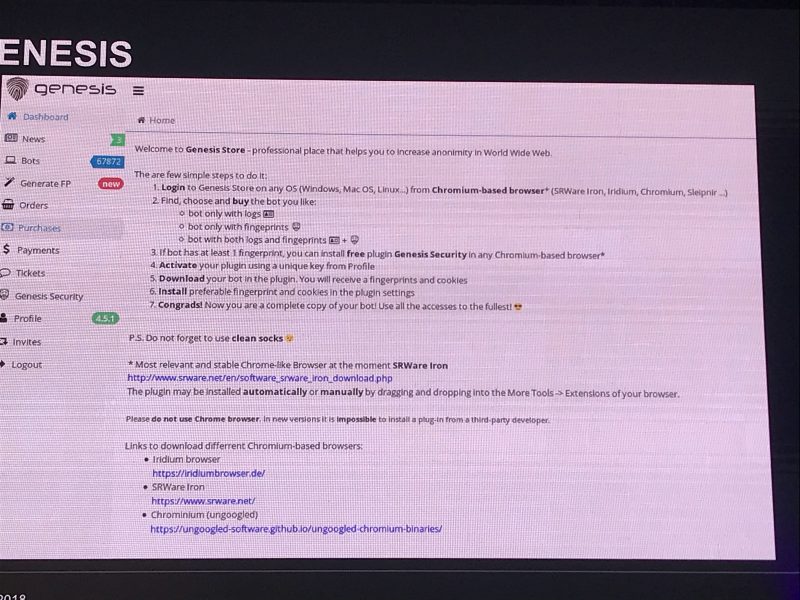
SINGAPORE – A newly-discovered underground marketplace, dubbed Genesis, is peddling tens of thousands of stolen digital “masks” — i.e., identities — which equip cybercriminals with the tools they need to get away with online fraud.
Researchers at Kaspersky Lab’s Security Analyst Summit 2019, which takes place this week in Singapore, said on Tuesday that they first discovered Genesis Darknet in February 2019, trading more than 60,000 compromised digital identities that are meant to evade automatic fraud detection systems that websites and online services use.
“When you use your PC or mobile device to access something online – PayPal, Amazon, online banking, e-commerce sites using your credit card — there’s an anti-fraud system working in the background,” explained Sergey Lozhkin, Kaspersky Lab researcher, during a briefing at SAS 2019. 
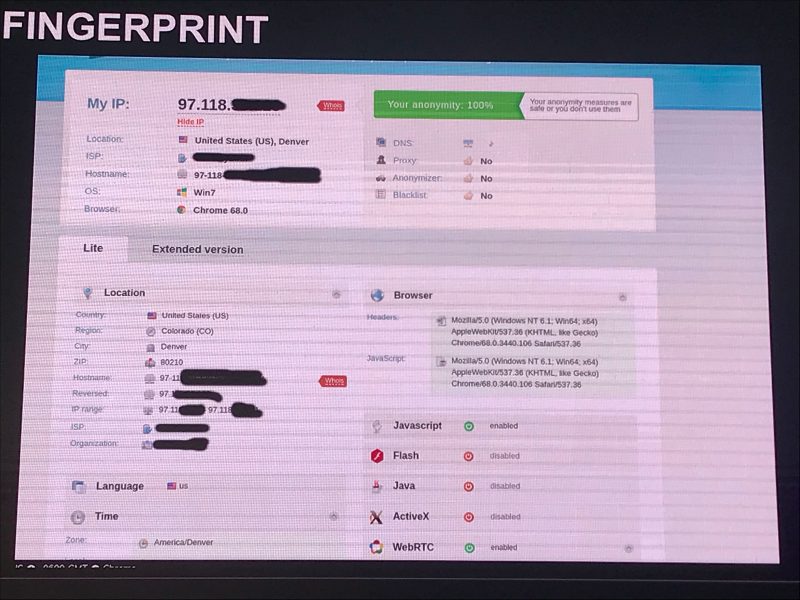
Lozhkin added that, aside from this type of suspicious behavior, anti-fraud systems also use a device’s digital “mask” to verify legitimate users.
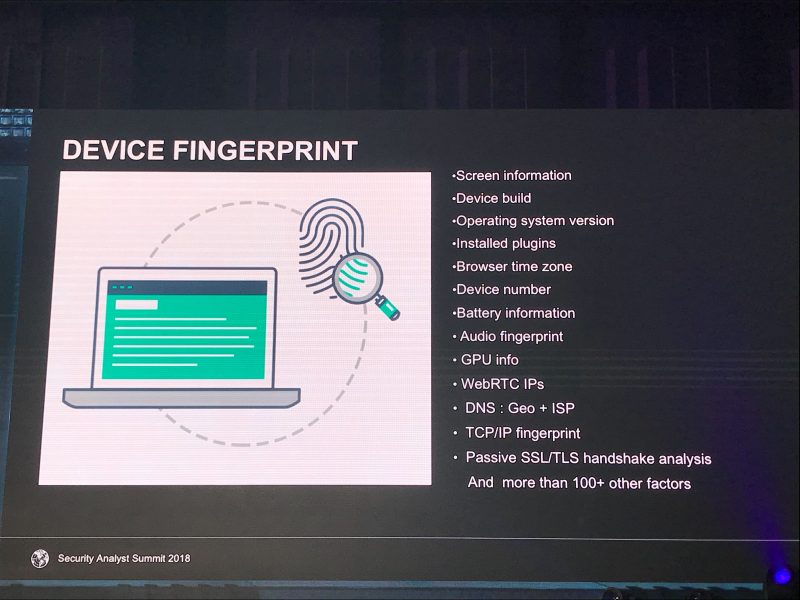
“A digital mask includes device fingerprints – data such as screen information, operating system version, browser time zone and installed plugins, cookies, time on site, clicks on site locations, mouse and touchscreen behavior, etc.,” Lozhkin told Threatpost. “These masks are used by financial organizations’ anti-fraud solutions to check whether they are dealing with a real users or a malicious one, trying to illegally cash out somebody else’s funds.”
If a bad actor were to have a seemingly legitimate digital mask on hand, they could circumvent these anti-fraud controls, making credit-card fraud easier to conduct. That means customers on the marketplace could buy previously-compromised digital identities, along with stolen logins and passwords to online shops and payment services. They could then launch them through a browser and proxy connection to mimic real user activity – and commit fraud without setting off any detection alarms, researchers said.
“If [Genesis customers] have the legitimate user’s account credentials, the attacker can then access their online accounts or make new, trusted transactions in their name,” according to the analysis.
The information is harvested via a specialized malware, according to the report. It steals logins and passwords for accounts, cookies, system info and the aforementioned device fingerprint parameters. The profile is then placed into the Genesis market, where it’s indexed; cybercriminals can then perform an easy search by parameter to uncover the types of profiles they’re interested in.
Another aspect of Genesis is that it offers a generator for creating a unique fingerprint. A criminal can choose the OS, browser and country you want, and it will generate a profile using bits and pieces of stolen profiles.
“This is fully customizable — you choose the platform, any parameter you like and you can adjust it accordingly, for a brand-new, legitimate-looking profile,” the researcher said.
The value of stolen identities range from $5 to $200, depending on how rich the information in the profile is.
“It depends on how many accounts are included in the profile, and what type; does it include online banking, PayPal, Amazon? Or just email and social networks and a few online shops?” Lozhkin explained. “If the latter, the cost is less.”
This type of digital-identity theft is growing in popularity as more cybercriminals recognize the benefits of sidestepping automated solutions that are meant to discover fraud. This particular market has been around about a year, Lozhkin told Threatpost, and is a reaction to tightening online security.
“Financial gain remains a powerful driving force for many attackers, and to bypass modern anti-fraud solutions, threat actors now need more than access credentials,” he said.
The good news is that tech companies are also prioritizing digital-identity security. Microsoft in July, for instance, launched a new bug bounty program offering payouts for discoveries of holes in its array of digital identity solutions.
However, Lozhkin for his part stressed that researchers are seeing the trend of financial fraud growing globally.
“While the industry invests heavily in anti-fraud measures, digital doppelgangers are hard to catch,” he said. “An alternative way to prevent the spread of this malicious activity is to shut down the fraudsters’ infrastructure. That is why we urge law-enforcement agencies across the world to pay extra attention to this issue and join the fight.”
Don’t miss our free Threatpost webinar, “Data Security in the Cloud,” on April 24 at 2 p.m. ET.
A panel of experts will join Threatpost senior editor Tara Seals to discuss how to lock down data when the traditional network perimeter is no longer in place. They will discuss how the adoption of cloud services presents new security challenges, including ideas and best practices for locking down this new architecture; whether managed or in-house security is the way to go; and ancillary dimensions, like SD-WAN and IaaS.