A new class of side channel vulnerabilities impacting all modern Intel chips have been disclosed, which can use speculative execution to potentially leak sensitive data from a system’s CPU.
Intel said that the newest class of vulnerabilities, dubbed Microarchitectural Data Sampling (MDS), consist of four different attacks, which all ultimately depend on different ways of executing side channel attacks to siphon data from impacted systems.
“First identified by Intel’s internal researchers and partners, and independently reported to Intel by external researchers, MDS is a sub-class of previously disclosed speculative execution side channel vulnerabilities and is comprised of four related techniques,” Intel said in an advisory released Tuesday. “Under certain conditions, MDS provides a program the potential means to read data that program otherwise would not be able to see.”
Intel said it is not aware of any reported real-world exploits of these security issues.
These vulnerabilities (CVE-2018-12126, CVE-2018-12127, CVE-2018-12130 and CVE-2019-11091) derive from a process called speculative execution in processors. It’s is used in microprocessors so that memory can read before the addresses of all prior memory writes are known; an attacker with local user access can use a side-channel analysis to gain unauthorized disclosure of information.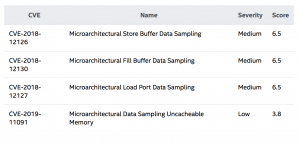
However, while speculative execution side channel previous attacks – like Meltdown – targeted data stored in the CPU’s memory that relies on this process; MDS looks to a different component in the chip using speculative execution. Those components are buffers, such as Fill Buffers (temporary buffers between CPU caches), Load Ports (temporary buffers used when loading data into registers), or Store Buffers (temporary buffers to hold store addresses and data).
“These structures are much smaller than the [level 1 data cache], and therefore hold less data and are overwritten more frequently,” Intel said in an analysis of the flaws. “It is also more difficult to use MDS methods to infer data that is associated with a specific memory address, which may require the malicious actor to collect significant amounts of data and analyze it to locate any protected data.”
Attack Vectors
The four different attack vectors are dubbed ZombieLoad, Fallout, RIDL (Rogue In-Flight Data Load) and Store-to-Leak Forwarding, and have been detailed and publicly disclosed on Tuesday by an array of security researchers.
The ZombieLoad attack “resurrects your private browsing-history and other sensitive data. It allows to leak information from other applications, the operating system, virtual machines in the cloud and trusted execution environments,” according to a page breaking down the MDS attack vectors.
With RIDL (Rogue In-Flight Data Load) attackers can exploit MDS flaws to leak sensitive data: “By analyzing the impact on the CPU pipeline, we developed a variety of practical exploits leaking in-flight data from different internal CPU buffers (such as Line-Fill Buffers and Load Ports), used by the CPU while loading or storing data from memory,” researchers with VUSec and CISPA said.
Meanwhile, the Fallout attack allows bad actors to leak data from Store Buffers, which are used every time a CPU pipeline needs to store any data, several independent researchers (a full list of who discovered the Fallout attack can be found here) said.
Finally, the Store-To-Leak Forwarding attack “exploits CPU optimizations introduced by the store buffer to break address randomization, monitor the operating system or to leak data when combined with Spectre gadgets,” according to researchers with the Graz University of Technology.
Mitigations
Intel sought to downplay the vulnerabilities, saying that: “MDS vulnerabilities have been classified as low to medium severity per the industry standard CVSS, and it’s important to note that there are no reports of any real world exploits of these vulnerabilities.”
However, researchers who discovered the flaws were more concerned about their impact: “The implications are worrisome,” researchers who discovered RDIL said. “Contrary to other state-of-the-art speculative execution attacks, such as Spectre, Meltdown and Foreshadow, RIDL can leak this arbitrary in-flight data with no assumptions on the state of the caches or translation data structures controlled by privileged software.”
Intel said that the new MDS class of flaws is addressed in hardware starting with select 8th and 9th Generation Intel Core processors, as well as the 2nd Generation Intel Xeon Scalable processor family. Future chips will also have integrated fixes.
In addition to hardware fixes, Intel is releasing processor microcode updates as part of its regularly-scheduled update process with OEMs to address the issue in products where MDS is not addressed in hardware.
An array of vendors have released separate security advisories in response to MDS, including Red Hat, Oracle and Microsoft.
“Microsoft has released software updates to help mitigate these vulnerabilities,” according to a Microsoft advisory released Tuesday. “To get all available protections, firmware (microcode) and software updates are required. This may include microcode from device OEMs. In some cases, installing these updates will have a performance impact. We have also acted to secure our cloud services.”
Side Channel Attacks
Side channel speculative execution attacks continue to plague Intel chips – in August, three new speculative execution design flaws in Intel CPUs were disclosed, impacting Intel’s Software Guard Extensions (SGX) technology, its OS and system management mode (SMM) and hypervisor software.
Other Spectre-class flaws have been discovered over the past half year since Spectre and the related Meltdown vulnerability were found, including side-channel variants 1, 2, 3, 3a, and 4.
Raoul Strackx, post-doctoral researcher at KU Leuven, who discovered the Foreshadow side-channel attack, recently told Threatpost that “basically it comes down to the fact that these processes are simply becoming way too complex.”
“I would say that’s the main problem, but if you disable speculative execution, then the performance impact is going to be huge, and so no one would be willing to do this. So there needs to be more academic research there,” he said.
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.











