Researchers have identified a new side-channel attack impacting all modern Intel server processors made since 2012. The vulnerability could allow bad actors to sniff out encrypted passwords as they are being typed into a secure shell session (SSH); but, luckily, such an attack would be difficult to launch.
The attack, disclosed on Tuesday and dubbed NetCAT (short for Network Cache Attack), stems from an Intel performance-enhancing technology called Data-Direct I/O Technology (DDIO). DDIO is turned on by default in most recent Intel server-grade processors, including Intel Xeon E5, E7 and SP processor families.
Targeting DDIO, an attacker could uncover the arrival time of individual network packets from an SSH session, using a remote cache side channel – thus obtaining sensitive information from the cache of the impacted application server.
“NetCAT can break the confidentiality of an SSH session from a third machine, without any malicious software running on the remote server or the client which communicate over SSH,” Michael Kurth, one of the researchers with VU Amsterdam who discovered the attack, told Threatpost. “The third machine is not involved at all in the SSH session between the remote server and the client. NetCAT leaks keystrokes of the clients of the target server on their encrypted SSH sessions even if they are on a different network segment than the attacker (so traditional sniffing attacks are not possible).”
DDIO grants network devices and other peripherals access to the CPU cache, by allowing peripherals to read or write to the last-level cache (as opposed to reading or writing it to slow memory), thus speeding up performance for server applications. That last-level cache is usually shared by all the functional units on the chip and is the farthest away type of cache from the processor.
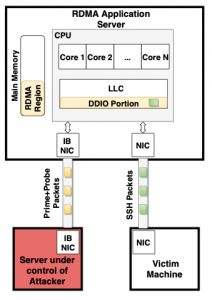
It’s in that last-level cache where the attack could be utilized to steal data. Upon reverse-engineering the properties of DDIO, VU Amsterdam researchers found that the last-level cache is a shared resource between CPU cores and the network card (the device connecting a computer to a computer network) – giving attackers with access to the network a potential way in.
To do that, attackers could use a server under their control to communicate to the application server that supports DDIO and also services network requests from a victim client. They would communicate using Remote Direct Memory Access (RDMA), which allows the memory of one computer to have a direct link into that of another.
Through this communication, bad actors would be able to observe the timing of packets of data and siphon information from that; specifically, they could observe the keystrokes being sent in particular pattern that could reveal sensitive passwords, said the researchers.
“In an interactive SSH session, every time you press a key, network packets are being directly transmitted,” they said. “As a result, every time a victim types a character inside an encrypted SSH session on your console, NetCAT can leak the timing of the event by leaking the arrival time of the corresponding network packet. Now, humans have distinct typing patterns…. As a result, NetCAT can operate static analysis of the inter-arrival timings of packets in what is known as a keystroke timing attack, to leak what you type in your private SSH session.”
The vulnerability (CVE-2019-11184) is not easy to exploit. An attacker would need to be authenticated and would need a direct network connection to the target’s system. In addition, a malicious actor would need to have read/write RDMA access on a target machine using Intel DDIO to launch the attack.
Intel for its part released an advisory on Tuesday seeking to downplay the impact of the attack: According to Intel, the issue has a low CVSS base score of 2.6.
“In scenarios where Intel DDIO and RDMA are enabled, strong security controls on a secured network are required, as a malicious actor would need to have read/write RDMA access on a target machine using Intel DDIO to use this exploit,” Intel said. “In the complex scenarios where Intel DDIO and RDMA are typically used, such as massively parallel computing clusters, malicious actors typically don’t have direct access from untrusted networks.”
However, Kurth told Threatpost that CVSS score generally does not properly capture hardware side-channel attacks with recent high-profile attacks such as Spectre, for example, scoring as medium severity.
“In the case of NetCAT, the low CVSS is mainly due to the confidentiality impact which is set to low by Intel,” he told Threatpost. “With NetCAT we can leak user keystrokes in an SSH session which is confidential. We believe the leakage itself is of high-severity, but the real impact depends on the environment. Data centers and cloud environments, which deploy RDMA, are directly impacted by NetCAT.”
The chip giant did recommend that users limit direct access from untrusted networks when DDIO and RDMA are enabled.
Researchers said that they initiated a coordinated disclosure process with Intel and the Dutch national CERT (NCSC) on June 23 regarding the flaw. The vulnerability was acknowledged by Intel with a bounty of $2,000, Kurth said.
Michael Kurth, Ben Gras, Dennis Andriesse, Cristiano Giuffrida, Herbert Bos, and Kaveh Razavi from VU Amsterdam were credited with reporting the issue.