A variant of the notorious Locky ransomware is part of a large scale email-based campaign managing to slip past the defenses of some unsuspecting companies.
Beginning on Aug. 9, and lasting three days, ransomware called IKARUSdilapidated landed in tens of thousands of inboxes with email that contains little to no content along with a malicious dropper file attachment, according to Comodo Threat Intelligence Lab.
“The attachment is an archive file, with the name ‘E 2017-08-09 (580).vbs’ where 580 is a (variable) number changing for each email and ‘vbs’ is an extension which varies as well,” said Comodo. “The subjects are similar “E 2017-08-09 (580).tiff” where the extension is a document (doc), archive file (zip), pdf or image file (jpg, tiff).”
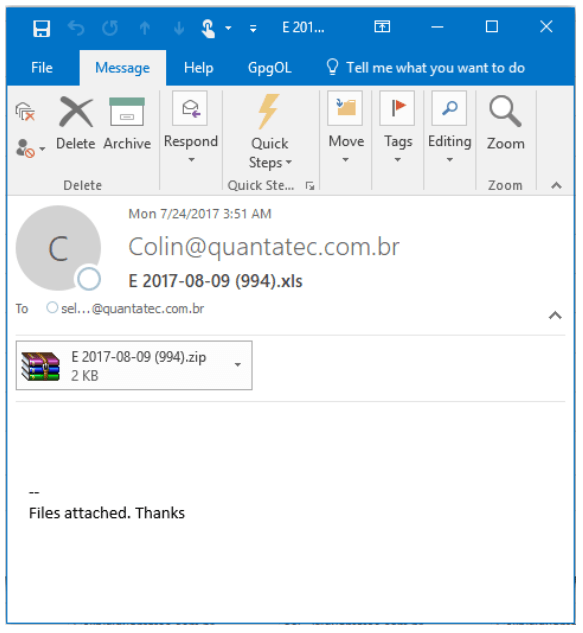 If the attachment is executed, it downloads the IKARUSdilapidated ransomware. The name of the ransomware strain is derived from a text string found in the code of the malicious file downloaded by the dropper.
If the attachment is executed, it downloads the IKARUSdilapidated ransomware. The name of the ransomware strain is derived from a text string found in the code of the malicious file downloaded by the dropper.
“When the user opens the attached document, it appears to be full of garbage, and it includes the phrase ‘Enable macro if data encoding is incorrect’ —a social engineering technique used in this type of phishing attack. If the user does as instructed, the macros then save and run a binary file that downloads the actual encryption trojan,” according to a preliminary analysis by Comodo.
“As a new malware variant, it is read as an ‘unknown file’ and is allowed entry by organizations not using a ‘default-deny’ security posture (which denies entry to all unknown files until it is verified that they are ‘good’ files and are safe to enter the IT infrastructure),” Comodo said.
Researchers say IKARUSdilapidated is a variant of Locky because they share many of the same characteristics such as encrypted filenames converted to a unique 16-letter and number combination with the .locky file extension.
According to the ransomware message, files are encrypted with “RSA-2048 and AES-128 ciphers.”
Locky is notorious for its effectiveness and profitability. Over the past two years, Locky has extorted more than $7.8 million in payments from victims, according a recent study by Google, Chainalysis, UC San Diego, and the NYU Tandom School of Engineering.
Post-infection, a message is displayed on the victim’s desktop instructing them to download the Tor browser and visit a payment site to fork over a ransom of between 0.5 and 1 in bitcoin ($600 to $1,200) for files to be decrypted.
Analysis on a sample of 62,000 emails linked to the IKARUSdilapidated campaign by Comodo revealed a sophisticated adversary utilizing 11,625 different IP addresses spread across 133 different countries such as Vietnam, India, Mexico, Turkey, and Indonesia.
“When the team checked the IP range owners, we see that most of them are telecom companies and ISPs. This tells us the IP addresses belong to infected, now-compromised computers,” researchers wrote in the yet to be published report on the ransomware.
Researchers say the size, scope and quality of the botnet behind the campaign suggests a practiced adversary. “It also shows the increasing sophistication, organization and size of new ransomware attacks and adds more credence to the call to act on the recommendation of security experts everywhere,” they wrote.
Over the past six months, Locky has been extremely active. In April it leveraged the Necurs botnet to send massive bursts of phishing emails. In that specific campaign, spotted by Cisco Talos, researchers warned Locky is borrowing effective techniques from the credential-stealing malware Dridex, which has become adroit at outsmarting sandbox mitigation efforts.
In February, Microsoft’s Malware Protection Center spotted malicious email campaigns using .lnk attachments to spread Locky ransomware and the Kovter click-fraud Trojan, the first time criminals have simultaneously distributed both pieces of malware.










