When the curtain was peeled back on the Icefog targeted espionage campaign in September, a new type of operator was unveiled, one that took the persistence out of advanced persistent threats (APT).
Researchers at Kaspersky Lab noted in uncovering Icefog that the attacks against the defense supply chain—including military contractors, ship builders, satellite operators, high tech companies and others in Japan and South Korea—were hit-and-run operations. Icefog was likely pulled off by a small group of attackers, one that used a mix of custom malware and attacks against known vulnerabilities in Windows and Mac OS X machines. The group knew its victim, knew what it needed from a campaign, and once that objective was achieved, the target was abandoned.
This goes against the grain of APT attacks where an organization is likely owned for a considerable amount of time as hackers pivot about internally under the cover of poor detection mechanisms or stolen credentials.
Icefog went dark after the September report, but researchers at Kaspersky Lab continued to dig into domains used in the attack that had been sinkholed by the security company, as well as looking at victim connections. This morning, additional details on the attack emerge that indicate the attackers also had a Java version of the campaign in their arsenal and used that to target three oil and gas companies in the United States.
The three companies were notified, and two have rid themselves of the infection, Kaspersky Lab said today. Individuals within these companies were likely duped by a phishing email that contained an Office exploit. Once inside, the attacks launched the Java-based attacks, dubbed Javafog, and also used a new command and control for backdoor communication. The Java attacks, Kaspersky Lab said, would be stealthier, and in another twist on this story, give the attackers a longer-term presence.
“The focus on the US targets associated with the only known Javafog C&C could indicate a US-specific operation run by the Icefog attackers; one that was planned to take longer than usual, such as, for instance, long term collection of intelligence on the target,” said the Kaspersky report. “This brings another dimension to the Icefog gang’s operations, which appear to be more diverse than initially thought.”
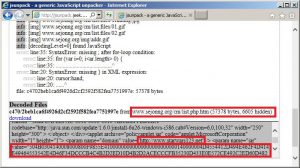
The latest pieces to the puzzle came together in October when Kaspersky Lab took over an Icefog domain called lingdona[.]com. The domain was originally hosted in Hong Kong and raised suspicions because it matched other known Icefog domains. Immediately, the domain began receiving connections every 10 seconds from a Java application, a new turn since other variants used IE User-Agent strings.
Unable to find a sample of the malware connecting to lingdona[.]com, the researchers were able to find a URL submitted to a public JSUNPACK service that was hosted on a known Icefog domain that referenced a Java applet called policyapplet.jar. The researchers decoded a long hexadecimal string parameter tagged to policyapplet reference and found another Java applet with a main class JavaTool.class that was compiled in 2010.
Once installed it, latches onto the computer’s registry for persistence at start up and then begins connecting to lingdona[.]com/news and sending system information. If the attackers determine this to be a target of value, they can then send back any number of commands ordering the malware encrypt and upload local files, migrate to a new command and control server URL, or execute a string specified and upload the results.
“It allows the attackers to control the infected system and download files from it,” the Kaspersky Lab report said. “Simple, yet very effective.”
This particular operation was small; eight IPs belonging to the three U.S. oil and gas companies connected to the lingdona domain. Researchers noted as well that two of the victims updated Java from Java 1.7 update 25 to update 45.