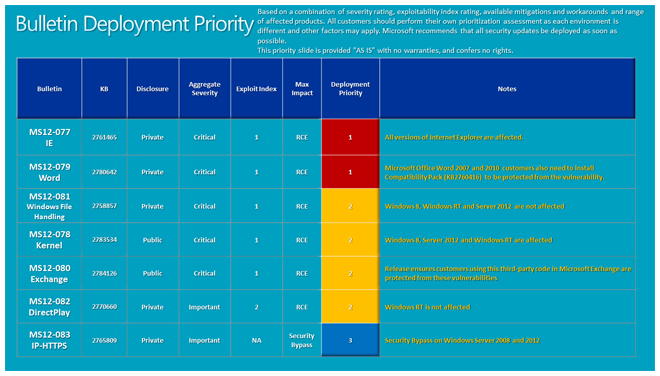
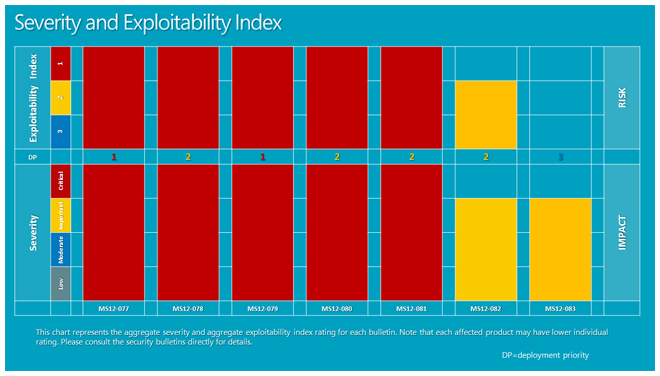
A rare critical Microsoft Word vulnerability was patched today by Microsoft, one of seven security updates pushed out repairing 11 flaws in its December security update.
A rare critical Microsoft Word vulnerability was patched today by Microsoft, one of seven security updates pushed out repairing 11 flaws in its December security update.
The Word vulnerability earned a critical rating because the Outlook email client uses Word to display documents in the Outlook preview pane and therefore removes the need for user interaction to trigger an exploit.
Generally, remote execution flaws in Office products don’t warrant critical ratings because they require some kind of action from the user. An attacker could also trick a user into visiting a website hosting a malicious RTF file or advertisement, for example, which would exploit the vulnerability.
The vulnerability occurs in the way Office parses specially crafted Rich Text Format messages, the Microsoft advisory said.
“An attacker who successfully exploited this vulnerability could take complete control of an affected system,” the Microsoft advisory said. “An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
Word 2007 and 2010 are vulnerable, as are supported versions of Microsoft Word Viewer, Microsoft Office Compatibility Pack, and Microsoft Office Web Apps.
“A potential workaround is to manually configure the preview pane in Outlook’s Trust Center to use plain text only, but one loses a significant amount of functionality that way,” said Wolfgang Kandek, CTO at Qualys.
Microsoft also patched three critical remote execution vulnerabilities in Internet Explorer 9 and 10 running on all platforms from Vista to Windows 8.
The first two vulnerabilities–an InjectHTMLStream Use After Free vulnerability and a CMarkup Use After Free vulnerability–exist in the way IE access objects in memory that have been deleted. “The vulnerabilities may corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user,” Microsoft said.
The third IE flaw is an Improper Ref Counting Use After Free vulnerability, which occurs in the way the browser accesses objects that have not been correctly initialized or has been deleted.
Critical flaws were also repaired in Microsoft Exchange Server, the most severe in the server’s WebReady Document Viewing feature which could lead to remote code execution as the LocalService account should a user preview a malicious file in Outlook Web App. Exchange Server 2007 and 2010 are affected.
There is also a denial-of-service vulnerability in Exchange Server that could occur when it improperly handles RSS feeds causing the information store service to become unresponsive. Exchange databases could dismount in the process and become corrupted.
Two vulnerabilities were patched in Windows as well, the most severe a remote execution flaw that could occur if a malicious document or webpage manages to embed TrueType or Open Type font files. Users would have to be led to the site via a spam or phishing message, Microsoft said.
The final critical remote execution vulnerabilities patched by Microsoft is a Filename Parsing vulnerability. Malicious filenames can corrupt memory enabling an attacker to remotely execute code on an infected machine. Windows XP, Vista and 7 are affected, as are Windows Server 2003 and 2008.
“The attacker would have to control an SMB or WebDAV fileserver that the target accesses in order to exploit the vulnerability,” Qualys’ Kandek said. “A good mitigation for these types of attacks would be firewall SMB filesharing and WebDAV on the outbound firewall or proxy to restrict the use of these protocols to the internal network and limit their use on the Internet.”
Microsoft also issued a pair of bulletins it rated important for Windows systems. The first could bypass certificate validation checks in the OS if an attacker uses a revoked certificate to an IP-HTTPS server for Microsoft DirectAccess deployments. “To exploit the vulnerability, an attacker must use a certificate issued from the domain for IP-HTTPS server authentication,” the advisory said. “Logging on to a system inside the organization would still require system or domain credentials.”
Windows Server 2008 R2 and Windows Server 2012 are affected.
The final December bulletin is also a remote execution flaw in Microsoft DirectPlay that could be triggered if an attacker convinces a user to view a malicious Office document with embedded content. The heap overflow vulnerability occurs in the way DirectPlay handles specially crafted content. DirectPlay is a network protocol in DirectX used by computer game developers to create multiplayer games. DirectX 9.0, 10.1 and 11.1 are vulnerable, Microsoft said.
Microsoft also revised a September update for vulnerabilities in Adobe Flash Player embedded in Internet Explorer 10, making it a cumulative update for Flash in IE 10.