A group of ‘script kiddies’ tied to Iran are targeting companies worldwide with internet-facing Remote Desktop Protocol (RDP) ports and weak credentials in order to infect them with Dharma ransomware.
The Dharma malware (also known as Crysis) has been distributed as a ransomware-as-a-service (RaaS) model since at least 2016. While the ransomware was previously used by advance persistent threat (APT) actors, its source code surfaced in March 2020, making it available to a wider breadth of attackers. That is the case with this latest Iran-linked threat group, which researchers say is unsophisticated and has been targeting companies across Russia, Japan, China and India with the ransomware since June.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” Oleg Skulkin, senior digital forensics specialist with Group-IB, said in an analysis of the attacks posted Monday. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage. Despite that these cybercriminals use quite common tactics, techniques and procedures they have been quite effective.”
The threat actors are unsophisticated because they use publicly available tools both to obtain initial access and move laterally – rather than using custom malware or post-exploitation frameworks, Group-IB senior DFIR analyst Oleg Skulkin told Threatpost.
“The threat actors use Persian language for Google searches on compromised servers and download tools from Iran-linked Telegram groups,” Skulkin told Threatpost. “In addition, Group-IB experts saw the threat actors’ attempt to brute-force accounts on an Iranian video streaming service.”
The attackers in this campaign first would scan ranges of IPs for hosts that contained these vulnerable RDP ports and weak credentials, researchers said. They did so using scanning software called Masscan (which has previously been utilized by bad actors like Fxmsp).
Once vulnerable hosts were identified, the attackers deployed a well-known RDP brute force application called NLBrute, which has been sold on forums for years. Using this tool, they were able to brute-force their way into the system, and then check the validity of obtained credentials on other accessible hosts in the network.
In some attacks, attackers also attempted to elevate privileges using an exploit for an elevation privilege flaw. This medium-severity flaw (CVE-2017-0213), which affects Windows systems, can be exploited when an attacker runs a specially crafted application.
Post compromise, “interestingly, the threat actors likely didn’t have a clear plan on what to do with the compromised networks,” said researchers, showing their lack of sophistication. In different attacks, attackers would download various publicly-available tools to perform reconnaissance or move laterally across the network.
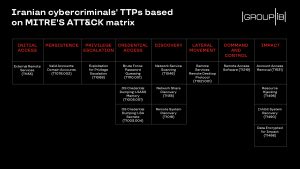 To scan for accessible hosts in the compromised network, for instance, they used publicly-available tool Advanced Port Scanner. Other tools were downloaded by the attackers from Persian-language Telegram channels, researchers said.
To scan for accessible hosts in the compromised network, for instance, they used publicly-available tool Advanced Port Scanner. Other tools were downloaded by the attackers from Persian-language Telegram channels, researchers said.
“For instance, to disable built-in antivirus software, the attackers used Defender Control and Your Uninstaller,” said researchers. “The latter was downloaded from Iranian software sharing website — the Google search query in Persian language “دانلود نرم افزار youre unistaller” was discovered in the Chrome artifacts.”
Attackers would then move laterally across the network and deploy the Dharma variant executable, encrypt data, and leave a ransom note for the victim. Researchers said, hackers typically demanded a ransom between 1 to 5 BTC (worth between 12,000 to 59,000 USD at the time of writing).
Researchers said, though the exact number of victims in this campaign is unknown, the discovered forensic artifacts revealed a that the threat actors in this campaigb are “far behind the level of sophistication of big league Iranian APTs.”
“The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals,” according to Group-IB researchers.
Researchers said part of this change may be attributed to the pandemic exposing a number of vulnerable hosts – with many employees working remotely – making an extremely popular attack vector for cybercriminals. Therefore, the default RDP port 3389 should be closed if not in use, they suggested.
“As the attackers usually need several attempts to brute force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed login attempts per user,” said researchers.
It’s the age of remote working, and businesses are facing new and bigger cyber-risks – whether it’s collaboration platforms in the crosshairs, evolving insider threats or issues with locking down a much broader footprint. Find out how to address these new cybersecurity realities with our complimentary Threatpost eBook, 2020 in Security: Four Stories from the New Threat Landscape, presented in conjunction with Forcepoint. We redefine “secure” in a work-from-home world and offer compelling real-world best practices. Click here to download our eBook now.











