 Microsoft’s February batch of security patches will be a biggie — 13 bulletins with fixes for a whopping 26 vulnerabilities.
Microsoft’s February batch of security patches will be a biggie — 13 bulletins with fixes for a whopping 26 vulnerabilities.
According to an advance notice from the Redmond, Wash. software
vendor, five of the 13 bulletins will be rated “critical” because of
the risk of remote code execution attacks.
The majority of the vulnerabilities affect the company’s flagship
Windows operating system while the others will deal with security holes
in the Microsoft Office productivity suite.
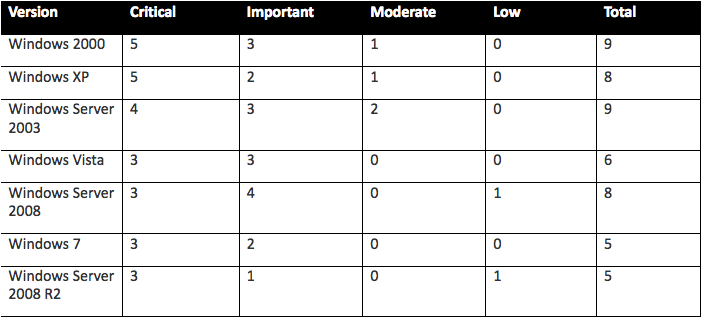
The chart below details the affected OS versions and severity ratings for
the bulletins, which will be released next Tuesday (February 9, 2010).
While the details of the vulnerabilities will be kept a secret until
Patch Tuesday, Microsoft says one of the bulletins will address a known privilege escalation flaw (see advisory) in the Windows kernel.
That vulnerability was publicly disclosed by a Google security
researcher who released released code to demonstrate the risk of
privilege escalation attacks against affects every release of the
Windows NT kernel — from
Windows NT 3.1 (1993) up to and including Windows 7 (2009).
(Click image for larger version)
Microsoft has already warned that
a malicious hacker could exploit this vulnerability to run
arbitrary code in kernel mode. For an attack to be successful, the
attacker must have valid logon credentials. The flaw does not affect
Windows operating systems for x64-based and Itanium-based computers.
There are at least two open, publicly known vulnerabilities that will NOT be patched this month. They are the most recent Internet Explorer data leakage bug (see advisory) details at Black Hat DC and a denial-of-service vulnerability in the Server Message Block (SMB) protocol.
Exploit code for the SMB flaw was released by researcherFollowing the publication of stop responding until manually restarted.









