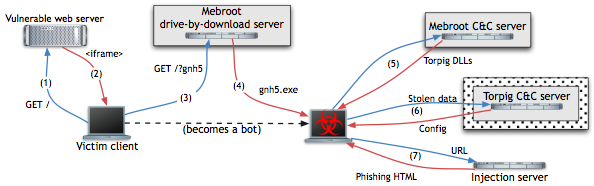
Security researchers at University of California, Santa Barbara have broken into the nerve center of the Torpig botnet (also called Sinowal or Mebroot) to find a ten-day stash of 10,000 bank accounts and credit card numbers worth hundreds of thousands of dollars.
During the botnet hijack [.pdf], the researchers exploited a weakness in the way the bots tried to locate their C&C servers and found an underground online crime operation collecting about 70GB of stolen data over just ten days.
Torpig is an interesting case study because of the sophisticated nature of the operation and the report is a must-read for anyone looking to understand the internals of a computer crime ring.
The botnet was built using a MBR (master boot record) rootkit that executes at boot time, before the operating system is loaded. Once a machine is infected, the malware harvests and uploads data in 20-minute increments. The stolen data includes e-mail accounts, Windows passwords, FTP credentials and POP/SMTP accounts.
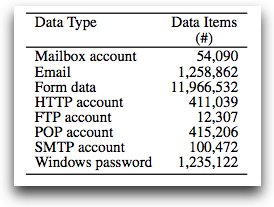
And, of course, financial data:
In ten days,Torpig obtained the credentials of 8,310 accounts at 410 different institutions. The top targeted institutions were PayPal (1,770 accounts), Poste Italiane (765), CapitalOne (314), E*Trade (304), and Chase(217).
And credit card numbers:
We extracted 1,660 unique credit and debit card numbers from our collected data. Through IP address geolocation, we surmise that 49% of the card numbers came from victims in the US, 12% from Italy, and 8% from Spain, with 40 other countries making up the balance. The most common cards include Visa (1,056), MasterCard(447), American Express(81), Maestro(36), and Discover (24).
While 86% of the victims contributed only a single card number, others offered a few more.
Of particular interest is the case of a single victim from whom 30 credit card numbers were extracted. Upon manual examination, we discovered that the victim was an agent for an at-home, distributed call center. It seems that the card Numbers were those of customers of the company that the agent was working for, and they were being entered into the call center’s central database for order processing.
The report surmises that the criminal gang behind Torpig pocketed between $83,000 $8.3 million in profit over a 10-day period.
For more on the botnet hijack, check out UC Santa Barbara’s Torpig project page. More at Slashdot.









