Nearly five years after the high-profile Ashley Madison data breach, hundreds of impacted website users are being targeted by a new extortion attack this past week.
The 2015 data breach of the adultery website led to 32 million accounts being publicly dumped online, including victims’ names, passwords, phones numbers, credit card information and more. Up to a year after the hack, researchers with Kaspersky said that affected users were still being hit with an array of attacks, from credit card scams to spam emails.
Now, cybercriminals are exploiting the treasure trove of breached Ashley Madison data again in a new highly-personalized and targeted attacks. According researchers at Vade Secure, extortionist are sending emails targeting affected Ashley Madison users once again.
“In the last week, Vade Secure has detected several hundred examples of this extortion scam, primarily targeting users in the United States, Australia, and India,” said Ed Hadley with Vade Secure in a Friday post. “Seeing that more than 32 million accounts were made public as a result of the Ashley Madison data breach, we expect to see many more in the coming weeks. Moreover, like sextortion, the threat itself will likely evolve in response to tweaks by email security vendors.”
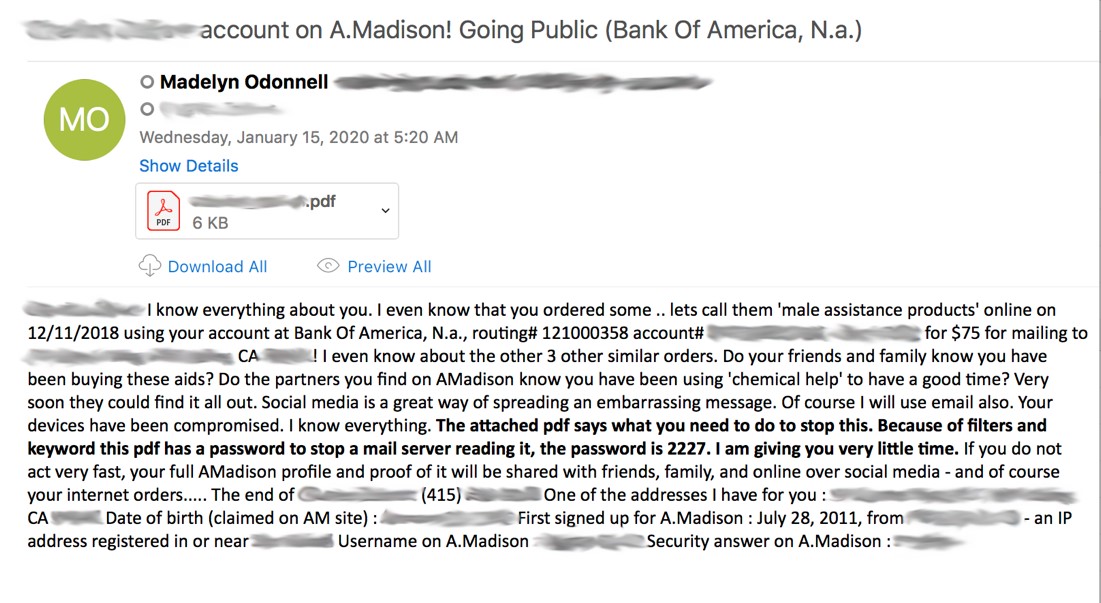
Victims are receiving emails threatening to expose their Ashley Madison accounts – along with other embarrassing data – to family and friends on social media and via email, unless they pay a Bitcoin ransom (which, in the sample email below, totaled around 0.1188 Bitcoin, or $1,059).
Researchers said these emails are highly personalized with information from the Ashley Madison breach – including the affected users’ names, bank account numbers, telephone numbers, addresses, and birthdays, as well as Ashley Madison site info such as the signup dates and answers to security questions.
In addition to the shame associated with being an adulterous website user, researchers said that cybercriminals also leverage embarrassing previous purchases supposedly made by victims. One of the emails (above) even references previous purchases for “male assistance products,” and says “Do the partners you find on AMadison know you have been using ‘chemical help’ to have a good time?'”
The body of the emails then refers to an attached, password protected PDF, which “says what you need to do to stop this.” This PDF includes additional info from the Ashley Madison data breach, including when the recipient signed up for the site, their user name, and even interests they checked on the site when seeking an affair. It also contains the ransom demand.
“What’s interesting about this extortion scam is that the financial demand isn’t made in the email body itself, but rather a password-protected PDF attachment,” said researchers. “As the email itself acknowledges, this is done to avoid detection by email filters, many of which are unable to scan the contents of files and attachments.”
 The PDF file also includes a QR code, for victims who are using a compatible mobile payment app to scan and make the payment.
The PDF file also includes a QR code, for victims who are using a compatible mobile payment app to scan and make the payment.
While the PDF tells victims that the QR code is an option “if you do not want to type the address,” researchers say that the QR code is a common phishing technique that is used to avoid detection by URL scanning or sandboxing technologies. That’s because many email filters do not feature detection tools for QR code technology, they said.”
“Lastly, like other phishing and scam emails, this attack creates a sense of urgency, setting a deadline of six days (after the email was sent) for the Bitcoin payment to be received in order to avoid having the recipient’s Ashley Madison account data shared publicly,” said researchers.
Sextortion-related scams are an easy way for cybercriminals to make money via ransom payments – and they’re getting better at evading detection, using new distribution techniques and shifting their “scare” tactics. However, researchers say that this attack points to cybercriminals utilizing actual data from previous breaches in extortion scams – a trend they believe will proliferate in 2020.
“This Ashley Madison extortion scam is a good example that a data breach is never one and done,” said Hadley. “In addition to being sold on the dark web, leaked data is almost always used to launch additional email-based attacks, including phishing and scams such as this one. Seeing that there were more than 5,183 data breaches reported in the first nine months of 2019, exposing 7.9 billion records, we expect to see a lot more of this technique in 2020.”