 Bot herders and the crimeware gangs behind banker Trojans have had a lot of success in the last few years with using bulletproof hosting providers as their main base of operations. But more and more, they’re finding that social networks such as Twitter and Facebook are offering even more fertile and convenient grounds for controlling their malicious creations.
Bot herders and the crimeware gangs behind banker Trojans have had a lot of success in the last few years with using bulletproof hosting providers as their main base of operations. But more and more, they’re finding that social networks such as Twitter and Facebook are offering even more fertile and convenient grounds for controlling their malicious creations.
New research from RSA shows that the gangs behind some of the targeted banker Trojans that are such a huge problem in some countries, especially Brazil and other South American nations, are moving quietly and quickly to using social networks as the command-and-control mechanisms for their malware. The company’s anti-fraud researchers recently stumbled upon one such attack in progress and watched as it unfolded.
The attack is as simple as it is effective. It begins with the crimeware gang setting up one or more fake profiles on a given social network (RSA isn’t naming the network on which it saw this specific attack). The attacker then posts a specific set of encrypted commands to the profile. When a new machine is infected with the banker Trojan, the malware then goes out and checks the profile for new commands. The specific command in this case begins with a string of random characters that serves as an authentication mechanism of sorts, letting the Trojan know it’s found the right commands.
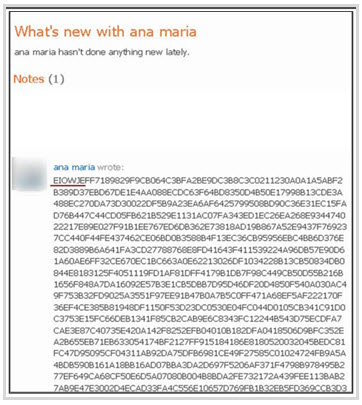
The rest of the encrypted string are hard-coded instructions telling the Trojan what to do next, whether it’s to look for other machines on the network, search for saved data or log keystrokes when the user visits a specific online banking site.
This certainly is not the first example of this kind of activity on social networks. There have been botnets controlled via Twitter for at least a year now, and researchers have found a number of example of Facebook profiles set up specifically for malicious activity. But this is one of the results of the success that researchers and law enforcement have had in recent years in shutting down the bulletproof hosting providers who have been harboring botnet C&C servers and Trojan drop zones for a long time.
“The most interesting thing is that it’s part of a growing trend. These groups have had four main options for hosting if they want to put it in a resilient infrastructure,” said Uri Rivner, head of new technologies–consumer identity protection at RSA, the security division of EMC. “You can build your own, and there are some that are very sophisticate with great disaster recovery, but that’s expensive. You can go with bulletproof hosting, but that’s getting harder. You can use cloud services, which we’ve seen some of lately. Or you can now use social networks. That’s getting more popular because resilience is they key for some of these Trojans that can run for months or years. It’s so important to them to find a good hosting environment.”
[block:block=47]
The other thing that makes networks such as Twitter and Facebook attractive for bot herders and Trojan gangs is the ease with which they can set up new profiles. The profiles themselves essentially become disposable, because the attackers can code a list of dozens or hundreds of such profiles into the Trojan and if one is discovered and taken offline, the malware move on to the next one. It’s also quite difficult for the operators of these sites to identify and block these profiles quickly enough, making them soft targets for the attackers.
“The only downside for the attackers is if the companies start fighting back against it, but that’s hard,” Rivner said. “This is the easiest, the cheapest and most reliable infrastructure that I see.”









