Back in the dark days of dial-up connectivity, attackers wouldn’t bother compromising home computers as bots to be used in distributed denial-of-service. The lack of bandwidth made PCs persona non grata in the DDoS world. Instead, attackers targeted Web servers, the only machines with the high-speed broadband connections to make DDoS viable.
In the years since, broadband has literally come home and personal machines have been compromised by the millions for everything from spam to flood attacks against websites and online services.
Yet in 2012, attackers went back to the future, opting again to use Web servers in the year’s most high-profile DDoS attacks against almost every major U.S. financial institution. The results were crippling 70 Gbps attacks against online banking services hosted by Bank of America, PNC, Wells Fargo and a number of others that dwarfed run-of-the-mill DDoS attacks by seven times the attack volume.
“The used compromised servers sitting in a data center with high-powered bandwidth,” said Gary Stockrider, solutions architect with Arbor Networks. “They were generating large, high packet-per-second attacks using a small number of hosts. Rather than seeing tens of thousands of hosts, we’re seeing hundreds.”
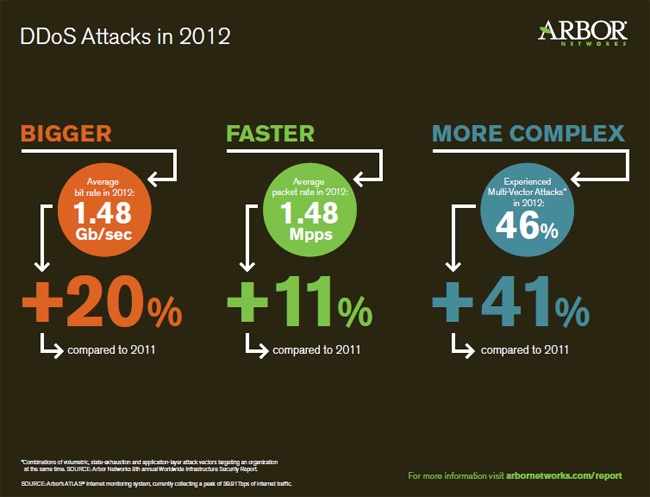
Arbor Networks’ eighth annual Infrastructure Security Report, released today, highlights a number of attack trends that emerged in 2012, led by this spike in the size and volume of DDoS attacks. Attackers sprayed attacks ranging anywhere from 60 Gbps to 100 Gbps, exponentially higher than the average of 1 Gbps seen in traditional DDoS attacks. Attackers are targeting not only the HTTP layer, but also DNS, causing costly outages to businesses along the way.
The bank attacks, which dominated headlines at different times last fall through the end of 2012, were reportedly in response to a series of movie trailers posted to YouTube for the film “Innocence of Muslims.” The group behind the attacks, Izz ad-Din al-Qassam, said their actions were in retaliation for the portrayal of Muslims in the film.
The attackers were able to hit multiple targets simultaneously with massive volumes of bad traffic.
“They were able to generate attacks without command-and-control,” Stockrider said. “They had a handful of attackers each managing multiple servers generating massive attacks. It gave them the ability to be nimble. As soon as an attack was mitigated, they were able to switch gears and change attack vectors. They would flood HTTP or DNS, things they know network operators have to let through.”
Those surveyed by Arbor for its annual report suffered an increased number of attacks combining application and network layer attacks. These multilayered attacks are difficult to counter because they require multiple solutions across a data center, Arbor said, adding that 46 percent of respondents reported such attacks, up from 27 percent in 2011. Also, half of the respondents said their data centers had suffered DDoS attacks, almost all of those adding that DDoS is a regular occurrence.
In the meantime, 88 percent of respondents reported operational expenses as the top business impact of attacks on data centers, followed by customer churn and revenue loss.
As for DNS, much of that infrastructure still operates without much security in place. Respondents reported a lack of visibility and dedicated security teams to DNS ; 21 percent said they do not restrict access to DNS recursors, leaving environments open to reflective amplification attacks. Meanwhile, those who have deployed DNSSEC are not reporting issues, Arbor said.
“They’ve gotten pretty good at protecting their own infrastructure, but the motivation is not there to stop infrastructure from being used to attack someone else,” Stockrider said. “If it doesn’t impact them, it’s hard to justify the investment there.”
Arbor said its report was culled from data collected by its ATLAS service from October 2011 through September 2012; 130 enterprise, network operators and service providers took part, primarily network or security operations engineers.










