Nearly three months after it was spotted for sale in a Russian hacker forum, the Mazar bot has been put to use in active attacks targeting Android devices.
Researchers at Heimdal Security said on Friday the bot is being sent to Android users via SMS and MMS messages and if the victim executes the APK, the bot roots the phone and gives the attacker extensive capabilities on the compromised device.
The malware allows the attackers to spy on almost every activity capable on an Android device, including establishing a backdoor connection, sending premium SMS messages, reading texts sent to the device, including bank authentication PINs. Heimdal researchers said the attackers’ root access can also allow them to erase the phone.
The researchers added that the malware won’t install on devices set to the Russian language option.
“Until now, Mazar BOT has been advertised for sale on several websites on the Dark Web, but this is the first time we’ve seen this code be abused in active attacks,” Heimdal said in its report. “Attackers may be testing this new type of Android malware to see how they can improve their tactics and reach their final goals, which probably is making more money (as always).”
The attackers’ original SMS tries to entice the user to click on an embedded link which leads the victim to http://www[.]mmsforyou[.]net/mms[.]apk. The APK starts by installing Tor—grabbed from legitimate sources—on the device and then tries to connect to a .onion server. It then sends an automated SMS to a number in Iran with a benign message and the device’s location data, Heimdal said.
In addition to rooting the phone, Mazar also installs the Polipo HTTP proxy, which exposes the device to man-in-the-middle attacks, putting the attacker between the phone and a web-based service, Heimdal said. It can also infect a version of the Chrome browser installed on the device, allowing the attackers to control the phone’s keys, turn on sleep mode or save actions in the phone’s settings.
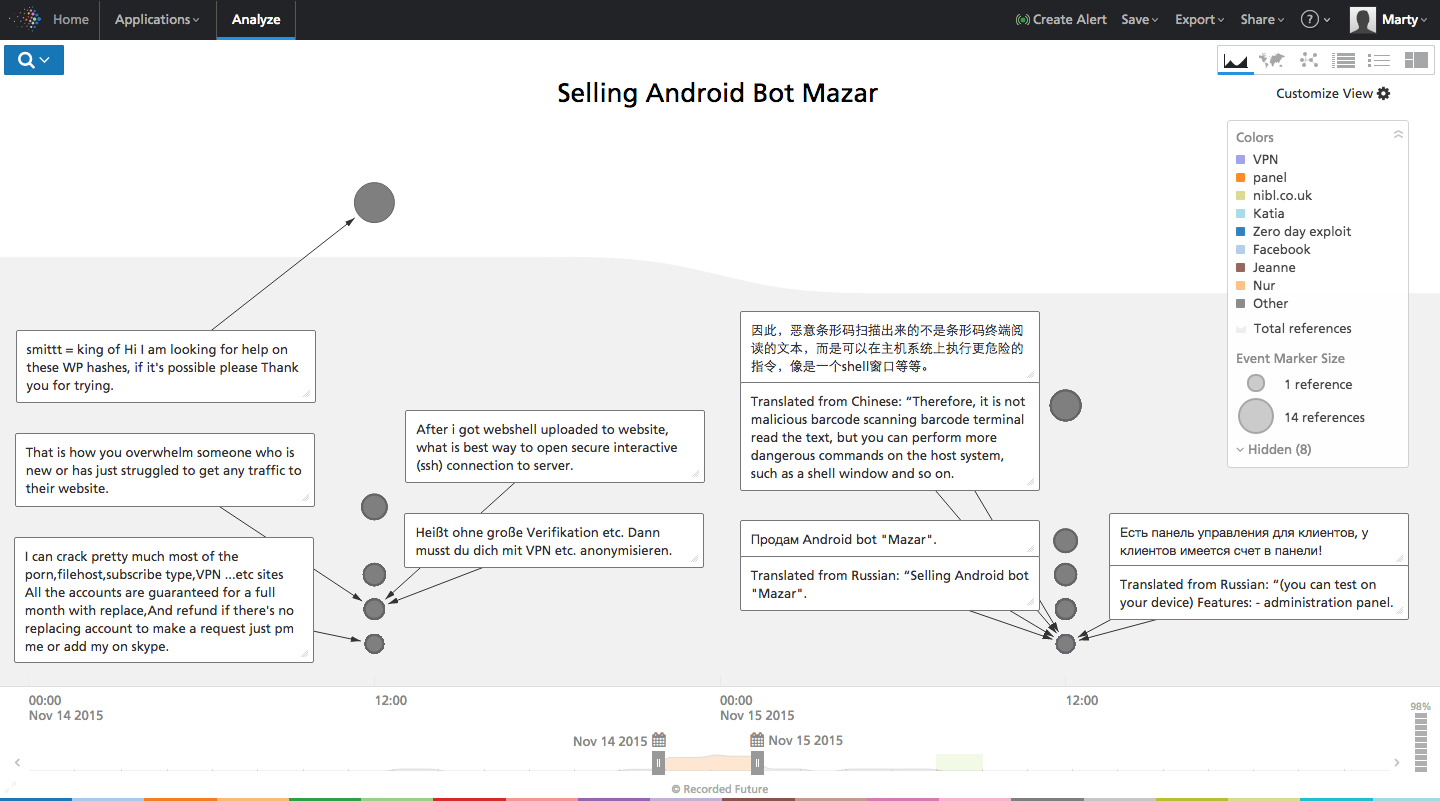
Researchers at Recorded Future saw the bot advertised, above, on a Russian forum known for selling malware used by cybercriminals, and panels make mention of a prominent Russian financial services company Sberbank. At the time, they were not sure of the bot’s authenticity and whether it was in the wild. Heimdal said last week this is the first time the malware had been spotted in active attacks.