New ransomware has surfaced that targets state and local government agencies, and educational institutions that are less likely to have big budgets to ward off or mitigate threats, according to researchers.
The ransomware, called MarsJoke, was detected in a large-scale email campaign last week that was being delivered via the Kelihos botnet, Proofpoint said.
“Emails contained URLs linking to an executable file named ‘file_6.exe’ hosted on various sites with recently registered domains, apparently for the purpose of supporting this campaign,” Proofpoint said Saturday in a blog post.
This technique differs from a more typical malicious macro-based document attacks used commonly with variants such as Locky. The hallmark of the MarsJoke campaign is its convincing spam emails that hijack the branding of popular air carriers and shipping companies. Typical messages read: “Make no difficulty to use the tracking number provided in the file below.”
The file (file_6.exe), once downloaded and executed, installs the MarsJoke malware that promptly encrypts files, but does not change original file extensions. However, during the encryption process, file name extensions are replaced temporarily with the “.a19” and “.ap19”, Proofpoint said.
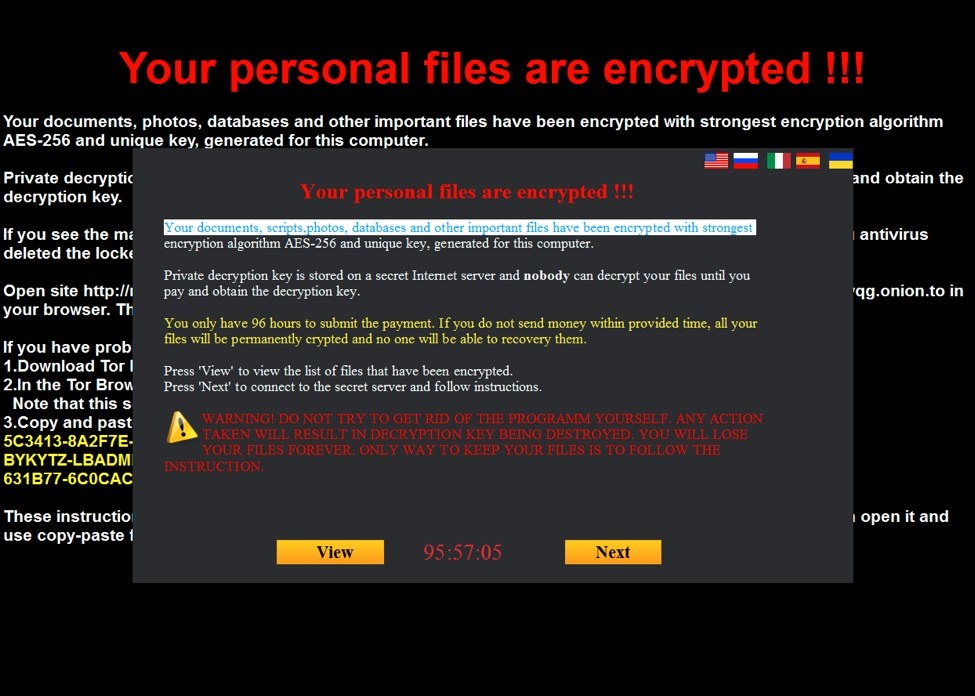
Those infected with MarsJoke have their Widows desktop background changed to black with the displayed ransom message, below. A dialogue box indicates “documents, scripts, photos and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this computer,” according to a screenshot of the ransomware provided by Proofpoint.
Ransom messages are delivered in English by default, Proofpoint said, but also include Russian, Italian, Spanish and Ukrainian. Victims are told they have 96 hours to submit a ransom of 0.7 bitcoin ($320) before files are deleted.
Attackers behind MarsJoke are stealing a page from the CryptFile2 ransomware playbook, Proofpoint said. That CryptFile2 ransomware spam campaign was also distributed via the Kelihos botnet. Similar to MarsJoke, CryptFile2 also used embedded malicious URLs targeted at similar government and educational institutions that also led recipients to download malicious files.
Primary differences between the two is that with CryptFile2, the malicious files were Word documents with malicious macros and the encryption algorithms were different. Proofpoint named MarsJoke based on a string discovered within the malware code “HelloWorldItsJokeFromMars.”
“MarsJoke does not appear to be ‘just another ransomware,’ though. The message volume and targeting associated with this campaign bear further monitoring as attackers look to monetize new variants and old strains saturate potential victims,” Proofpoint wrote.