An online database belonging to insurance marketing website MedicareSupplement.com was found exposing more than 5 million records with personal information.
MedicareSupplement.com is a U.S.-based marketing site that allows users to find supplemental medical insurance available in their area. Researchers on Thursday said that they found a publicly-available MongoDB database on May 13 that had been online for several days. The exposed data appeared to be part of the website’s marketing leads database and did not have a password or any authentication protecting it.
“While I have not seen any ransom notes or suspicious activity, the IP in question has been first indexed by a public search engine BinaryEdge on May 10, and closed down 5 days later,” security researcher Bob Diachenko, who discovered the database along with researchers at Comparitech, told Threatpost. “However, for a MongoDB being in the wild for such a long time there is a high chance it has been accessed by other actors.”
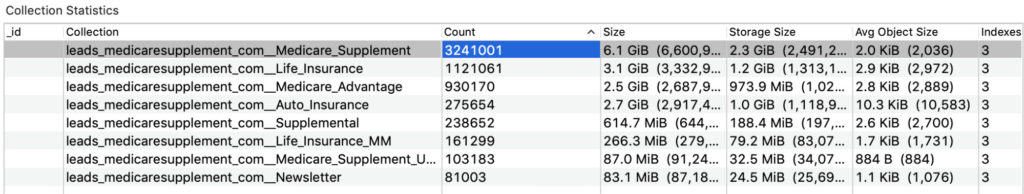
Specifically exposed were about 5 million records containing the personal data of customers. That data included first and last names, addresses, IP addresses, email addresses, dates of birth, and gender. Also included was an array of marketing-related information for customers, including lead duration and clicks.
Around 239,000 records also indicated insurance interest areas for customers – for instance, medical insurance (i.e. cancer insurance), as well as life, auto, and supplemental insurance.
Researchers said that they disclosed the vulnerable database to MedicareSupplement.com, after which the database access was disabled and a property security configuration was installed.
While researchers are not sure whether anyone else was able to access the data, they warned that the customers of the website whose information was exposed, particularly those whose records included insurance interest area, could be at risk of spam, targeted phishing, and fraud due to the exposed data.
Accidental data exposure continues to be an issue plaguing companies who do not sufficiently secure their MongoDB or NoSQL databases.
 This week, for instance, three publicly-accessible cloud storage buckets from data management company Attunity leaked more than a terabyte of data from its top Fortune 100 customers – including internal business documents, system passwords, sensitive employee information.
This week, for instance, three publicly-accessible cloud storage buckets from data management company Attunity leaked more than a terabyte of data from its top Fortune 100 customers – including internal business documents, system passwords, sensitive employee information.
In May, IT services provider HCL Technologies inadvertently exposed passwords, sensitive project reports and other private data of thousands of customers and internal employees on various public HCL subdomains. In April, hundreds of millions of Facebook records were found in two separate publicly-exposed app datasets.
“I have previously reported that the lack of authentication allows the installation of malware or ransomware on the MongoDB servers,” said Diachenko. “The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place, criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.”