Attackers leveraged a Pony botnet controller to not only siphon away a large batch of account credentials but also to make off with over $200,000 in Bitcoin and other virtual currencies over a four month span, according to researchers this week.
It’s the second high profile instance of the Pony botnet seen over the last several months.
The source code for Pony, a botnet management interface, was initially leaked in the summer of 2013. The Trojan, whose sole purpose is to steal private data from infected machines, has been attributed to a sharp rise in data gathering attacks since.
According to a post on Trustwave SpiderLabs’ Anterior blog yesterday the botnet’s latest iteration is much more advanced and while the latest round of attacks only compromised a scant 85 wallets, they yielded roughly $200,000 in crypto-currency including Bitcoins (355), LiteCoins (280), PrimeCoins (33) and FeatherCoins (46).
“Despite the small number of wallets compromised, this is one of the larger caches of Bitcoin wallets stolen from end-users,” Daniel Chechik and Anat Davidi, two researchers with the company rationalized Monday.
The two assert that “it’s only natural” that Pony would begin to start going after people’s virtual wallets.
The Bitcoin theft is in addition to a slew of credentials, over 700,000, that Pony pilfered from September 2013 to January including:
- 600,000 website login credentials
- 100,000 email account credentials
- 16,000 FTP account credentials
- 900 Secure Shell account credentials
- 800 Remote Desktop credentials
While 700,000 may sound like a lot, the numbers are actually way down from a separate instance of Pony that SpiderLabs reported in December in which a campaign unearthed two million account credentials. Those usernames and passwords were mostly linked to Facebook, Google, and Twitter along with other social media sites but some were also linked to the ADP payroll service, something Chechik and Davidi warned at the time could “have direct financial repercussions.”
Also unlike the Pony incident in December, Trustwave researchers were able to glean a little more information about the geographical location of its victims this time around. In December the cybercriminals used a reverse proxy to drop the bots but this time the Pony bots interacted with a command-and-control (C+C) server, giving the researchers a much better idea about the campaign’s target. A chunk of the attacks were found taking aim at European users, with sites in Germany, Poland, Italy and the Czech Republic seeing 62 percent of the attacks.
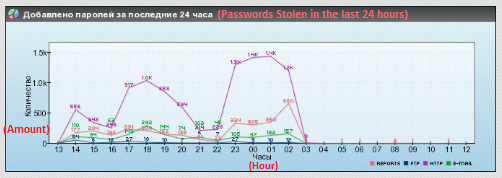
As the following graphic illustrates, after a series of up and down attacks the attackers decided to pull the plug on the most recent campaign at 3 a.m. on January 17.
Still though, Trustwave believes Pony isn’t done infecting users. Speaking to Reuters, Ziv Mador, a security research director with the company claims that while the company was able to disrupt its servers, he believes the crime ring is still operating and will continue to target virtual wallets in the future.
 Along with Bitcoin and the currencies listed above, Pony also looks for 30+ different types of virtual currency, including Anoncoin, Fastcoin and Luckycoin to name a few. Trustwave is warning users with unencrypted wallets associated with one of the listed currencies, right, that Pony may be looking for their money.
Along with Bitcoin and the currencies listed above, Pony also looks for 30+ different types of virtual currency, including Anoncoin, Fastcoin and Luckycoin to name a few. Trustwave is warning users with unencrypted wallets associated with one of the listed currencies, right, that Pony may be looking for their money.
Chechik and Davidi claim that while it’s difficult to say with certainty that the Bitcoin wallets associated with the attack were necessarily raided, it’s also tough to verify that the transfers associated with them were legitimate. When it comes down to it though, they were compromised in some shape or form.
It’s because of the uncertainty around the compromised wallets – there’s really no way to contact their owners – as a public service, the company has set up a tool to let users know if they’ve been implicated by Pony. Users can input their Bitcoin wallet public key or on another site, their email address, to see if their credentials have been compromised by the most recent campaign.
News of the most recent Pony attack comes in the wake of revelations that the largest and most popular Bitcoin exchange, Mt. Gox, is nearing collapse. Monday saw Mt. Gox’s chief executive resign from the Bitcoin Foundation, the company delete all of its tweets and take its site offline as word began to circulate that the service was expected to file for bankruptcy. Bitcoin loyalists fear the worst amid rumors that the company may have suffered a catastrophic theft to the tune of 744,408 Bitcoins, or $350 million over the last few months.