Intel has issued an updated advisory for more than 30 fixes addressing vulnerabilities across various products – including a critical flaw in Intel’s converged security and management engine (CSME) that could enable privilege-escalation.
The bug (CVE-2019-0153) exists in a subsystem of Intel CSME, which powers Intel’s Active Management System hardware and firmware technology, used for remote out-of-band management of personal computers. An unauthenticated user could potentially abuse this flaw to enable escalation of privilege over network access, according to the Intel advisory, updated this week.
The flaw is a buffer overflow vulnerability with a CVSS score of 9 out of 10, making it critical. CSME versions 12 through 12.0.34 are impacted: “Intel recommends that users of Intel CSME… update to the latest version provided by the system manufacturer that addresses these issues,” according to Intel’s advisory.
Overall, the chip giant issued 34 fixes for various vulnerabilities – with seven of those ranking high-severity, 21 ranking medium-severity and five ranking low-severity, in addition to the critical flaw.
These latest flaws are separate from Intel’s other advisory last week revealing a new class of speculative execution vulnerabilities, dubbed Microarchitectural Data Sampling (MDS), which impact all modern Intel CPUs. Those four side-channel attacks – ZombieLoad, Fallout, RIDL (Rogue In-Flight Data Load) and Store-to-Leak Forwarding – allow for siphoning data from impacted systems.
High-Severity Flaws
In addition to the critical vulnerability, Intel released advisories for several high-severity flaws across different products.
One such glitch is an insufficient input validation that exists in the Kernel Mode Driver of Intel i915 Graphics chips for Linux. This flaw could enable an authenticated user to gain escalated privileges via local access. The vulnerability, CVE-2019-11085, scores 8.8 out of 10 on the CVSS scale. Intel i915 Graphics for Linux before version 5 are impacted; Intel recommends users update to version 5 or later.
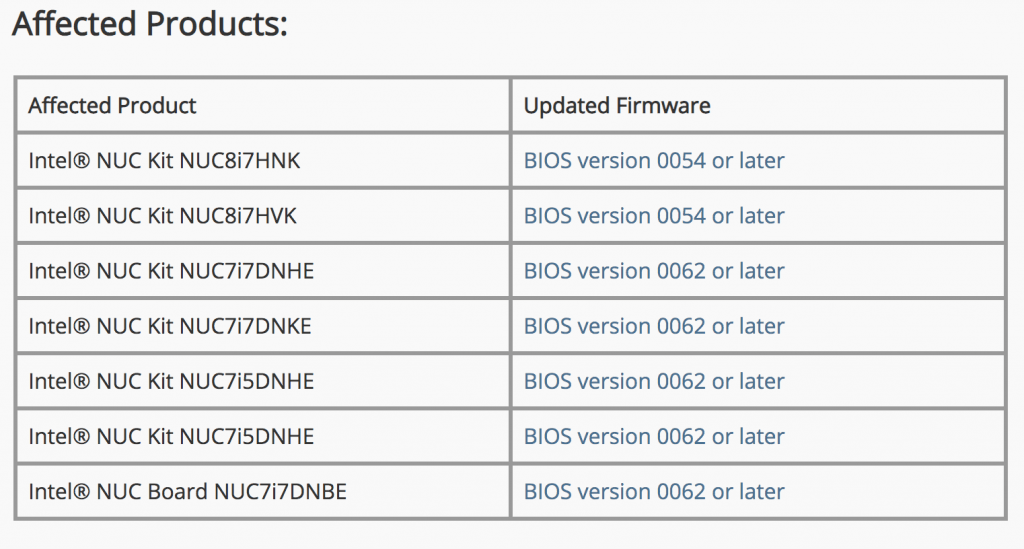
Another high-severity flaw exists in the system firmware of Intel NUC kit (short for Next Unit of Computing); a mini PC kit that offers processing, memory and storage capabilities for applications like digital signage, media centers and kiosks.
This flaw, CVE-2019-11094, ranking a 7.5 out of 10 on the CVSS scale, “may allow an authenticated user to potentially enable escalation of privilege, denial of service and/or information disclosure via local access,”according to Intel. Intel recommends that the impacted products (below) update to the latest firmware version.
Another high-severity flaw, discovered internally by Intel and disclosed last week, exists in in Unified Extensible Firmware Interface (UEFI), a specification defining a software interface between an operating system and platform firmware (while UEFI is an industry-wide specification, specifically impacted is UEFI firmware using the Intel reference code)
“Multiple potential security vulnerabilities in Intel Unified Extensible Firmware Interface (UEFI) may allow escalation of privilege and/or denial of service,” according to last week’s advisory. “Intel is releasing firmware updates to mitigate these potential vulnerabilities.”
The flaw, CVE-2019-0126, has a CVSS score of 7.2 out of 10, and may allow a privileged user to potentially enable escalation of privilege or denial of service on impacted systems.
This vulnerability stems from “insufficient access control in silicon reference firmware for Intel Xeon Scalable Processor, Intel Xeon Processor D Family, according to Intel. In order to exploit the flaw, an attacker would need local access.
Other high severity flaws include: an improper data-sanitization vulnerability in the subsystem in Intel Server Platform Services (CVE-2019-0089), an insufficient access control vulnerability in subsystem for Intel CSME (CVE-2019-0090), an insufficient access control vulnerability (CVE-2019-0086) in Dynamic Application Loader software (an Intel tool allowing users to run small portions of Java code on Intel CSME) and a buffer overflow flaw in subsystem in Intel’s Dynamic Application Loader (CVE-2019-0170).
Lenovo for its part released an advisory with several target dates where it aims to apply patches for its Intel-impacted products, including various versions of the IdeaPad and ThinkPad (see a full list here).
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.