearly 60 Adobe vulnerabilities in the CVE database. That number nearly doubled in 2009 to close to 120 total flaws. So far in 2010, there have been 24 unique CVE identifiers assigned to Adobe vulnerabilities.
Today malware involving malformed PDF file are legion. From less then
2 percent of malware directly connected to exploits in 2007 and 2008,
they have reached 17 percent in 2009 and 28 percent during the first
quarter of 2010. For Adobe Reader software, 2010 seems to be the year of
living dangerously.
Adobe’s products are among the more widely installed pieces of software worldwide, so the security of Reader, Acrobat and Flash affect more users than problems in Windows, Internet Explorer or just about any other piece of software. And Adobe has been under the microscope on security issues for some time now, especially with regard to its patching and update process.
In related news, a new generic system for detecting malicious code in PDFs has debuted. Known as Joedoc, the system enables users to upload a suspicious PDF, which the service will test and then email the results to the user. The exploit-detection system works by opening the documents inside a virtual machine sandbox, then tracing the execution path of the code in the document.
To check if a document is malicious or not the EPs are extracted from
the corresponding execution trace and compared with the set of good EPs.
If the number of new EPs exceeds a predefined threshold Joedoc
identifies the given document as malicious.
Summarized Joedoc detects exploits by checking if new code is executed
(e.g. shellcode) and if given code is executed differently
(e.g. return-to-libc).
This is similar to the way that anti-malware researchers analyze new samples, and it’s designed to catch most well-known exploit behaviors. But, as the Joedoc site makes clear, it won’t detect everything.
“Like all other runtime systems Joedoc has problems with exploits which
need
special triggers (e.g. user behaviour like mouse clicks on a pdf) to be
executed. Another problem are unreliable exploits. If an exploit does
not work in the virtual machine, then Joedoc does not detect anything,” the documentation explains.









