Over half of all Android handsets are susceptible to a clever over-the-air SMS phishing attack that could allow an adversary to route all internet traffic through a rogue proxy, as well as hijack features such as a handset’s homepage, mail server and directory servers for synchronizing contacts and calendars.
Researchers at Check Point said Samsung, Huawei, LG and Sony handsets are “susceptible” to the phishing ploy.
“In these attacks, a remote agent can trick users into accepting new phone settings that, for example, route all their internet traffic through a proxy controlled by the attacker,” Check Point researchers Artyom Skrobov and Slava Makkaveev wrote in a blog post outlining their research on Wednesday.

Check Point said the attack vector was reported to handset makers in March and so far Samsung and LG have released fixes to address what researchers are calling a “phishing flow.” Huawei told Check Point its next-generation of handsets (Mate series or P series) will be updated to mitigate against such an attack.
“Sony refused to acknowledge the vulnerability, stating that their devices follow the [Open Mobile Alliance Client Provisioning] OMA CP specification,” wrote researchers.
Attack Specifics
The attacks are based on over-the-air (OTA) provisioning, a tool used by cellular network operators to deploy network-specific settings to a new phone joining their network, describes Check Point. “However, as we show, anyone can send OTA provisioning messages,” Skrobov and Makkaveev wrote.
Researchers said the weak point in the OTA provisioning is tied to the industry standard approach, called OMA CP, which affords limited authentication between sender and handset.
“A recipient cannot verify whether the suggested settings originate from his network operator or from an imposter,” researchers wrote. Vulnerable handsets “allow users to receive malicious settings via such weakly-authenticated provisioning messages.”
Attack Scenarios
In a hypothetical attack, an adversary would send an OMA CP message via specialized equipment, which includes a GSM modem that could cost as little as $10. Next, the attacker sends a specially crafted binary SMS message to either a specific target or a range of phone numbers.
Researchers said, assuming that at least some of the recipients are gullible enough to accept a CP without challenging its authenticity, the OMA CP message allows the modification of the following settings over-the-air:
- MMS message server
- Proxy address
- Browser homepage and bookmarks
- Mail server
- Directory servers for synchronizing contacts and calendar
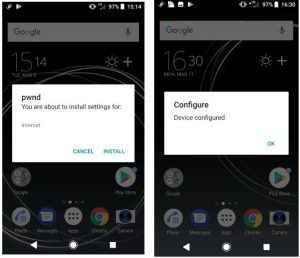
In one attack scenario, involving a Samsung phone, researchers created an OMA CP message that if “accepted” by the user would route internet traffic through a proxy of the researcher’s choosing.
“We emphasize that there is no authenticity check for the attacker to overcome: all that is needed is for the user to accept the CP,” they wrote.
In other attack scenarios involving Huawei, LG or Sony phones an adversary needs to know the victims’ Mobile Subscriber Identity (IMSI) number. IMSI numbers are similar to an internet protocol address. Each phone has a unique IMSI number that is private. However Check Point researchers said they were easily able to identify a target’s IMSI number using a reverse IMSI lookup service.
“Reverse IMSI lookups are cheaply available via commercial suppliers. A rogue Android application can read the user’s IMSI number via the standard API ((TelephonyManager)getSystemService(Context.TELEPHONY_SERVICE)).getSubscriberId()– as long as the application has the permission permission.READ_PHONE_STATE. Over a third of all Android apps released in the last three years already require this permission, so it wouldn’t raise any suspicion,” researchers wrote.
Researchers said the proof-of-concept attacks were performed on the Huawei P10, LG G6, Sony Xperia XZ Premium, and a range of Samsung Galaxy phones, including S9.