A campaign aimed at Mac users is spreading the XCSSET suite of malware, which has the capability to hijack the Safari web browser and inject various JavaScript payloads that can steal passwords, financial data and personal information, deploy ransomware and more.
Infections are propagating via Xcode developer projects, researchers noted; the cybercriminals behind the campaign are injecting the malware into them, according to Trend Micro. Xcode consists of a suite of free, open software development tools developed by Apple for creating software for macOS, iOS, iPadOS, watchOS and tvOS. Thus, any apps built on top of the projects automatically include the malicious code.
The initial discovery of the threat came when “we learned that a developer’s Xcode project at large contained the source malware — which leads to a rabbit hole of malicious payloads,” according to an analysis [PDF] from Trend Micro, released on Friday. “The threat escalates when affected developers share their projects via platforms such as GitHub, leading to a supply-chain-like attack for users who rely on these repositories as dependencies in their own projects. We have also identified this threat in other sources including VirusTotal and Github, which indicates this threat is at large.”
The initial payload tucked into the projects comes in the form of a Mach-O executable. The researchers were able to trace an infected project’s Xcode work data files and found a hidden folder containing Mach-O, located in one of the .xcodeproj files.
When executed, the Mach-O malware connects to a hardcoded command-and-control (C2) server address, and begins to take screenshots of the current desktop at the rate of once a minute; once a new screenshot is taken, the previous one is deleted, the analysis noted.
However, Mach-O’s main purpose is to download and run the second-stage payload, an AppleScript file called main.scpt, which carries out most of the malicious behavior.
The research noted that when the “Main” payload is executed, it first harvests basic system information of the infected user, then kills certain running processes if present, including various browsers (Opera, Edge, Firefox, Yandex and Brave) as well as “com.apple.core,” “com.oracle.java” and others.
The payload then gets down to real business, obtaining and compiling malicious code into a Mac app package. The package name is mapped to an installed, well-known application name, such as Safari. Researchers detailed that it then replaces the app’s corresponding icon file and “Info.plist” to make the fake app look like a real, normal app –and thus, users go to open the normal app, the malicious one opens instead.
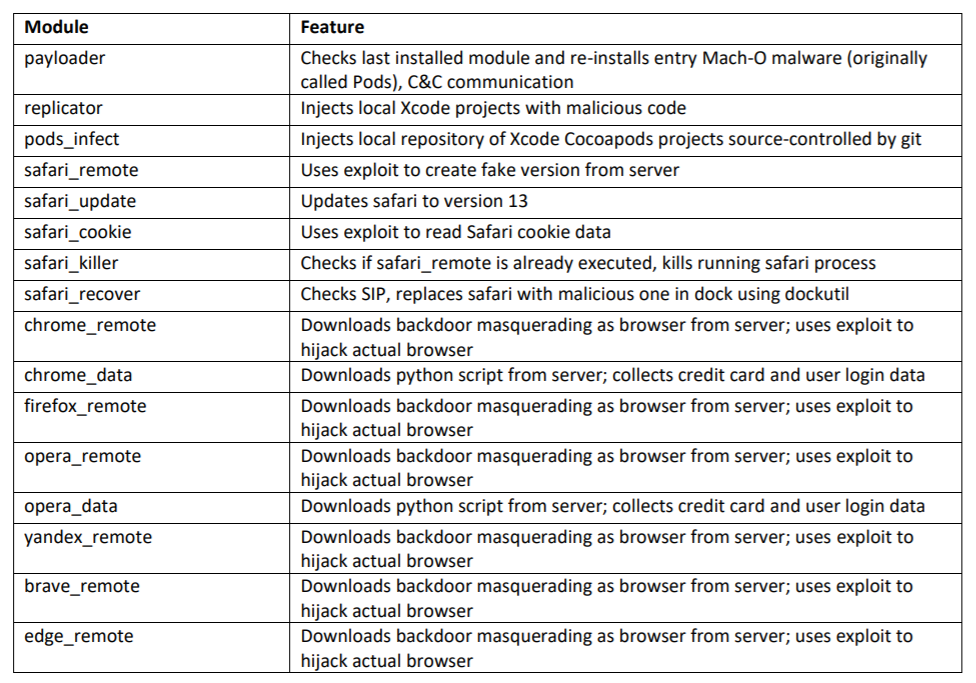
According to the analysis, when opened, the fake app package’s malicious capabilities are then executed, in the form of deploying a raft of modules used for various goals: Taking over browsers; stealing information from installed apps including Evernote, Skype and Telegram; and spreading to other hosts. It also has ransomware modules that it can deploy and dozens of other capabilities. Below is a partial list:
The malware also uses a zero-day vulnerability in Data Vault that allows it to bypass macOS’ System Integrity Protection (SIP) feature, in order to steal Safari cookies; and a Safari for WebKit Development zero-day that allows universal cross-site scripting (UXSS), which clears the way to inject JavaScript into the development version of Safari and other browsers without worrying about sandboxing.
In the latter case, the malware injects the malicious JavaScript code into a current browser page. The attackers can then manipulate browser results; manipulate and replace found Bitcoin and other cryptocurrency addresses; replace a Chrome download link with a link to an old version package; steal Google, Yandex, Amocrm, SIPmarket, PayPal and Apple ID credentials; steal credit-card data linked in the Apple Store; prevent the user from changing passwords and also record new passwords; and take screenshots of certain accessed sites.
Threatpost has reached out to Trend Micro to see if the zero-days have been reported and if any further particulars are available on them – scant details were offered in the analysis.
The firm said that it was able to collect a list of victim IP addresses from the C2; this consisted of 380 individual infected targets; most were in China and India. Trend Micro noted that it observed the XCSSET malware affecting two Xcode projects so far, but warned that the campaign is very likely to spread.
“With the OS X development landscape rapidly growing and improving – as proven by news on the latest Big Sur update, for instance – it’s no surprise that malware actors now also leverage both aspiring and seasoned developers alike for their own benefit,” Trend Micro concluded. “Project owners should continue to triple-check the integrity of their projects in order to definitely nip unwarranted problems such as a malware infection in the future.”
It’s the age of remote working, and businesses are facing new and bigger cyber-risks – whether it’s collaboration platforms in the crosshairs, evolving insider threats or issues with locking down a much broader footprint. Find out how to address these new cybersecurity realities with our complimentary Threatpost eBook, 2020 in Security: Four Stories from the New Threat Landscape, presented in conjunction with Forcepoint. We redefine “secure” in a work-from-home world and offer compelling real-world best practices. Click here to download our eBook now.