Nvidia has issued fixes for high-severity flaws in two popular gaming products, including its graphics driver for Windows and GeForce Experience. The flaws can be exploited to launch an array of malicious attacks – from denial-of-service efforts (DoS) to escalation of privileges.
The majority of the high-severity flaws are in the Windows GPU Display Driver, Nvidia’s graphics driver used in devices targeted to enthusiast gamers. This is the software component that enables the device’s operating system and programs to use its high-level graphics hardware.
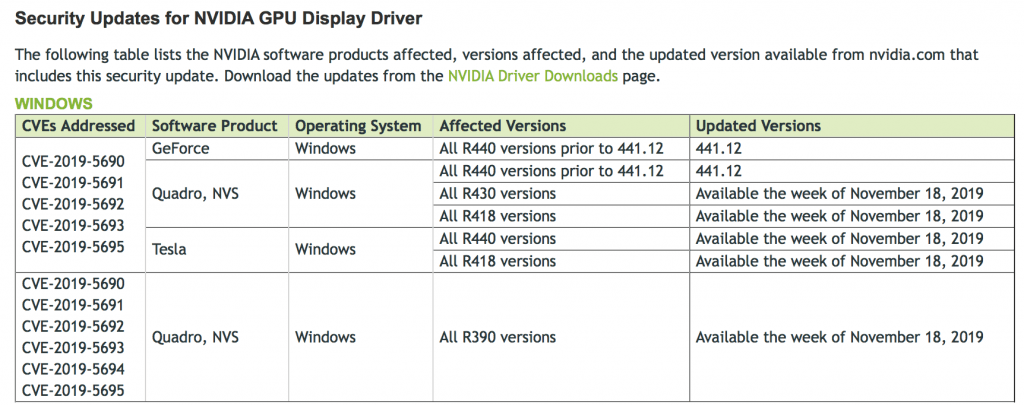
The driver has three high-severity flaws (CVE‑2019‑5690, CVE‑2019‑5691, CVE‑2019‑5692), which all stem from the kernel mode layer handler component of the driver, Nvidia said on Wednesday.
Kernel mode is generally reserved for the lowest-level, most trusted functions of the operating system; in this case, the layer handler (nvlddmkm.sys) for the DxgkDdiEscape interface within the kernel mode has an array of glitches.
These issues include the handler not validating the size of an input buffer (CVE‑2019‑5690), derefencing a NULL pointer (CVE‑2019‑5691) and using untrusted input when calculating an array index (CVE‑2019‑5692). All of these issues could enable escalation of privileges or DoS.
These flaws are strikingly similar to high-severity vulnerabilities reported by Nvidia in May 2019, which also existed in the DxgkDdiEscape interface within the kernel mode layer of the driver. Those flaws could have led to information disclosure, escalation of privileges and DoS in impacted Windows gaming devices.
Overall the graphics driver has nine vulnerabilities, including three high-severity and six medium-severity flaws. For the updated versions of products, see below.
Another high-severity vulnerability was disclosed in GeForce Experience, a supplemental application to the GeForce GTX graphics card. GeForce Experience keeps users’ drivers up-to-date, automatically optimizes their game settings and more. GeForce Experience is installed by default on systems running NVIDIA GeForce products, Nvidia’s brand of GPUs.
This high-severity flaw (CVE‑2019‑5701) exists because GeForce Experience contains a vulnerability when GameStream is enabled. GameStream is Nvidia’s tool allowing users to stream PC games to Nvidia Shield TVs or Shield Tablets.
According to Nvidia, an attacker with local-system access can load Intel graphics driver dynamic link libraries (DLLs) to GeForce Experience without validating the path or signature. This attack is also known as a binary planting or DLL preloading attack, when an application dynamically loads a DLL without specifying a fully qualified path, potentially leading to DoS information disclosure or escalation of privileges through code execution.
Windows-based GeForce users can update to version 3.20.1, Nvidia said. GeForce Experience had three flaws overall, including two medium-severity vulnerabilities.
The chipmaker has patched an array of flaws so far in 2019: In April, Nvidia released fixes for eight high-severity vulnerabilities in its “Linux for Tegra” driver packages; the worst of which could allow information disclosure, denial of service and code execution on impacted systems. And in March, Nvidia patched another high-severity vulnerability in its GeForce Experience software, which could lead to code-execution or DoS of products if exploited.