A researcher earned a double-payment totaling $10,000 for a cross-site scripting (XSS) bug he found in Google Maps. He earned $5,000 initially. But when Google’s patch fell short, the researcher earned a second $5,000 for discovering the bypass to the fix.
Zohar Shachar, head of application security at Wix.com, reported the flaw to Google on April 23 and was issued a $5,000 reward soon after. Google publicly disclosed the issue, declaring it “fixed” on June 7. Minutes after Shachar was notified of the patch and bounty payment award, he said he found a bypass for the Google Maps fix. That eventually earned him another $5,000.
“Something in the boredom of this particular moment led me to overcome my initial mindset of ‘this is Google, they know how to fix an XSS’, and actually try and validate the fix. Within 10 minutes of that, I had a bypass in hand, and a few days later a double bounty in my account,” wrote Shachar in blog post Sunday breaking down the flaws for the first time publicly.
The initial vulnerability stemmed from a Google Maps function that allows users to create their own map, said Shachar. After building the map, users can export it in several formats. One of those formats is Keyhole Markup Language (KML), an XML-like format for expressing geographic annotation and visualization within 2D maps.
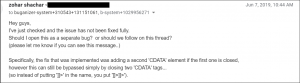
When the map was exported as KML, Shachar found the server response contained a CDATA tag. CDATA tags indicate that a certain portion of the document is general character data (rather than non-character data) and makes sure that the code wouldn’t be rendered by the browser. However, he found that by adding special characters, the CDATA tag can be easily “closed.”
“Specifically, by adding ‘]]>’ at the beginning of your payload (I.e. as the beginning of the ‘map name’), you can escape from the CDATA and add arbitrary XML content (which will be rendered as XML) – leading immediately to XSS,” said Shachar.
To exploit this flaw, an attacker could create a new empty map, rename it using these special characters and add an XSS payload for SVG. SVG (or Scalable Vector Graphics) is an XML-based vector image format. Then, they need to set permissions for the map to “public,” allowing everyone to access it, export it as KML and copy the download link. They can then send the download link to their victim. Once the target is persuaded to click on the link (via social engineering) the XSS attack is launched.
After Shachar reported the bug, Google said it was fixed. However, Shachar then discovered a way to bypass the patch. That’s because in order to fix the flaw, Google appeared to have added an additional CDATA tag – meaning an attacker could merely add two CDATA closing tags, said Shachar.
“I was genuinely surprised the bypass was so simple. I reported it so quickly (literally 10 minutes between checking my mailbox and reporting a bypass), that right after sending this mail I started doubting myself,” said Shachar.
Threatpost has reached out to Google for further comment.
Google has continually expanded its bug-bounty programs. The tech giant recently increased the reward amounts in its bug-bounty program for reports focusing on potential attacks in the product-abuse space, to top out at $13,337 per report.
Last year Google debuted the Developer Data Protection Reward Program, which offers up to $50,000 for reports on violations of the Google Play, Google API and Google Chrome Web Store Extension program privacy policies. Also in 2019, Google tripled top reward payouts for security flaws in Chrome from $5,000 to $15,000 – and doubled the maximum reward amount for high-quality reports from $15,000 to $30,000.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Register today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.