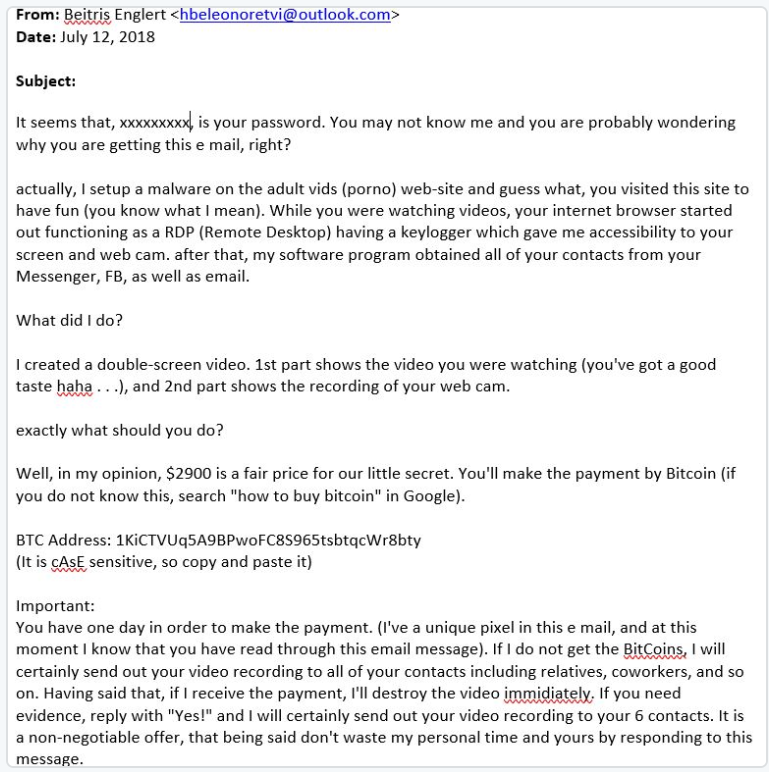
A fresh take on the classic sextortion scam is making the rounds, with several reports confirming a new wrinkle in approach: The inclusion of a legitimate password in the email for the campaign.
Multiple end users have received scam email messages from actors claiming to have taken over the targets’ webcams to record a video of the person watching porn. As with previous sextortion efforts, the fraudster also threatens to send a copy of the video to all contacts – unless, of course, a Bitcoin ransom is paid within 24 hours (in this case, the demand is $1,400).
Of course, the threat actor hasn’t recorded a video, hasn’t compromised the computer, and has no access to contact lists. The effort strictly relies on people falling for scare tactics – and these kinds of fraud efforts are something that more and more consumers are copping onto. But as the average citizen becomes savvier in the ways of email spam-scams, attackers are looking for ways to increase their hit rate by making the mails more convincing.
“Scammers generally have a very low success rate,” Brian Contos, CISO at Verodin, told Threatpost. “That low success rate is okay, however, because cyber-scams are a volume business. Even if only 1 percent of targets in a scam respond to a campaign aimed at, let’s say, only 10,000 individuals, that’s still 100 people sending the scammer a pile of Bitcoins. This isn’t a bad return when you consider the level of effort required and the level of risk for the scammer.”
The new crop of messages shows an evolution in tactics: The emails offer, as proof of compromise, a password associated with the target’s online accounts. In a copy of the email posted by a white-hat researcher who goes by SecGuru on Twitter, the opening line is: “It seems that, [password], is your password. You may not know me and you are probably wondering why you are getting this e mail [sic], right?”
Brian Krebs said that he received reports from various recipients that these passwords were indeed legitimate in the sense that they had once been used with an account — but in all of the cases, the passwords were almost a decade old. This was echoed by others posting in various forums as well.
In all probability, the sextortionists have gained access to a cache of password/email combinations from a previous data breach, and are leveraging the information for their own purposes; SecGuru, posting on Twitter, said that the password in the email that he gained access to came from LeakForums, which is a sort of social network and marketplace for swapping information on various leaks.
The passwords could also come from a successful website breach, but given the age of some of them, this seems less likely.
In any event, it’s unlikely that sextortion campaigns will wane anytime soon, but will rather continue to evolve.
“Sextortion, in its varied forms, has been used by malicious actors for some time now due to the hyper-emotional targeting of the victim,” Aaron Higbee, CTO and co-founder of Cofense, told Threatpost. “Whether the malicious actor is demanding nude photos from the victim, as seen with the nRansomware threat, or in this case scaring the victim into thinking their use of adult content on the web has been recorded and in the hands of a stranger, leveraging such a taboo subject as this allows malicious actors to hit a sensitive nerve in people keen to protect their reputation and keep their private life private.”
Higbee added, “Regardless of the type of extortion methods used, phishing isn’t a threat that anyone should take lightly. With so much ransomware being delivered via phishing emails, it’s essential that organizations and individuals are conditioned to recognize and most importantly report phishing attempts that bypass perimeter controls in order for incident responders to effectively analyze and remediate the threat before damage occurs.”