Recently, one of my friends from my submarine days sent me a friend request on Facebook. The weird thing is, I was already connected with this friend. Looking further at the profile, I noticed a few of the same pictures but only 11 friends. So I knew this was some scammer and, being me, I messaged them.
“Long time no see man, how have you been?” I said. They replied with some short pleasantries and almost immediately began to ask if I knew about some program where I could get money. My response: “Where did you and I meet? What year, what state?” This wouldn’t be something they could know, because we met on a military base that wasn’t in either of our hometowns or current cities. They deleted the account almost immediately.
Fake accounts are used for other purposes too: Facebook for instance last fall announced the takedown of 14,000 fake accounts used to spread disinformation in the 2020 election.
Account Fraud: Beyond Social Media
Fake-account creation and utilizing fake accounts is a problem for not only social-media platforms but almost any enterprise that has a system that collects accounts for any purpose. We all have logins for places we shop, so we can get emails about specials or limited time offers. Many of us have logins for our favorite food-ordering programs, car services, airline rewards programs and many more. In fact, many of us do not transact with an organization without setting up an account there.
So are fake accounts for these types of services a big concern? Why would it matter if the account didn’t represent a one-to-one relationship with real people?
The answer: Fake account creation can result in massive fraud, a problem often minimized because everyone has encountered a fake account at one time or another.
For example, the U.S. Secret Service recently announced the return of roughly $2 billion in fraudulent unemployment requests. And the FCC recently found that 80 percent of the comments on net neutrality were fudged, with 7.7 million of the comments coming from a 19-year-old college student who fabricated people’s names and addresses using software.
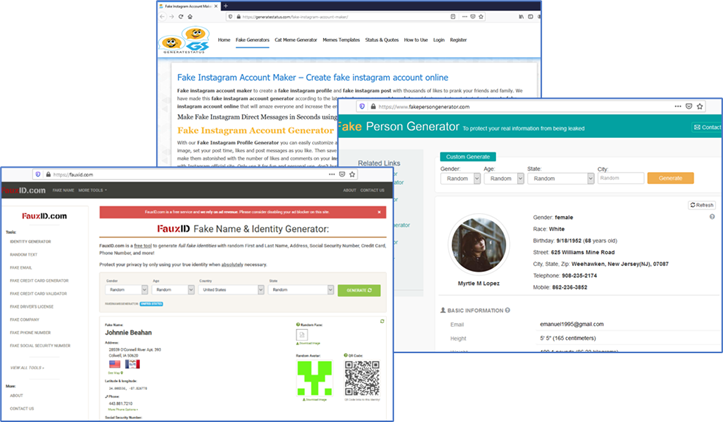
Fake-account generators. Source: Cequence.
Yes — fake accounts are so commonly used that there are software tools that automate the creation to “mask your identity or generate status.” A web search I did quickly uncovered several offerings.
Sneaker-Bots and More

An example of a sneaker-bot offering, from AIO Bot. Source: AIO Bot.
Additional fraudulent fake-account use extends deep into the retail world, where they are used heavily by “hype-sale” bots in grabbing up highly desired items. Once a threat actor has created enough email addresses and “farmed” them to look like real people by sending emails, watching YouTube videos and in general, acting like a human, they then go set up accounts on the desired platforms for the purpose of making purchases of the next item to “drop.” This means these platforms have hundreds of accounts that are simply controlled by the threat actor.
When the drop happens, they are already logged in and hundreds of accounts attempt to checkout at once. No wonder you can’t buy that hot new pair of Yeezys, the latest game console, video card or package of toilet paper.
Being targeted by criminal organizations or individuals for fraud is something we all deal with from time to time, but online it’s possible to be dealing with them in a near-constant stream. But the main issue with the phenomenon of fake accounts is the fact that, whether on a social-media platform, utilizing a public service or simply trying to buy a pair of sneakers, fake accounts are competing with your ability to be recognized as a real individual who desires to be heard. Threat actors are using fake accounts to overwhelm your senses and snap up the things you wish to buy, believe in or support.
Ultimately, that’s fraud too, and it needs to be recognized.
Jason Kent is hacker-in-residence at Cequence Security.
Enjoy additional insights from Threatpost’s InfoSec Insider community by visiting our microsite.










