A botnet comprised entirely of internet-enabled closed circuit TV devices used a barrage of HTTP requests to knock a small jewelry store offline for days.
Researchers who came across the botnet recently said they weren’t surprised that IoT devices were being used to carry out a distributed denial of service attack but were caught off guard that it was able to sustain itself for so long and use more than 25,000 CCTV devices in order to do so.
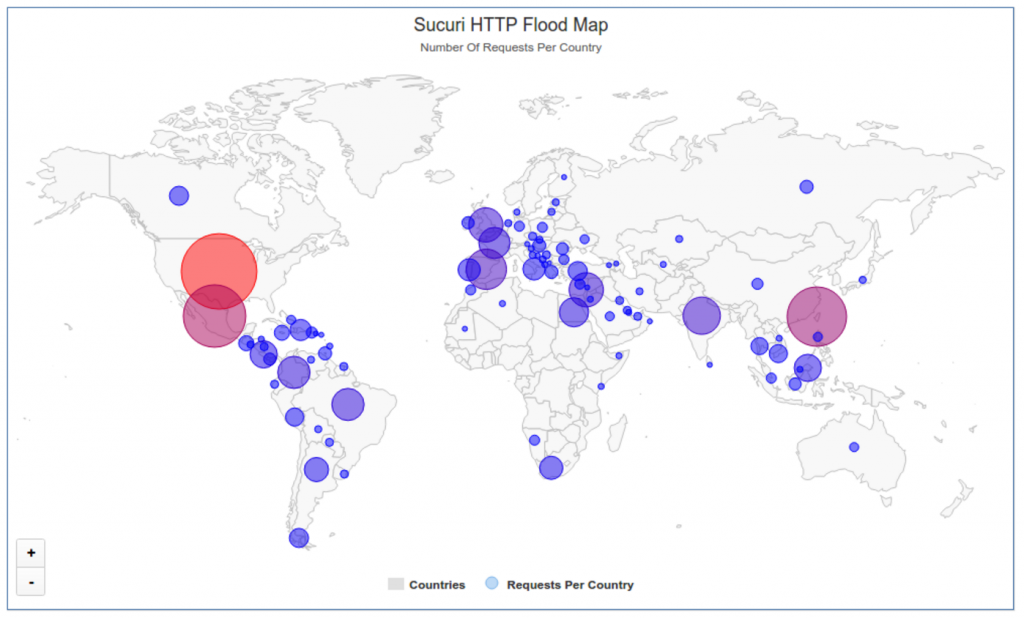
Researchers with Sucuri first noticed the store, one of their clients, was being hit with a layer 7 HTTP flood attack that generated 35,000 HTTP requests a second. The researchers saw an uptick in requests coming from a subsequent attack, one that ramped up to 50,000 requests a second soon after, and prompted Sucuri to look further into the source.
It was after that they observed 25,513 different IP addresses – most of them based in Taiwan – generating a DDoS attack over the course of just a couple of hours, according to Daniel Cid, Founder and CTO of Sucuri, who wrote about the botnet on Monday.
The rest of the IP addresses were primarily scattered across Indonesia, Mexico, Malaysia, and Israel, but after researchers broke down its geographic distribution, they discovered the botnet actually relied on IP addresses from 100+ countries worldwide. As researchers continued to look into it they discovered the crux of the botnet’s traffic was emanating from devices running Cross Web Server, a type of software that figures into several types of CCTV DVRs.
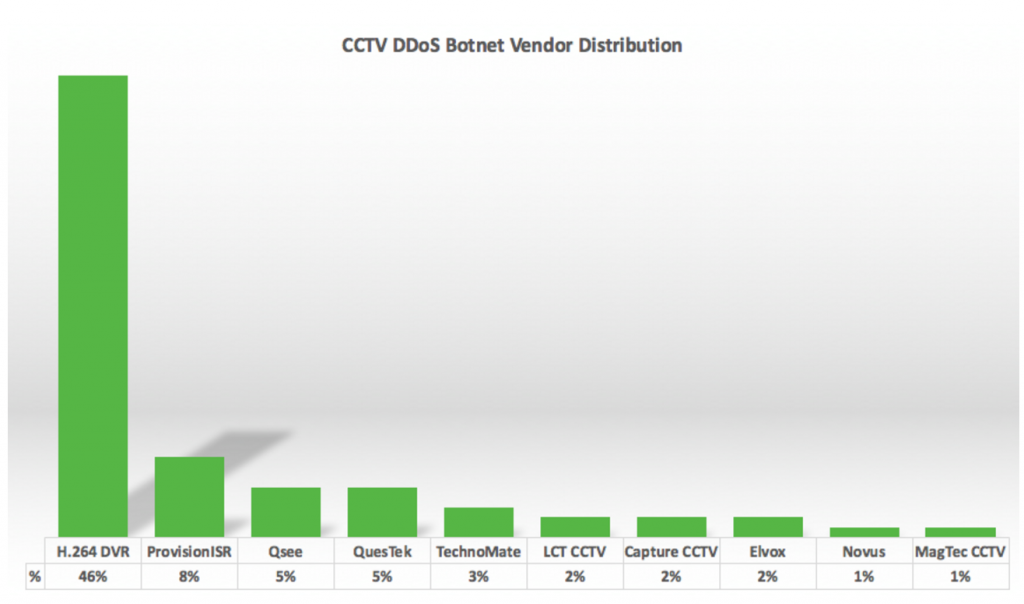
The bulk of the devices, 46 percent, are H.264 Network Digital Video Recorders. Other devices include CCTV boxes manufactured by an Israeli company, Provision-ISR, a device manufacturer sold in Home Depot and Costco stores, Q-See, and a manufacturer based in Vietnam, Questek, Sucuri claims.
Cid said Monday that all of the devices run on BusyBox, a software that provides Unix tools in a single executable file and can be run in Linux, Android, and FreeBSD.
Cid hinted at, but said its uncertain whether there’s a connection between the botnet and a remote code execution vulnerability discovered in March that affects DVR boxes made by 70 different CCTV vendors. Devices by Provision-ISR, Q-See, and Questek were all listed as vulnerable to the RCE vulnerability at the time but Cid claims the connection is unconfirmed at this point.
With that in mind, it’s unlikely the CCTV devices will get patched anytime soon. Even once they are, attackers will simply move onto the next one, Cid claims.
“Unfortunately, as website owners, there is not much you can do to get those 25,000+ CCTVs fixed and protected,” You also can’t do much to fix the millions of vulnerable devices on the internet that can be used as botnets and DDoS amplification methods,” Cid wrote.
“… that’s just one small piece of the problem,” Cid said, “Once the cameras are patched, the attackers will find other easily hacked devices for their botnets.”
Cid claims his company is in the middle of contacting networks that have the compromised cameras. In the meantime, he insists that users should at the least ensure that if they own one of the devices, that they’re patched and isolated from the internet.
Researchers with Incapsula last fall detected a similar, although less intense, CCTV-fueled botnet. One of the company’s clients was also hit by a series of HTTP flood attacks, these ones toppling out at around 20,000 requests per second, from about 900 CCTV cameras worldwide. Like the DVRs Sucuri reviewed, all of the compromised devices were running BusyBox. In that instance however the malware inside actively searched for open Telnet/SSH services that were susceptible to brute force dictionary attacks.