Hackers behind the Carbanak criminal gang have devised a clever way to gain persistence on targeted systems to more effectively pull off financially motivated crimes. The technique involves creating a bogus instance of a Microsoft Windows app compatibility feature.
On Wednesday, Mandiant, FireEye’s incident response team, posted a technical description of the technique, which it first observed earlier this year. More specifically, researchers say the Carbanak group (also known as FIN7) leverages what are called shim databases. According to Mandiant, shim databases are part of Microsoft’s Windows Application Compatibility Infrastructure.
“Mandiant identified that the group leveraged an application shim database to achieve persistence on systems in multiple environments. The shim injected a malicious in-memory patch into the Services Control Manager (‘services.exe’) process, and then spawned a Carbanak backdoor process,” wrote co-authors of the report Matthew McWhirt, Jon Erickson and DJ Palombo, each researchers with Mandiant.
According to Microsoft, shim databases were created to help with incompatibilities between legacy Windows applications and newer versions of Windows. Within the context of the Windows Application Compatibility Infrastructure, shim databases are where API calls and other application attributes sit. These libraries exist to bridge a gap between older applications and a new OS.
Mandiant said this technique is being used by Carbanak to install a payment card harvesting utility for persistent access. “This was a departure from FIN7’s previous approach of installing a malicious Windows service for process injection and persistent access,” according to researchers.
The use of shim databases for malicious purposes has been discussed in the past, namely at both BruCon and BlackHat, Mandiant wrote. But those attacks scenarios have been hypothetical and now adversaries are using the technique in the wild.
According to researchers, FIN7 utilizes targeted phishing emails to gain an initial foothold within an environment. “Recently, Mandiant identified additional techniques that FIN7 leverages for their phishing lures, including using hidden shortcut files (LNK files) embedded in malicious DOCX or RTF files,” researchers wrote in an email interview with Threatpost.
One of the trickier aspects of using malicious shims, from an attacker’s point of view, is getting them installed and registered on the targeted OS, and instructing Windows when shims should be executed.
“To install and register the malicious shim database on a system, FIN7 used a custom Base64 encoded PowerShell script, which ran the ‘sdbinst.exe’ utility to register a custom shim database file containing a patch onto a system,” researchers wrote. “In addition, specific registry keys were created that correlated to the shim database registration.”
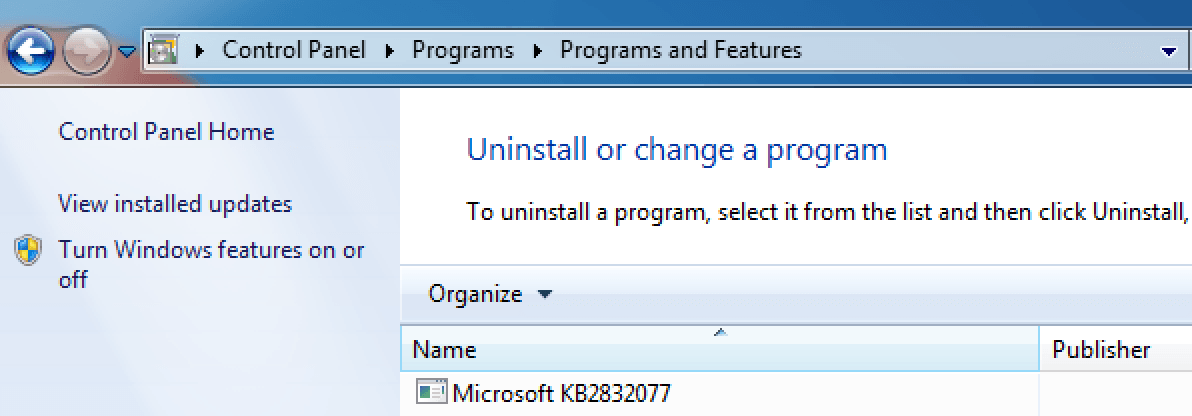
The database description used for the shim database registration is conveniently and covertly named “Microsoft KB2832077” – as in Knowledge Base patch.
“This description (see above) appeared in the listing of installed programs within the Windows Control Panel on the compromised system,” authors wrote.
During Mandiant’s analysis of malicious shims used in the wild, it said the Carbanak/FIN7 criminal group used a custom shim database to “patch” both the 32-bit and 64-bit versions of “services.exe” with their Carbanak payload.
“This occurred when the ‘services.exe’ process executed at startup. The shim database file contained shellcode for a first stage loader that obtained an additional shellcode payload stored in a registry key. The second stage shellcode launched the Carbanak DLL (stored in a registry key), which spawned an instance of Service Host (‘svchost.exe’) and injected itself into that process,” Mandiant wrote. Now the “services.exe” calls the function that executes the Carbanak payload stored in the registry.
Mitigation, Mandiant said, includes monitoring for new shim database files created in directories “C:\Windows\AppPatch\Custom” and “C:\Windows\AppPatch\Custom\Custom64”. Researchers also recommend monitoring process execution events and command line arguments for malicious use of the “sdbinst.exe” utility.