COVID-19-related phishing emails, brute-force attacks on remote workers, and a focus on exploiting or abusing collaboration platforms are the hallmarks of cybercriminal enterprise as the coronavirus marks its first anniversary of going global.
A year after the COVID-19 crisis was officially determined to be a pandemic, the way people live and work has radically changed – and so have “the methods and tactics used by criminals on the internet looking to exploit the massive increase in online traffic,” according to a report from Kaspersky, issued on Monday.
Phishing Scams Exploit COVID-19 Themes
Email scamming (and phishing in particular) is still one of the most effective types of attacks in the coronavirus era, according to Kaspersky, since fear and anxiety are two of the most-exploited emotions for this kind of social-engineering attack.
Campaigns such as those purporting to offer N95 masks or hand sanitizer (which prompted people to put in their payment details) became endemic over the course of the year. Impersonating COVID-19 authorities was also a poplar gambit, with cybercriminals offering “important” updates. In reality, all they were offering was malware.
“In 2020, criminals launched a variety of scams that exploited the pandemic topic from just about every angle, from advertisements to masks when they were in short supply to special refunds from the government,” according to the report. “Scammers often imitated leading authority figures on the pandemic, like the CDC and the World Health Organization, to give their emails additional authority — and increase the chances that users would click a malicious link.”
Cybercriminals also used lures involving delayed shipments – taking advantage of the fact that ordering by mail skyrocketed during lockdowns. In 2020, delivery services entered the top ten most-spoofed organizations for these types of attacks, according to Kaspersky.
“They would send emails claiming that, due to COVID, an important delivery had been delayed and that the target must verify the new delivery information (a situation easy to believe in the middle of a pandemic) in order to receive it,” according to the report. “However, upon clicking the attachment, the users would download trojans ranging from spyware to backdoors.”
Brute-Force Attacks on Remote Workers
As millions of employees were sent home to work remotely in 2020, cybersecurity measures were an afterthought for many organizations. Cybercriminals, suspecting this, targeted employees logging in to corporate resources from personal devices and on unsecured home networks, according to the analysis.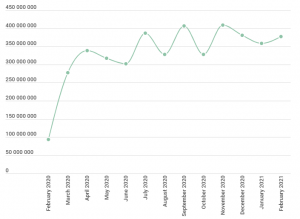
Specifically, brute-force attacks (where attackers try random usernames and passwords against accounts) on Remote Desktop Protocol (RDP) connections ramped up globally, surging 197 percent from 93.1 million worldwide in February to 277.4 million in March. RDP is Microsoft’s proprietary protocol that enables users to access Windows workstations or servers.
“RDP is one of the most popular remote-access protocols used by companies, making it a favorite target for attackers,” according to the report. “In spring of 2020, the number of brute-force attacks against the RDP protocol skyrocketed across almost the entire planet.”
A year later, the number of attacks has not returned to pre-pandemic levels, Kaspersky noted: In February, there were 377.5 million brute-force attacks.
Cyberattacks on Collaboration Platforms Ramp Up
Cyberattackers have also gone after users of various cloud services, especially collaboration services like Flock, GotoMeeting, HighFive, Join.me, Lifesize, MS Teams, Slack, Webex and Zoom. Kaspersky found that by May of last year, the average daily number of attacks on these services seen in its telemetry had jumped 25 percent just since February 2020.
These too haven’t really abated.

Collaboration attacks over the past year. Click to enlarge. Source: Kaspersky.
“The number of web attacks, after displaying a decline in the summer of 2020, reached a new peak in December as much of the world was facing a second wave of the pandemic,” according to Kaspersky. “A large portion of users’ time spent online was dedicated to meeting and collaborating virtually. That is why meeting and messenger apps, like Zoom and Teams, became a popular lure for distributing cyberthreats.”
Most of these attacks involve malicious files being spread under the guise of these apps’ names, Kaspersky found that in January, there were 1.15 million such files detected — the highest number since the lockdown began.
“These files are often bundled as part of seemingly legitimate application installers, which can be encountered in several ways: Through phishing emails claiming to have notifications or special offers from their platforms or through phishing web pages,” according to the report.
What’s Next for COVID-19 Cyberattacks?
With the pandemic heading into a new phase involving vaccinations, there’s also a new crop of topics for phishers and scammers to exploit, like health passports for travel or vaccine distribution, Kaspersky warned.
“Chances are they will exploit them,” according to the report. “It is important that users view any email or website referencing the pandemic with a skeptical eye. What is more, recent events have shown how willing criminals are to take advantage of crisis, and, while this pandemic will subside, it certainly will not be the last crisis.”
The report also noted that remote working will likely remain in place even post-pandemic.
“RDP is not going anywhere — and neither are attacks against the protocol,” the report concluded. “That means businesses need to reevaluate their usage of RDP and learn how to secure remote access. If there is has ever been a time for companies to reevaluate and bolster their security strategy, that time is now.”
Microsoft’s probe comes amidst news that ransomware gangs are starting to take aim at the Exchange Server vulnerabilities, adding a new sense of urgency to the need for organization to apply patches and disinfect backdoors from networks.
Check out our free upcoming live webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community:
- March 24: Economics of 0-Day Disclosures: The Good, Bad and Ugly (Learn more and register!)
- April 21: Underground Markets: A Tour of the Dark Economy (Learn more and register!)











