UPDATE
Adobe has released fixes addressing five critical flaws in its popular Experience Manager content-management solution for building websites, mobile apps and forms. The cross-site scripting (XSS) flaws could allow attackers to execute JavaScript in targets’ browsers.
Including Adobe Experience Manager, Adobe fixed 18 flaws as part of its regularly scheduled September updates. It also addressed flaws in Adobe Framemaker, its document-processor designed for writing and editing large or complex documents; and InDesign, its desktop publishing and typesetting software application.
Adobe on Sept. 15 also fixed “important-severity” flaws in Adobe Media Encoder, as part of an out-of-band patch. The out-of-bounds read flaws (CVE-2020-9739, CVE-2020-9744, CVE-2020-9745) could enable information disclosure.
“The impact of any exploitation of these vulnerabilities, no matter their criticality, could open any organization up to the release of private information, easy lateral movement through a network, or the hijacking of critical information all due to the heavy use of these tools in marketing and its unfettered access to critical information,” said Richard Melick, senior technical product manager at Automox, in an email. “It is important to patch these vulnerabilities as soon as possible.”
Adobe patched 11 bugs overall in its Experience Manager; five of those are rated critical severity, and the rest are “important” severity. The critical flaws are all XSS glitches (CVE-2020-9732, CVE-2020-9742, CVE-2020-9741, CVE-2020-9740 and CVE-2020-9734).
“Successful exploitation of these vulnerabilities could result in arbitrary JavaScript execution in the browser,” according to Adobe.
The five important-severity flaws include an issue allowing for execution with unnecessary privileges, leading to sensitive information disclosure (CVE-2020-9733), four cross site scripting flaws (CVE-2020-9735, CVE-2020-9736, CVE-2020-9737, CVE-2020-9738) and an HTML injection glitch (CVE-2020-9743) allowing arbitrary HTML injection in the browser.
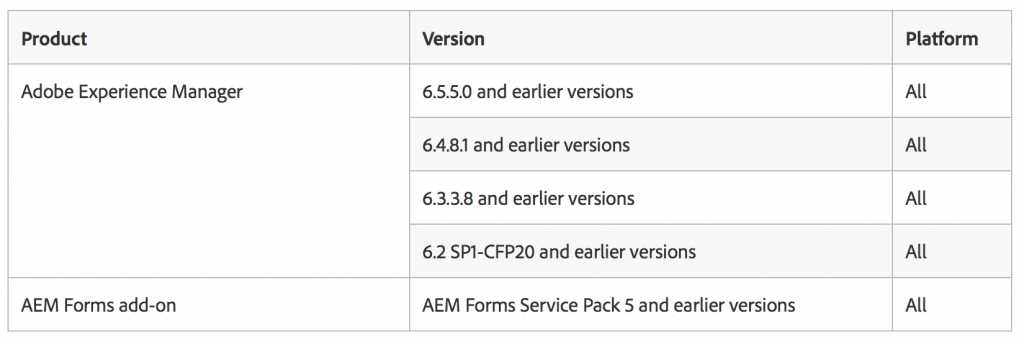
Below is a list of affected product solutions; fixes are available in version 6.5.6.0 and version 6.4.8.2 (as well as AEM Forms Service Pack 6 for AEM forms add-on users).
The update for Adobe Experience Manager received a “priority 2,” meaning it resolves flaws in a product that has “historically been at elevated risk” – but for which there is no known exploits.
“Based on previous experience, we do not anticipate exploits are imminent. As a best practice, Adobe recommends administrators install the update soon (for example, within 30 days),” according to Adobe.
Adobe Framemaker Flaws
Two critical flaws plague Adobe Framemaker versions 2019.0.6 and below for Windows. Adobe issued patches for the flaws in version 2019.0.7 for Windows. An anonymous reporter working through the Zero Day Initiative (ZDI) was credited with finding these flaws.
One of the two flaws was an out-of-bounds read glitch (CVE-2020-9726) that could lead to arbitrary code-execution. An out-of-bounds read is when the software reads data past the end – or before the beginning – of the intended buffer, allowing attackers to read sensitive information from other memory locations or cause a crash.
According to Dustin Childs, communications manager at Trend Micro’s ZDI, the flaw exists within the parsing of Framemaker (FM) files. Specifically, crafted data in an FM file can trigger a read past the end of an allocated buffer, he said.
The second critical flaw was a stack-based buffer overflow error (CVE-2020-9725) that could also enable arbitrary code-execution. Here, the specific flaw also exists within the parsing of FM files, Childs told Threatpost. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length, stack-based buffer, he said.
“In both cases, an attacker can leverage these vulnerabilities to execute code in the context of the current process. An attacker would need to convince a user to open a specially crafted file to get code execution,” Childs told Threatpost.
The update was given a priority rating 3, meaning it “resolves vulnerabilities in a product that has historically not been a target for attackers. Adobe recommends administrators install the update at their discretion,” according to the advisory.
InDesign Flaws
Five critical flaws were discovered in Adobe InDesign for Windows and MacOS. Versions 15.1.1 and below were affected; the fixed version is InDesign 15.1.2.
Successful exploitation of the flaws (CVE-2020-9727, CVE-2020-9728, CVE-2020-9729, CVE-2020-9730, CVE-2020-9731) could lead to arbitrary code execution in the context of the current user.
Kexu Wang of Fortinet’s FortiGuard Labs was credited with reporting the issue. The update for these flaws also received a “priority 3” patch.
“Adobe is not aware of any exploits in the wild for any of the issues addressed in these updates,” according to Adobe on Tuesday.
In April, Adobe plugged 11 critical security holes in Acrobat and Reader, which if exploited could allow attackers to remotely execute code or sidestep security features in the app. Overall, as part of its regularly scheduled security updates in August, Adobe fixed critical- and important-severity flaws tied to 26 CVEs – all stemming from its popular Acrobat and Reader document-management application – as well as one important-severity CVE in Adobe Lightroom, which is its image manipulation software.
This story was updated on Sept. 15 at 2pm to detail several out-of-band vulnerabilities that were patched by Adobe.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Register today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.