Hundreds of thousands of web visitors continue utilizing passwords that have previously been compromised. Worse, they are reusing the breached credentials for some of their most sensitive financial, government and email accounts.
That’s according to a new Google study released this week, which was based on data collected from Google’s Password Checkup Chrome extension. The study found that 1.5 percent – or 316,000 users – of website logins on the browser are utilizing already-hacked passwords.
“Protecting accounts from credential stuffing attacks remains burdensome due to an asymmetry of knowledge: attackers have wide-scale access to billions of stolen usernames and passwords, while users and identity providers remain in the dark as to which accounts require remediation,” researchers said in a research paper titled “Protecting accounts from credential stuffing with password breach alerting,” released at USENIX this week.
The Password Checkup extension, launched in February 2019, is meant to keep online accounts safe from hijacking by displaying a red “warning” box to users when they sign on to a site using one of the 4 billion usernames or passwords that Google knows has been breached.
Not changing already compromised passwords opens up users to various risks. One of the biggest risks is credential stuffing, where cyberattackers use stolen passwords and user names from previous data breaches to brute-force accounts on a wide scale, and when a match is found, take over the victim’s account. This has recently seen in action in cyberattacks against State Farm and Dunkin Donuts.
Anonymous telemetry reported by the extension revealed that users were reusing breached credentials on over 746,000 distinct domains. The risk of hijacking was the highest for video streaming and porn websites, researchers said; where up to 6.3 percent of users were logging in using breached credentials.
On the other hand, only 0.2 percent of logins on financial and government sites relied on breached credentials. Researchers surmised that this was because these users appeared to internalize password security advice or at least were forced to do so via password composition policies.
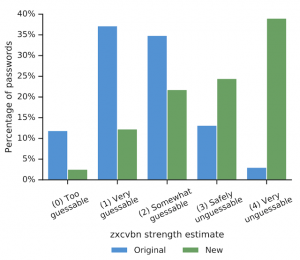 Worse, only about 26 percent of the extension’s warnings actually resulted in users migrating to a new password that was at least as strong as the original, according to Google.
Worse, only about 26 percent of the extension’s warnings actually resulted in users migrating to a new password that was at least as strong as the original, according to Google.
“Despite variations across industries, our analysis reveals that the threat of credential stuffing extends well into the long tail of the Internet,” said researchers. “Absent new forms of authentication, we believe that it is critical to democratize access to breach alerting so that both users and identity providers can proactively resecure their accounts.”
The good news is that the 1.5 percent of users keeping breached passwords is actually significantly lower than previous figure reported by a 2017 Google study, which said that 6.9 percent of users were using previously-compromised credentials.
Google said that simply updating passwords are an easy way to avoid hackers: According to the study, 60 percent of new passwords are secure against guessing attacks—meaning it would take an attacker over a hundred million guesses before identifying the new password.
The big “password problem” has plagued the security industry for years. Poor password hygiene, including reusing passwords or picking easy-to-guess passwords, is greatly exacerbating many of the major issues that plague the cybersecurity landscape, researchers like Troy Hunt have said in the past.
Making matters worse, passwords are appearing left and right online as part of major data breaches – yet victims aren’t changing their passwords at all across various platforms. The Collection #1 data dump, which included 773 million credentials, and subsequent Collection #2-5 dumps, show exactly how many passwords are available on the Dark Web and underground forums.
Many users are still careless with their passwords and need to become better educated about regularly changing up passwords, Felix Rosbach, product manager with comforte AG, said in an email.
“As private individuals, there’s no way to be sure that the websites and services we use safeguard our usernames and passwords by an adequate amount of security,” He said. “The best way to protect yourself is to use different passwords for all your online accounts and change them regularly. Otherwise, if one is compromised, then you can assume they’ve all been compromised.”
Interested in more on the internet of things (IoT)? Don’t miss our free Threatpost webinar, “IoT: Implementing Security in a 5G World.” Please join Threatpost senior editor Tara Seals and a panel of experts as they offer enterprises and other organizations insight about how to approach security for the next wave of IoT deployments, which will be enabled by the rollout of 5G networks worldwide. Click here to register.