BitTorrent today announced that a patch has been rolled out in the libuTP protocol used by many of its clients, fixing a vulnerability that allows attackers to carry out distributed reflective denial of service attacks.
The issue was revealed in a paper and presentation at the recent USENIX Security Symposium that described how BitTorrent clients could be unwitting participants in amplified DDoS attacks.
Christian Averill, vice president of communications at BitTorrent, told Threatpost that the fix had been rolled out as of Aug. 4, more than a week before the USENIX presentation.
The vulnerability was reported to BitTorrent on July 1 by City University of London research student Florian Adamsky. A number of BitTorrent clients that use the libuTP UDP-based protocol, including uTorrent, BitTorrent and BitTorrent Sync, were vulnerable to abuse.
“Many BitTorrent products make use of libµTP because it can detect network congestion and automatically throttle itself. This self-throttling characteristic makes BitTorrent, µTorrent and BitTorrent Sync friendlier to home networks,” BitTorrent said today on its engineering blog. “However, a flaw in the way libµTP handles incoming connections may leave many clients vulnerable to become unknowing accomplices in amplification attacks as reflectors.”
Adamsky’s work, assisted by PLUMgrid, Inc.’s Syed Ali Khayam, THM Friedberg’s Rudolf Jager, and another City University London student, Muttukrishnan Rajarajan, was tested in a controlled lab setting, and BitTorrent said it was theoretical and had not yet been seen in the wild.
The researchers built a test bed of more than 10,000 BitTorrent handshakes – two-way connections between uTP nodes.
Assuming they have a valid SHA-1 info-hash, the researchers claim libuTP could enable attackers to carry out attacks by using a spoofed IP address. In fact, attacks channeled through BitTorrent could be amplified up to 50 times. This includes those filtered through some of the more protocol’s more popular clients, such as uTorrent, Mainline and one of the biggest culprits, Vuze, which they found heightened attacks up to 54 times.
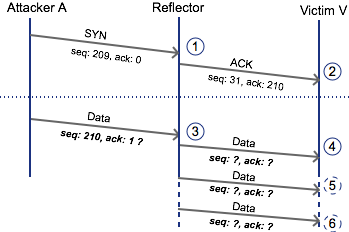
“uTP establishes a connection with a two-way handshake. This allows an attacker to establish a connection with an amplifier using a spoofed IP address, as the receiver does not check whether the initiator has received the acknowledgment,” the paper reads.
BitTorrent said that as of Aug. 4, uTorrent, BitTorrent and BitTorrent Sync clients were patched and will only transition to the connection state if they receive a valid acknowledgement from the connection initiator.
“This means that any packets falling outside of an allowed window will be dropped by a reflector and will never make it to a victim,” BitTorrent said. “Since the mitigation occurs at the libµTP level, other company protocols that can run over libµTP like Message Stream Encryption (MSE) are also serviced by the mitigation.”