Threat actors exploited a vulnerability in the popular 3D computer graphics Autodesk software in order to launch a recent cyber-espionage attack against an international architectural and video production company.
Researchers said that further analysis of the attack points to a sophisticated, APT-style group that had prior knowledge of the company’s security systems and used software applications, carefully planning their attack to infiltrate the company and exfiltrate data undetected. The targeted company, which researchers did not name, is known to have been collaborating in billion-dollar real estate projects in New York, London, Australia and Oman.
The hallmark of the attack is its use of a malicious plugin for Autodesk 3ds Max, a computer graphics program used by engineering, architecture or gaming organizations for making 3D animations, which is developed by Autodesk Media and Entertainment.
“During the investigation, Bitdefender researchers found that threat actors had an entire toolset featuring powerful spying capabilities and made use of a previously unknown vulnerability in a popular software widely used in 3D computer graphics (Autodesk 3ds Max) to compromise the target,” said researchers with Bitdefender in a Wednesday analysis.
The Flaw
The malicious payload was purporting to be a plugin for Autodesk 3ds Max (though they did not say how victims were persuaded to download the plugin). In reality, the plugin is a variant of a MAXScript exploit of Autodesk 3ds Max, which is called “PhysXPluginMfx.”
This exploit can corrupt the settings of 3ds Max software in order to run malicious code, and ultimately propagate to other files on a Windows system (if the files containing the script are loaded into 3ds Max).
Autodesk for its part issued an advisory for the flaw earlier in August: “Autodesk recommends 3ds Max users download the latest version of Security Tools for Autodesk 3ds Max 2021-2015SP1 available in the Autodesk App Store to identify and remove the PhysXPluginMfx MAXScript malware,” according to the company.
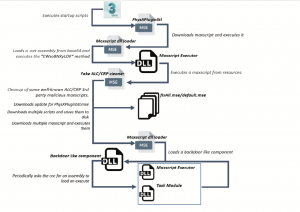 In the case of this specific espionage campaign, attackers utilized the MAXScript PhysXPluginStl exploit to download and execute an embedded DLL file. This file acts as a loader for two .net binary files. These files then download other malicious MAXScripts, which collect varying information about the victim (including web browser passwords for Google Chrome and Firefox, information about the machine and screenshots), encrypt it with a custom algorithm and mask the result so that it appears to be base64 content.
In the case of this specific espionage campaign, attackers utilized the MAXScript PhysXPluginStl exploit to download and execute an embedded DLL file. This file acts as a loader for two .net binary files. These files then download other malicious MAXScripts, which collect varying information about the victim (including web browser passwords for Google Chrome and Firefox, information about the machine and screenshots), encrypt it with a custom algorithm and mask the result so that it appears to be base64 content.
As part of this, researchers uncovered a slew of spying tools utilized by the threat actor, including HdCrawler, which lists, compresses and uploads specific files to the C2; and an InfoStealer, which has the ability to screen capture and collect the username, IP addresses of network adapters, information about storage, and more information about the system.
The attackers’ level of sophistication can be seen in a tricky tactic they used to sidestep detection, researchers said: If Task Manager or Performance Monitor applications are running (and their respective window is visible) during the attack, then a flag is set that instructs the binary to sleep more and more often (thus reducing the consumption of CPU, which would be a red flag to the victim).
While attackers were successful in compromising the targeted company, it’s unclear how much information was actually stolen during the campaign.
APT For Hire
Another key takeaway of the campaign is that it appears to have been launched by “APT mercenary groups,” which are sophisticated actors tout powerful espionage tools – and who offer their services to the highest bidder, researchers claim. Threat actors of this campaign, who used South Korean-based Command and Control (C2) infrastructure, were potentially such a group, Liviu Arsene, global cybersecurity analyst with Bitdefender, told Threatpost.
“The TTPs revealed during the investigation do point to APT-style modus operandi, which means they have the knowledge and the skills necessary to pull off coordinated and pin-point accurate attacks on select victims,” Arsene told Threatpost. “Coupled with the fact that they made use of a previously unknown vulnerability in a software used by the company, shows both footprinting capabilities (usually associated with advanced actors that scout their victims in advance) and that they have the technical skills to find and exploit such a vulnerability.”
APT-for-hire groups are increasingly becoming more popular in the threat landscape. The StrongPity APT and “Dark Basin” groups are all previously discovered APT mercenaries, which have allegedly acted on behalf of customers seeking to discredit or infiltrate high-profile targets in financial, legal, and now the multi-billion-dollar real-estate industry, researchers said.
“The commoditization of APT-level hackers-for-hire could potentially entice rival luxury real-estate investors involved in multi-billion-dollar contracts to seek these services to spy on their competition by infiltrating their contractors,” Bitdefender researchers said. “Industrial espionage is nothing new and, since the real-estate industry is highly competitive, with contracts valued at billions of dollars, the stakes are high for winning contracts for luxury projects and could justify turning to mercenary APT groups for gaining a negotiation advantage.”
On Wed Sept. 16 @ 2 PM ET: Learn the secrets to running a successful Bug Bounty Program. Resister today for this FREE Threatpost webinar “Five Essentials for Running a Successful Bug Bounty Program“. Hear from top Bug Bounty Program experts how to juggle public versus private programs and how to navigate the tricky terrain of managing Bug Hunters, disclosure policies and budgets. Join us Wednesday Sept. 16, 2-3 PM ET for this LIVE webinar.











