Researchers are warning that “human operated” ransomware campaigns are growing more sophisticated, adopting new infection tactics and lateral movement techniques that traditional defense teams aren’t equipped to handle.
Researchers said that “auto-spreading” ransomware – like WannaCry and NotPetya – are making headlines due to the crippling downtimes that these attacks cause. However, “human operated” ransomware – like REvil, Bitpaymer, and Ryuk – are adopting new techniques that are enabling them to operate unfettered in networks.
For instance, “human operated” ransomware attacks focus on compromising accounts with high privileges. They are exhibiting extensive knowledge of systems administration and common network security misconfigurations. Researchers said hey are also able to adapt once they’ve initially infected a system and establish a foothold on machines. That allows these next-gen ransomware attackers to continue unabated in infiltrating target environments, said researchers with Microsoft’s Threat Protection Intelligence Team.
“These attacks are known to take advantage of network configuration weaknesses and vulnerable services to deploy devastating ransomware payloads,” said researchers on Thursday. “And while ransomware is the very visible action taken in these attacks, human operators also deliver other malicious payloads, steal credentials, and access and exfiltrate data from compromised networks.”
‘Smash-and-Grab’
Microsoft said one trend it has observed is a “smash-and-grab monetization” technique, where attackers infiltrate a system via brute force, and proceed with deploying the ransomware, credential theft, and other attacks – all in less than an hour, decreasing the chances of affected victims to intervene.
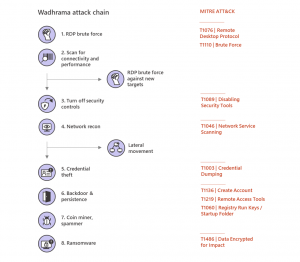
Researchers tracked one popular ransomware group leveraging this method, which they call Parinacota (which deploy the ransomware also known as Dharma) for 18 months. Over time, the group has grown to now impact three to four organizations weekly; as well as evolved its tactics and goals to “use compromised machines for various purposes, including cryptocurrency mining, sending spam emails, or proxying for other attacks.”
Parinacota employs the smash-and-grab method. They first brute force their way into vulnerable Remote Desktop Protocol (RDP) servers exposed to the internet and then rapidly scan for other vulnerable systems within the network. They then perform RDP brute force attacks against new targets within the network, allowing them to move laterally. Finally, they perform credential theft, deploy cryptomining malware, and deliver the final ransomware payload.
Parinacota operators also exhibit in-depth knowledge about their targets, often changing the ransom payment that they ask for (which can vary from 0.5 to 2 Bitcoin) based on the likelihood of what the victim would pay due to impact to their company or the perceived importance of the target.
“Other malware families like GandCrab, MegaCortext, LockerGoga, Hermes, and RobbinHood have also used this method in targeted ransomware attacks,” said researchers. “Parinacota, however, has also been observed to adapt to any path of least resistance they can utilize. For instance, they sometimes discover unpatched systems and use disclosed vulnerabilities to gain initial access or elevate privileges.”
Commodity Malware
Another characteristic of human-operated ransomware campaigns is that they often start with “commodity malware,” like banking trojans. These attack vectors are viewed as “unsophisticated” and tend to be triaged as unimportant and therefore not thoroughly investigated and remediated, researchers said – allowing the ransomware operators to evade defenders.
This technique has proved successful for the Ryuk ransomware, most recently seen in an attack this past weekend hitting Epiq Global, which caused the legal services company to take its systems offline globally, according to a report this week by legal news site LawSites. Media reports said that the attack started with the TrickBot malware infecting a computer on Epiq’s system in December. After TrickBot was installed, it reportedly opened a reverse shell to the Ryuk operators, allowing them to access the network devices and encrypting files on infected computers.
The DoppelPaymer ransomware (recently seen in attacks that have stolen data from a supplier to SpaceX and Tesla) also makes use of commodity malware as an initial infection vector, using the Dridex malware in early attack stages (via fake updaters, malicious documents in phishing email) and later delivering Doppelpaymer on machines in affected networks. The Dridex banking trojan, which has been around since 2011, comes equipped with obfuscation capabilities, helping it skirt anti-virus detection.
“Investigators have in fact found artifacts indicating that affected networks have been compromised in some manner by various attackers for several months before the ransomware is deployed, showing that these attacks (and others) are successful and unresolved in networks where diligence in security controls and monitoring is not applied,” said researchers.
Improving Defenses
Researchers said that preventing these types of ransomware attacks requires a shift in mindset. Defense teams need to focus on “comprehensive protection required to slow and stop attackers before they can succeed,” they said.
“Human-operated attacks will continue to take advantage of security weaknesses to deploy destructive attacks until defenders consistently and aggressively apply security best practices to their networks,” they said.
To keep up, defense teams need to better integrate IT pros into security teams, because attackers are preying on settings and configurations that many IT admins manage and control. Security teams need to also address the infrastructure weakness that initially let attackers in, because ransomware groups routinely hit the same targets multiple times. Also, security teams need to understand that seemingly rare, isolated or commodity malware alerts can indicate new dangerous attacks unfolding.
“If these alerts are immediately prioritized, security operations teams can better mitigate attacks and prevent the ransomware payload,” said researchers. “Commodity malware infections like Emotet, Dridex, and Trickbot should be remediated and treated as a potential full compromise of the system, including any credentials present on it.”
Interested in security for the Internet of Things and how 5G will change the threat landscape? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.