In 2014, there were increases in malware designed to target retail point-of-sale systems and attack supervisory control and data acquisition (SCADA) systems, according to Dell’s annual threat report.
The report [pdf] was released, interestingly enough, just one day before Verizon’s industry standard Data Breach Investigations Report. It highlights emergent attack trends from 2014 by analyzing data gathered by Dell’s global response intelligence defense network, which consists of millions of security sensors in more than 200 countries, honeypots, malware and internet protocol reputations from firewalls and email security services, shared intelligence from freelance researchers, and the broader industry and spam alerts from Dell security products.
Perhaps the most stark finding reveals that the amount of attacks targeting industrial control and SCADA systems doubled from 2013 to 2014. Most attacks targeted systems in Finland, the U.S. and the U.K., which is no surprise, Dell says, because Internet-connected industrial control systems are comparatively common in these regions. Buffer overflows remain the most commonly exploited vulnerabilities in SCADA software.
Research from @DellSecurity found a 100% increase in attacks against #SCADA systems via @Threatpost
Tweet
Dell said it saw worldwide SCADA attacks increase from 91,676 incidents in January 2012 to 163,228 in January 2013 and then on further to 675,186 in January 2014. Coming in behind buffer overflows, which accounted for 25 percent of SCADA attacks, are improper input validation and information exposure bugs, each of which accounted for just over nine percent of attacks.
Not surprisingly considering the deluge of retail attacks in 2014, Dell is reporting that it generated 13 new point-of-sale-related malware signatures in 2014, compared to just three in 2013.
“Malware targeting point-of-sale systems is evolving drastically, and new trends like memory scraping and the use of encryption to avoid detection from firewalls are on the rise,” said Patrick Sweeney, executive director, Dell Security. “To guard against the rising tide of breaches, retailers should implement more stringent training and firewall policies, as well as re-examine their data policies with partners and suppliers.”
The call to reexamine partner and supplier data policies is a clear allusion to the Target breach in late 2013, in which attackers used billing credentials for an HVAC contractor to compromise the retail giant’s payment processing servers. Interestingly, Target’s 2013 breach was the largest known in history until Home Depot took secured the top spot after its breach in 2014.
According to data, retail breaches in 2014 were often caused by outdated software installations, under-restricted contractor access to sensitive networks, poorly secured mobile network access and a general lack of regulation for employee Internet access.
Broadly speaking, Dell claims to have collected 37 million malware samples in 2014, nearly double the 19 million collected the prior year.
Some good news from the report, though Dell chose to spin it as bad news, is that there was a 109 percent increase in the volume of HTTPS web connections from the start of 2014 to the start of 2015. Despite the fact that more encryption is generally lauded as a universally good thing (unless you are the FBI Director James Comey or NSA Director Mike Rogers), Dell is concerned that more encryption offers more opportunity for criminals to encrypt malware in transit, which, in turn, could let more malware through corporate and personal firewalls. Dell says malvertising schemes perpetrated on Forbes and Yahoo are examples of this abuse.
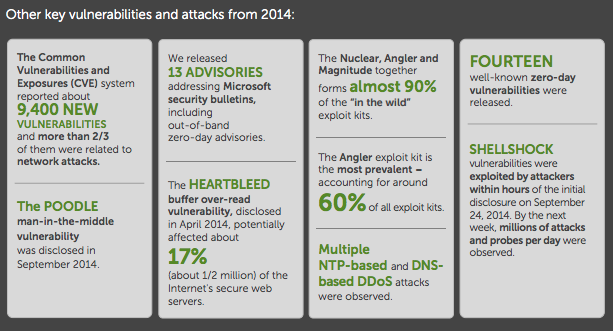
Other facts of interest in the report include the 9,400 new vulnerabilities entered into the common vulnerability and exposures system; the emergence of Internet-wide bugs like Heartbleed, Shellshocked and POODLE; the increased prevalence of the Anlger exploit kit; and the continuance of amplified distributed denial of service attacks.