Google is increasing the reward amounts in its bug-bounty program for reports focusing on potential attacks in the product-abuse space, to top out at $13,337 per report.
Product abuse is when a threat actor uses a legitimate service in a way that enables social-engineering or other cyberattacks. For instance, last year a campaign made the rounds that took advantage of a common default feature for people using Gmail on their smartphones: Calendar invites automatically pop up on phones, prompting users to accept or decline them. Cybercriminals were sending targets an unsolicited calendar invitation carrying a link to a phishing URL.
In another example, researcher Martin Vigo discovered that it was possible to join a Google Meets enterprise meeting by phone, if one knew the phone number and a 4-digit PIN for the meeting; these were discoverable by simple “wardialing” and brute-forcing, among other techniques. Also, he found that recurring meetings have static numbers and PINs, offering former employees a simple attack vector.
“The nature of product abuse is constantly changing,” wrote Google’s Marc Henson, lead and program manager for Trust & Safety, and Anna Hupa, senior strategist, in a blog this week. “Why? The technology (product and protection) is changing, the actors are changing and the field is growing. Within this dynamic environment, we are particularly interested in research that protects users’ privacy, ensures the integrity of our technologies, as well as prevents financial fraud or other harms at scale.”
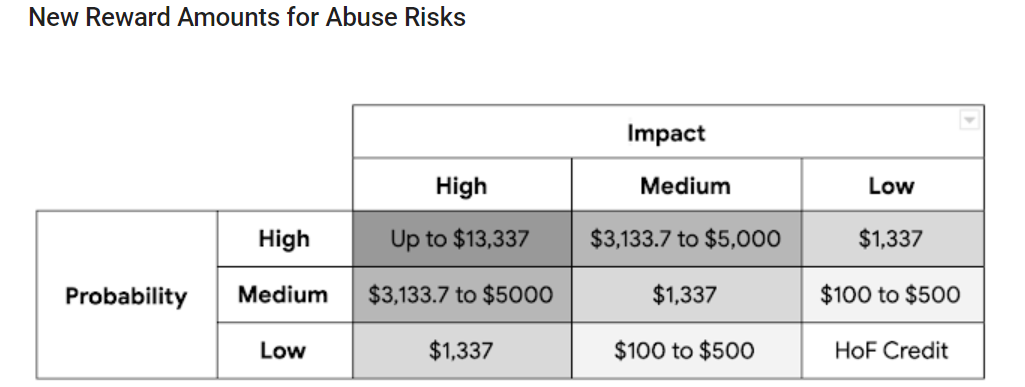
The highest reward in the product-abuse program has now increased by 166 percent, from $5,000 to $13,337. Research with medium- to high-impact and probability will now earn up to $5,000. A full breakdown of the rewards is below:
“Reports that qualify for a reward are those that will result in changes to the product code, as opposed to removal of individual pieces of abusive content,” added Henson and Hupa. “The final reward amount for a given abuse risk report also remains at the discretion of the reward panel. When evaluating the impact of an abuse risk, the panels look at both the severity of the issue as well as the number of impacted users.”
They added that the increased reward levels will soon be followed by an expansion in Google’s Vulnerability Research Grants, to support cyber-research into preventing abuse risks.
The internet giant has so far identified more than 750 previously unknown product abuse risks through the program, they said.
Google has continually expanded its bug-bounty programs. Last year for instance it debuted the Developer Data Protection Reward Program, which offers up to $50,000 for reports on violations of the Google Play, Google API and Google Chrome Web Store Extension program privacy policies.
Also in 2019, Google tripled top reward payouts for security flaws in Chrome from $5,000 to $15,000 – and doubled the maximum reward amount for high-quality reports from $15,000 to $30,000.
The Android Security Rewards program meanwhile has added additional exploit categories, and upped the top prize to $1 million for a full-chain, remote-code-execution exploit with persistence that compromises the Titan M secure element on Pixel devices.
This year marks the tenth anniversary of Google starting its bug-bounty efforts; in January, it said that it had paid out $21 million in rewards to date and $6.5 million last year alone.
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Register today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.