AMD is seeking to downplay side-channel attacks that can leak potentially sensitive data from its processors released between 2011 and 2019.
The “Take A Way” attack, so-called by researchers with the Graz University of Technology in a new analysis this weekend, is a side-channel attack. Side-channel attacks extract sensitive information from signals created by electronic activity within computing devices as they carry out computation. There are an array of techniques to launch side-channel attacks, including using caches, branch predictors or analog signals. In this case, “Take A Way” leverages the way AMD stores memory, through the L1-data (L1D) which refers to the data cache and pools of memory that contain the leak-able data within CPUs.
AMD this weekend said it does not believe these are “new speculation-based attacks” and did not offer any mitigations: “We are aware of a new white paper that claims potential security exploits in AMD CPUs, whereby a malicious actor could manipulate a cache-related feature to potentially transmit user data in an unintended way,” said AMD in a Saturday advisory. “The researchers then pair this data path with known and mitigated software or speculative execution side channel vulnerabilities. AMD believes these are not new speculation-based attacks.”
In an email to Threatpost, researchers responded that “Take A Way” presented several side-channel attacks, but only one of them could be combined with speculative execution. Speculative execution is not required to exploit the side channel flaw, they said.
“Indeed, these are not new speculation-based attacks,” Daniel Gruss, one of the researchers behind the attack, told Threatpost via email. “But we also never said they were!? So, I don’t know why they would make such a statement – it seems to have nothing to do with our attacks.”
Take A Way
To create the “Take A Way” side-channel attack researchers said they reverse-engineered AMD’s L1D cache way predictor. The cache way predictor is a tool that predicts where the data is stored in the processor. This predictor, which exists in microarchitectures for AMD between 2011 (starting with the Bulldozer microarchitecture) to 2019, was introduced in AMD processors as a way to optimize energy consumption and performance for CPUs.
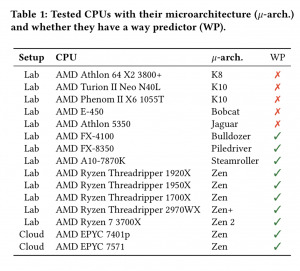 In reverse engineering the L1D cache way predictor, researchers were able to detect when the data is accessed by various processes -and then use that knowledge to leak small pieces of data from the CPU. Researchers then created to two subset attacks as part of “Take A Way” that took advantage of this process, which they dubbed “Collide+Probe” and “Load+Reload.”
In reverse engineering the L1D cache way predictor, researchers were able to detect when the data is accessed by various processes -and then use that knowledge to leak small pieces of data from the CPU. Researchers then created to two subset attacks as part of “Take A Way” that took advantage of this process, which they dubbed “Collide+Probe” and “Load+Reload.”
“With Collide+Probe, an attacker can monitor a victim’s memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core,” said researchers. “With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core. While Load+Reload relies on shared memory, it does not invalidate the cache line, allowing stealthier attacks that do not induce any last-level-cache evictions.”
One of these attacks, Collide+Probe, can be combined with speculative execution to use a side-channel analysis to gain unauthorized disclosure of information. Speculative execution (leveraged by the Spectre attack first disclosed impacting Intel chips in 2018) is used in microprocessors so that memory can read before the addresses of all prior memory writes are known.
The “Take A Way” attack is similar to other side-channel attacks released in the past few years, starting with the disclosure of Spectre and Meltdown in 2018 and continuing with the discovery of a class of side channel vulnerabilities called “ZombieLoad,” that impacted all modern Intel chips and used speculative execution to potentially leak sensitive data from a system’s CPU.
On Twitter, Gruss, said that the latest speculative execution attack is “certainly not” as severe as Meltdown or ZombieLoad. He told Threatpost, a plausible attack would come from an unprivileged local attacker.
Certainly not. The attacks leak a few bit of meta-data. Meltdown and Zombieload leak tons of actual data.
— Daniel Gruss (@lavados) March 7, 2020
Researchers said that they disclosed their findings to AMD on Aug. 23, 2019, and also outlined hardware and software based mitigations and countermeasures in their research.
However, in its advisory this weekend AMD did not release new mitigations, instead pointing to other previously disclosed speculative execution attacks that leveraged L1D, and recommending that CPU users keep their operating systems up to date, follow secure coding methodologies and implement the latest patched versions of critical libraries (including those susceptible to side channel attacks).
But Vedad Hadžić, one of the researchers behind the attack, said that existing mitigations don’t fix “Take A Way” vulnerabilities.
Well, no. The way predictor still behaves like described in the paper. It leaks info on addresses and is not as severe as #meltdown. Aside from the ASLR breaks, the two attacks are just building blocks similar to Prime+Probe and Flush+Reload.
— Vedad Hadžić (@duxcode) March 8, 2020
Threatpost has reached out to AMD for further clarification.
Interested in security for the Internet of Things and how 5G will change the threat landscape? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.











