Researchers are warning of a new Android ransomware being spread via links in online forums and SMS messages. The malicious links purport to connect back to a sex simulation game, but in reality lead to ransomware that encrypts victims’ files.
The Android ransomware, dubbed Android/Filecoder.C, has been active since at least July 12, when researchers found it via two domain links. These links were distributed primarily on online forums, including via Reddit in posts that were porn related, or via a forum for Android developers called “XDA Developers” in posts relating to technical topics.
“Using victims’ contact lists, it spreads further via SMS with malicious links. Due to narrow targeting and flaws in execution of the campaign, the impact of this new ransomware is limited,” said Lukas Stefanko with ESET in a Monday analysis of the ransomware. “However, if the operators start targeting broader groups of users, the Android/Filecoder.C ransomware could become a serious threat.”
In addition to online forums, researchers found the malicious links being spread via SMS messages. Once the victim is infected, the ransomware also sends malicious links of the domains via SMS messages to the victim’s contact list. These SMS messages add some level of urgency and personalization to con the contacts to open them, as they use the contact name listed in the SMS message, and tells the contact that their photos are being used in the sex simulation game.
“These messages include links to the ransomware; to increase the potential victims’ interest, the link is presented as a link to an app that supposedly uses the potential victim’s photos,” said Stefanko.
Targets are sent a link to the malicious application, which must be installed manually by victims. After the app is launched, it displays whatever is promised via the posts distributing it – most often, the sex simulator online game.
But behind the scenes, the ransomware is activated, launching command-and-control communication, spreading the malicious messages to victims’ other contacts and implementing an encryption-and-decryption mechanism.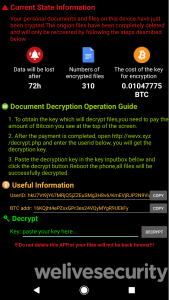
The ransomware encrypts various filetypes – including DOC, PPT, JPEG and others. That said, the malware leaves files unencrypted if the file extension is .zip or .rar and the file size is over 51,200 KB/50 MB. Also, JPEG, JPG and PNG files with a file size less than 150 KB are also not encrypted.
After encrypting victims’ files, the ransomware displays a ransom note in the app asking for a payment in Bitcoin. The ransom note warns that data will be lost after 72 hours, and that the files will not be decrypted even if the app has been deleted.
“It is true that if the victim removes the app, the ransomware will not be able to decrypt the files, as stated in the ransom note,” said researchers. “Also, according to our analysis, there is nothing in the ransomware’s code to support the claim that the affected data will be lost after 72 hours.”
While researchers don’t say how many have been infected, in inspecting one such bit.ly link spread on Reddit, Stefanko said that it had reached 59 clicks from various sources and countries.
Researchers urged Android victims to avoid attack by keeping devices up to date and sticking to Google Play for downloading apps. Android devices face a slew of threats: A new recent breed of Android malware, dubbed “Agent Smith,” has infected 25 million handsets in order to replace legitimate apps with doppelgangers that display rogue ads, researchers have said. Researchers have also spotted a mobile surveillance-ware remote access trojan for Android called Monokle, using novel techniques to exfiltrate data.











