An independent analysis of the so-called Anti Public Combo List, a dump of 562 million breached usernames and passwords, reveals a privacy silver lining. Hard to imagine, but according to an analysis of the data by Duo Labs researchers, consumers are slowly adopting safer password habits.
The Anti Public Combo List is a massive database of email addresses and password pairs that have been pieced together over the past several years from various unrelated breaches and data leaks. Late last week, breach notification service HaveIBeenPwned? found the list along with a second one on the dark web of more than 593 million, adding more than one billion new email addresses and passwords to the repository.
Security expert Troy Hunt, who runs HaveIBeenPwned?, said the lists have been passing hands between hackers since December 2016. The Anti Public Combo List, according to Hunt, has been marketed by criminals at $5 for 10,000 valid user names and passwords, $20 for 50,000 and $70 for 210,000. The massive list is a combination of breaches ranging from Adobe, Dropbox, LinkedIn, Yahoo, VerticalScope and many others.
“While Troy’s focus was on the legitimacy of the data, we built off his research and focused on what the user names and passwords said about their owners and the services they were tied to,” said Kyle Lady, senior R&D engineer at Duo Labs. “From what we can tell, people appear to slowly be heeding the advice of security professionals and are creating more sophisticated passwords,” Lady said.
According to Duo’s analysis of the data, 70 percent of passwords had at least one number. This is an improvement over previous bad passwords that used just six-character lower-case dictionary words that could easily be cracked using brute force attacks, Lady said.
But Lady said, password improvements have less to do with users’ adopting stronger security habits and more to do with more stringent password requirements by the sites.
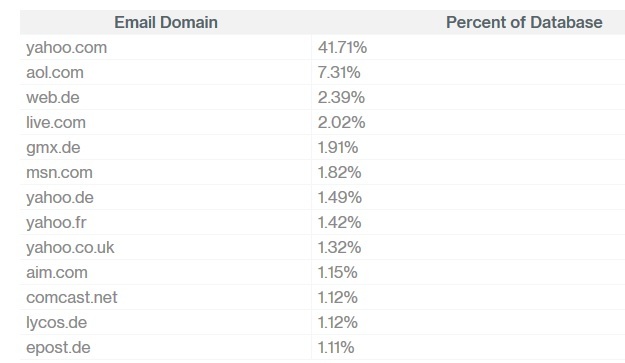
Of the breached sites that made up the 562 million user name and password pairs examined by Duo, 42 percent of usernames end in Yahoo.com and 7 percent end in AOL.com, suggesting most emails were tied to consumers. “We found that only about 1 million (1.7 percent) of the accounts in the dump were from domains of large companies,” Duo Labs wrote in its breakdown of the database posted Thursday.
Focusing on password strength, Duo Labs wrote “passwords in this dump follow an exponential long-tail distribution in terms of length, peaking at nine characters at 27 percent and falling under 1 percent after 14 characters.”
Besides 70 percent of passwords having at least one number, only 6 percent and 4 percent of passwords contain at least an uppercase character or a symbol, respectively. “A surprisingly low result was for the space character, which is allowed by many systems, but was only present in 0.03 percent of passwords examined,” researchers noted.
Duo researchers said this suggested that attackers might be less likely to include spaces in their set of search character when trying to crack a password. “Users would be wise to keep in mind that spaces can often be valid password characters when choosing,” they wrote.
Researchers say the Anti Public Combo List appears to be a collection of individual password dumps. “It’s likely that the breach in question resulted in the theft of hashes instead of cleartext passwords. When this happens, attackers will try to crack as many passwords as possible, leaving the hashes in place for those they couldn’t quickly crack,” they wrote.
The good news Lady said is that there was a meaningful portion of Anti Public Combo List breached users names with passwords that couldn’t be cracked. “It took us this long for 70 percent of people to start using a digit in their password. Next, is it too unreasonable to start adding uppercase characters and a symbol?”