Researchers have linked Magecart Group 5, the credit-card skimming cybercriminals behind the Ticketmaster breach, to Dridex phishing campaigns and the infamous Carbanak group.
Magecart – which is an umbrella group encompassing several different affiliates all using the same modus operandi – injects malicious JavaScript that steals the data that shoppers enter into online payment forms, typically on checkout pages. The skimmer malware exfiltrates name, address, credit-card number, expiry date and CVV back to the criminals every time someone makes a purchase on one of the compromised stores.
Magecart 5 specifically targets the supply-chain used by e-commerce merchants; in the Ticketmaster attack for instance, it targeted a chat feature hosted by a third party. It’s a bang-for-the-buck strategy that potentially gives it access to hundreds or even thousands of websites downstream.
“This kind of supply-chain attack, where thousands of stores are loading altered code, have a much higher return than individually targeting stores,” explained researchers at Malwarebytes, in an analysis on Tuesday.
These higher-volume tactics result in attractive “scores” that have more in common with the tactics of advanced threat actors than your garden variety financially-motivated cybercriminal, according to the research. And sure enough, by examining a number of Magecart 5 domains and their ties with other malicious activity, researchers at Malwarebytes have made a link to just such actors.
“We see many compromises that affect a small subset of merchants that are probably tied to less sophisticated criminals, often using a very simply skimmer or a kit,” the researchers said. “In contrast, we believe that the bigger breaches that reel in a much larger prize are conducted by advanced threat groups with previous experience in the field and with very well-established ties within the criminal underground.”
It’s worth noting that Magecart 5 also uses a higher-end toolset, in the form of various libraries, analytics and fake “security seals” meant to reassure website visitors that the site is malware-free.
Links to Carbanak
Researchers found definite links to the Carbanak Gang (a.k.a. Cobalt), known for using the Carbanak custom backdoor to target internal banking infrastructure and ATMs. It’s also known for delivering the Dridex banking trojan via phishing campaigns. Europol has said that overall, the criminal operation has struck banks in more than 40 countries, resulting in cumulative losses of over EUR 1 billion for the financial industry. Its leader was nabbed in March 2018, but that hasn’t slowed down the group’s activity.
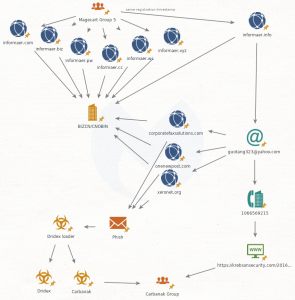
“We spent some time digging into a number of Magecart domains registered via the well-known Chinese registrar BIZCN/CNOBIN, [which is] essentially a bulletproof registrar,” Malwarebytes researchers said. “We narrowed down the domains to a smaller subset previously identified as being used by Magecart Group 5.”
While eight of the identified top-level domains were using privacy protection services, the group made an oversight when it came to one domain, informaer[.]info. The researchers were able to view the site’s registry data, which included name, address, contact information and more – all of which pointed to operators in Beijing.
“If we pivot from [the] email address, we can identify other domains, and in particular several that connect to Dridex phishing campaigns,” researchers explained. “Dridex is a robust banking Trojan that has been around for many years. To this day, it continues to be distributed via malicious spam campaigns using fake invoices.”
The guotang323@yahoo.com email address was used to register domains known to be used in previous Dridex campaigns, including a corporate eFax campaign targeting Germans and two phishing efforts spoofing the OnePosting and Xero accounting services.
The analysis points out that Dridex has been used in the past as an initial infection vector in attacks where delivering the Carbanak malware is the ultimate goal, used for lateral movement and conducting fraud.
“A diagram from Swiss CERT also shows how the Dridex loader does some victim triaging to either deliver Dridex proper (for consumers or low interest targets) or Carbanak for companies and high value targets,” according to the research.
Magecart consists of a dozen or more splinter groups, and its activity continues to ramp up. Recent analysis from RiskIQ identified almost 2 million (2,086,529) instances of Magecart’s JavaScript binaries, with over 18,000 hosts directly breached. The emergence of connections to sophisticated organized gangs is a new wrinkle.
“As Magecart activity increases and new groups emerge, it can sometimes be helpful to go back in time in order to examine bread crumbs that may have been left behind,” researchers said.
What are the top cybersecurity issues associated with privileged account access and credential governance? Experts from Thycotic on Oct. 23 will discuss during our upcoming free Threatpost webinar, “Hackers and Security Pros: Where They Agree & Disagree When It Comes to Your Privileged Access Security.” Click here to register.