Concerned global citizens making donations to help fight the massive Australia bushfires have been caught up in a Magecart attack, after one of the groups implanted a payment-card skimmer on the check-out page of a legitimate online donation site.
Researchers ran across the Magecart script, named “ATMZOW” after one of the strings in the code, stealing form data from the checkout page of the site. This included the payment-card data itself (name on card, number, expiry and CVV) as well as additional personal information such as name and billing address.
Jérôme Segura, director of threat intelligence at Malwarebytes, told Threatpost that this particular script uses typical obfuscation but also has some anti-debugging tricks. It infected the site via its e-commerce platform, which he said hadn’t been patched or updated in a while.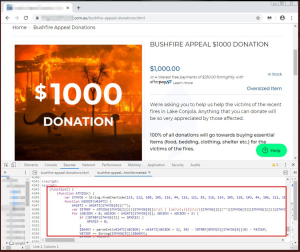
“The compromised site is running Magento, by far the most targeted CMS when it comes to skimming, and was outdated, which is likely how the attackers were able to inject it with malware,” he said in an email interview. “We don’t believe this site was targeted on its own, but rather was victim of an automated attack based on exploiting known vulnerabilities. This reinforces the idea that any site, big or small, business or not for profit, is a valuable resource for criminals.”
Segura declined to name the affected site (but said that it was informed of the problem and that the malicious code “has been removed from the site as we speak”). However, researchers traced the skimmer back to its control panel, a known exfiltration domain at vamberlo[.]com.
“The same ATMZOW script had already been injected into dozens of other websites before this one and using the same exfiltration domain as well,” Segura told Threatpost.
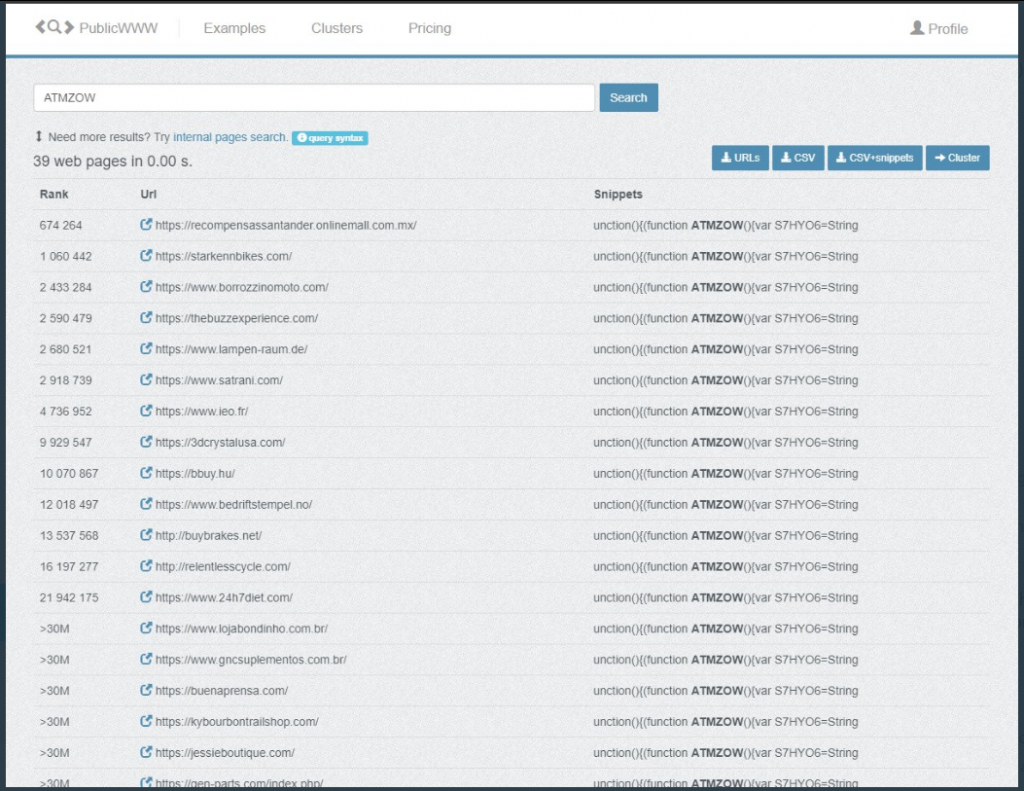
Troy Mursch of Bad Packets Report said via tweet that the PublicWWW tool indeed shows that ATMZOW is active on 39 other websites, and posted a screenshot:
Magecart is an umbrella term encompassing several different threat groups who typically use the same modus operandi. They compromise websites by exploiting vulnerabilities in third-party e-commerce platforms, in order to inject card-skimming scripts on checkout pages.
At Virus Bulletin last October, researchers at RiskIQ said that Magecart is now so ubiquitous that its infrastructure is flooding the internet. There are at least 570+ known command-and-control (C2) domains for the group, with close to 10,000 hosts actively loading those domains, researchers said.
Even so, Segura told Threatpost that this could be the tip of the iceberg.
“Client-side web skimmers have become well documented over the past couple of years,” he said. “However, what we read about is probably only a small fraction of the total number of active compromises. In particular, we rarely ever hear about skimmers that work server-side because only very few companies/researchers are able to get visibility into these breaches.”
Concerned about mobile security? Check out our free Threatpost webinar, Top 8 Best Practices for Mobile App Security, on Jan. 22 at 2 p.m. ET. Poorly secured apps can lead to malware, data breaches and legal/regulatory trouble. Join our experts to discuss the secrets of building a secure mobile strategy, one app at a time. Click here to register.