Google’s reCaptcha service has been cracked by a group of University of Maryland researchers who devised an automated attack that can break the service with 85 percent accuracy.
The researchers created a tool called unCaptcha that is able to abuse the audio challenge option of Google’s reCaptcha V2 service.
Google introduced reCaptcha in 2014 to most of its public services in an effort defeat bots and scripts that can speedily register hundreds of free web-service accounts at a time. CAPTCHA stands for Completely Automated Public Turing test to tell Computers and Humans Apart. ReCaptcha is Google’s name for its own technology and free service that uses image, audio or text challenges to verify a human is signing into an account.
“We evaluate unCaptcha using over 450 reCaptcha challenges from live websites, and show that it can solve them with 85.15 percent accuracy in 5.42 seconds, on average,” wrote authors of the UM paper (PDF) Kevin Bock, Daven Patel, George Hughey and Dave Levin.
In the case of unCaptcha, the method doesn’t rely on the image portion of the challenge, rather it identifies digits or words spoken in an audio clip. “Visually impaired users are incapable of solving these visual captchas, prompting the creation of audio captchas,” the researchers explain.
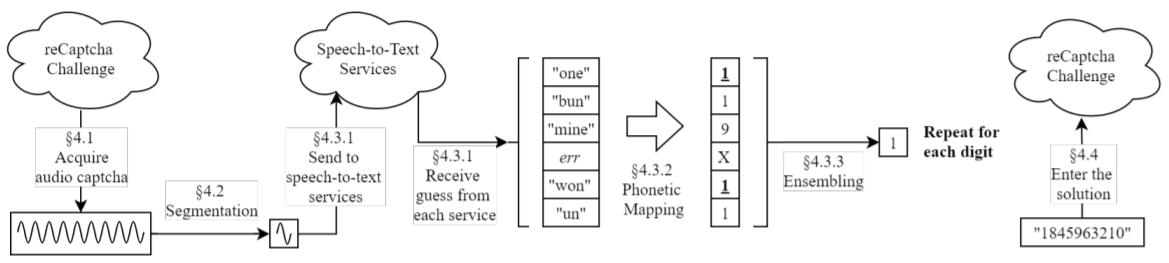
According to the research paper, unCaptcha combines free speech-to-text engines online and advanced phonetic mapping techniques. First, researchers select the audio option of the reCaptcha services using browser automation software. This triggers the download of the sound file. Next, using free online speech-to-text services they are able to identify the audio word challenge.
“After performing phonetic mapping on each of the individual speech recognition services’ predictions, we ‘ensemble’ their responses to obtain a single answer,” researchers wrote. “After a candidate string of digits has been assembled, unCaptcha organically (with uniform timing randomness between each character) types the solution into the field and clicks the ‘Verify’ button.”
Google is no stranger to having its reCaptcha broken. In March, researchers at East-Ee Security detailed a proof of concept bypass that used Google’s own web-based tools to crack the security measure.
The tool dubbed ReBreakCaptcha is able to defeat reCaptcha security via a script that uses Google’s own APIs to capture audio challenges as sound files. Then it uses speech-to-text technology to convert audio into text answers that are then inputted as text-based solutions to audio-based challenges used in reCaptcha.
Again, in 2016 at Black Hat Asia, security researchers from Columbia University published a paper I’m not a human: Breaking the Google reCAPTCHA (PDF). According the paper’s authors, their technique automatically solved 70.78 percent of the image reCaptcha challenges, while requiring only 19 seconds per challenge.
East-Ee Security did not provide any comparable data for its ReBreakCaptcha bypass.