Multiple vulnerabilities in the Citrix Application Delivery Controller (ADC) and Gateway would allow code injection, information disclosure and denial of service, the networking vendor announced Tuesday. Four of the bugs are exploitable by an unauthenticated, remote attacker.
The Citrix products (formerly known as NetScaler ADC and Gateway) are used for application-aware traffic management and secure remote access, respectively, and are installed in at least 80,000 companies in 158 countries, according to a December assessment from Positive Technologies.
Other flaws announced Tuesday also affect Citrix SD-WAN WANOP appliances, models 4000-WO, 4100-WO, 5000-WO and 5100-WO.
Attacks on the management interface of the products could result in system compromise by an unauthenticated user on the management network; or system compromise through cross-site scripting (XSS). Attackers could also create a download link for the device which, if downloaded and then executed by an unauthenticated user on the management network, could result in the compromise of a local computer.
“Customers who have configured their systems in accordance with Citrix recommendations [i.e., to have this interface separated from the network and protected by a firewall] have significantly reduced their risk from attacks to the management interface,” according to the vendor.
Threat actors could also mount attacks on Virtual IPs (VIPs). VIPs, among other things, are used to provide users with a unique IP address for communicating with network resources for applications that do not allow multiple connections or users from the same IP address.
The VIP attacks include denial of service against either the Gateway or Authentication virtual servers by an unauthenticated user; or remote port scanning of the internal network by an authenticated Citrix Gateway user.
“Attackers can only discern whether a TLS connection is possible with the port and cannot communicate further with the end devices,” according to the critical Citrix advisory. “Customers who have not enabled either the Gateway or Authentication virtual servers are not at risk from attacks that are applicable to those servers. Other virtual servers e.g. load balancing and content switching virtual servers are not affected by these issues.”
A final vulnerability has been found in Citrix Gateway Plug-in for Linux that would allow a local logged-on user of a Linux system with that plug-in installed to elevate their privileges to an administrator account on that computer, the company said.
Of the 11 vulnerabilities, there are six possible attacks routes; but five of those have barriers to exploitation. Also, the latest patches fully resolve all the issues. Here’s a full list of the bugs with exploitation barriers listed:
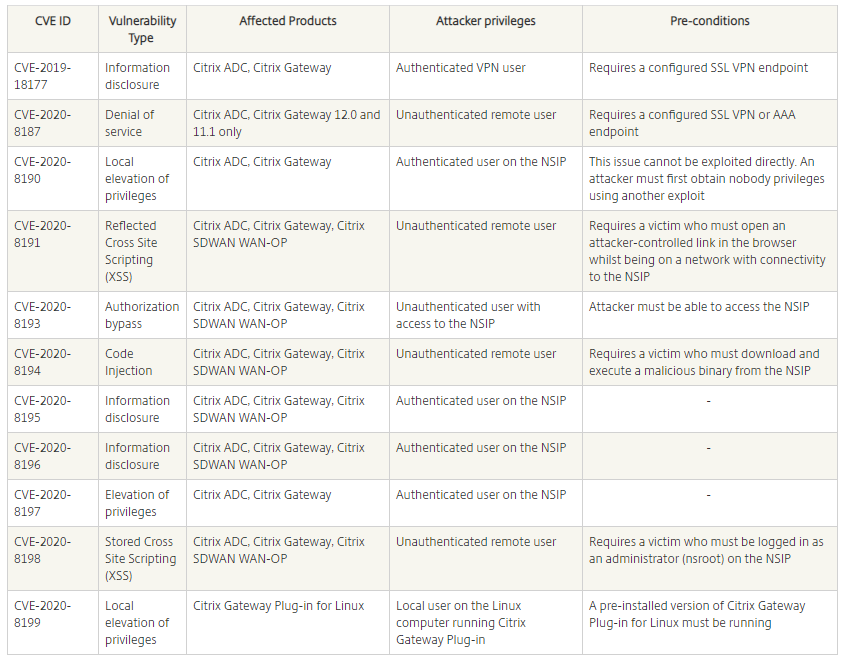
Since Citrix is mainly used for giving remote access to applications in companies’ internal networks, a compromise could easily be used as a foothold to move laterally across a victim organization. However, Citrix CISO Fermin Serna said in an accompanying blog post that the company isn’t aware of any active exploitation of the issues so far, and he stressed that the barriers to exploitation of these flaws are significant.
“There are barriers to many of these attacks; in particular, for customers where there is no untrustworthy traffic on the management network, the remaining risk reduces to a denial-of-service attack,” he wrote. “And in that case, only when Gateway or authentication virtual servers are being used. Other virtual servers, for example, load balancing and content switching virtual servers, are not affected by the issue.”
He added, “three possible attacks additionally require some form of existing access. That effectively means an external malicious actor would first need to gain unauthorized access to a vulnerable device to be able to conduct an attack.”
Serna also noted that the bugs aren’t related to the CVE-2019-19781 critical bug in Citrix ADC and Gateway, announced in December. That zero-day flaw remained unpatched for almost a month and in-the-wild attacks followed.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.











