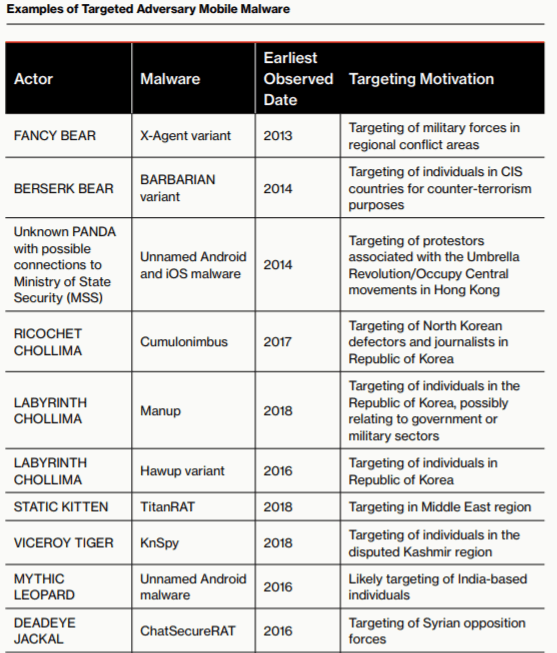
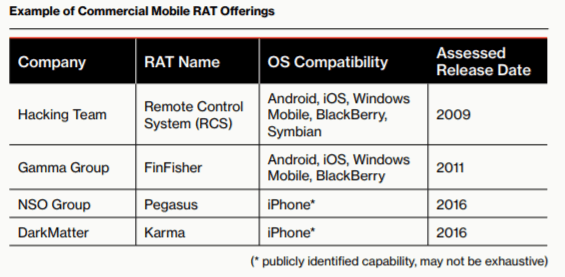
APTs, including a range of nation-state groups operating in China, North Korea, Pakistan and Russia, are shifting their malware development focus to target mobile users for intelligence gathering, financial gain and disruption of national rivals.
That’s according to CrowdStrike’s Mobile Threat Landscape Report, which found that targeted adversary groups continue to develop sophisticated mobile malware variants, typically as offshoots of established desktop malware families.
“A number of targeted intrusion adversaries have begun developing mobile malware as part of their overall operational tool kit,” according to the report, released Tuesday. “Often these implementations are mobile ports of malware originally developed for desktop computers, and therefore share commonalities, including general capabilities and C2 protocols.”
Meanwhile, CrowdStrike said that sophisticated mobile RATs are also available to these types of attackers via commercial services. However, remote software exploits or physical access to the devices is often required to install these RATs, so these are usually supported by professional device exploitation operations and C2 infrastructure administration services.
“The high cost of developing and running such operations make these capabilities best suited for nation-state customers,” according to the report. “Although some deployment operations of this type may involve using zero-day exploits to silently install their malware on target devices, some groups also take the more traditional route of packaging their malware to make it seem legitimate.”
For example, the group behind the Exodus malware registered with Apple as an enterprise developer, using the identity of a possible cover company called Connexxa to distribute a version of their malware for iOS devices.
Commercial RATs also tend to have broader capability than bespoke code, the report added.
“Apart from the full operational management chain, what distinguishes these companies from other mobile RAT developers is their continual maintenance and patching of their malware, as well as producing variants written for non-Android operating systems such as Apple iOS,” according to the report. “While the Apple mobile ecosystem is not immune to malicious software, there are barriers to the development and deployment of potentially malicious software that complicate the typical deployment techniques often employed to install Android-based RATs.”
The firm said that the shift to specifically targeting mobile users reflects the fact that even though mobile data security is less mature than its desktop equivalent, the quality of the information on offer is top-tier.
“The initial development and increased distribution of mobile malware in recent years appears as a tacit acknowledgement by a range of malicious actors of…the utility of mobile devices as a source of intelligence or financial gain,” according to the report. “The installation of RAT malware on mobile devices provides access to a large amount of high-resolution victim data.”
That includes device information, contact information, email and messaging content, files and attachments, pictures and video, audio recordings and geolocation information.
This broad range of information can also help with follow-on attacks, according to CrowdStrike.
“For example, 2FA tokens may be intercepted to provide remote access to cloud-based services such as email accounts, while access to IMEI and IMSI numbers could potentially allow for alternative target correlation and data collection using indigenous signals intelligence (SIGINT) programs operated by sophisticated state actors,” the report noted.
Mobile malware is also becoming more attractive of a tool thanks to ever-increasing scrutiny of desktop machines by security products, according to the firm.
“[This] is likely to lead to further investment in the development of mobile RATs, particularly by targeted threat actors who seek to maintain access to their victims for extended periods of time…[and] particularly by actors who require tracking their victim’s physical location via GPS telemetry, or who focus on specific geographic regions.,” CrowdStrike said. “State actors with SIGINT [signals intelligence] collection missions are also likely to invest in the creation of mobile malware as a solution to the increased adoption of encrypted network communications across email, web and messaging services, as access to a mobile endpoint will provide opportunities to subvert this trend.”
Interested in more on patch management? Don’t miss our free Threatpost webinar, “Streamlining Patch Management,” now available on-demand. Please join Threatpost editor Tom Spring and a panel of patch experts as they discuss the latest trends in Patch Management, how to find the right solution for your business and what the biggest challenges are when it comes to deploying a program. Click here to listen (registration required).