Graphics chipmaker Nvidia has fixed two high-severity flaws in its graphics drivers. Attackers can exploit the vulnerabilities to view sensitive data, gain escalated privileges or launch denial-of-service (DoS) attacks in impacted Windows gaming devices.
Nvidia’s graphics driver (also known as the GPU Display Driver) for Windows is used in devices targeted to enthusiast gamers; it’s the software component that enables the device’s operating system and programs to use its high-level, gaming-optimized graphics hardware.
One of the vulnerabilities, CVE-2020-5962, exists in the Nvidia Control Panel component, which provides control of the graphics driver settings as well as other utilities installed on the system. The flaw could allow an attacker with local system access to corrupt a system file, which may lead to DoS or escalation of privileges, according to Nvidia’s Wednesday security advisory.
Another vulnerability (CVE‑2020‑5963) exists in the CUDA Driver, a computing platform and programming model invented by Nvidia. The issue stems from improper access control in the driver’s Inter Process Communication APIs. It could lead to lead to code execution, DoS or information disclosure.
The display driver also contains four medium-severity flaws, existing in the service host component (CVE‑2020‑5964), the DirectX 11 user mode driver (CVE‑2020‑5965), the the kernel mode layer (CVE‑2020‑5966) and the UVM driver (CVE‑2020‑5967).
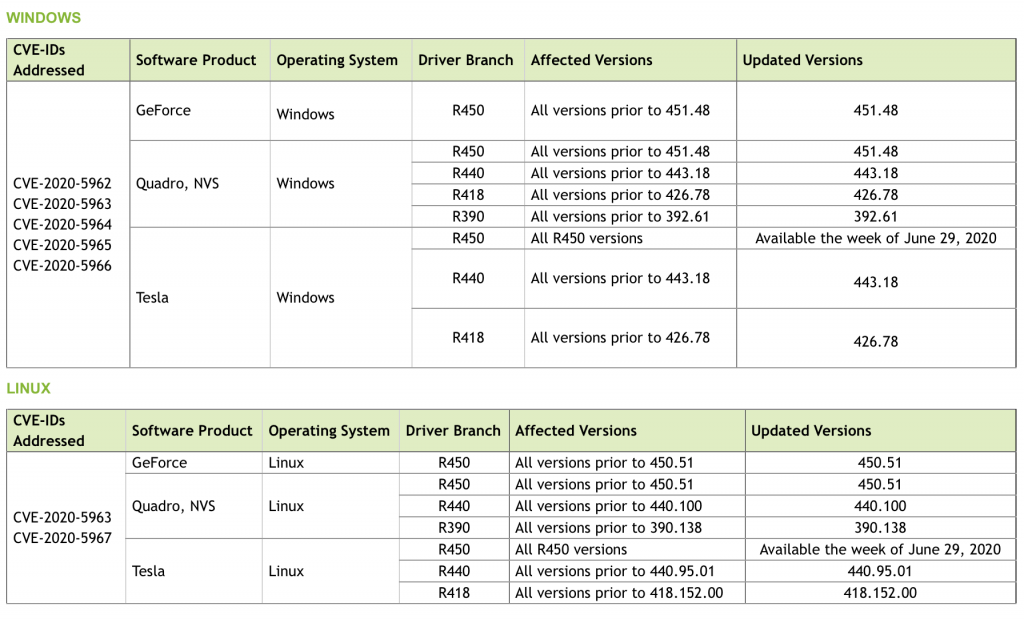
Various drivers are affected for Windows and Linux users, including ones that use Nvidia’s GeForce, Quadro and Tesla software. A full list of affected – and updated – versions are below.
Nvidia also stomped out four high-severity flaws in its Virtual GPU (vGPU) manager, its tool that enables multiple virtual machines to have simultaneous, direct access to a single physical GPU, while also using Nvidia graphics drivers deployed on non-virtualized operating systems.
In this case, the software does not restrict (or incorrectly restricts) operations within the boundaries of a resource that could be accessed by using an index or pointer, such as memory or files. That may lead to code execution, DoS, escalation of privileges or information disclosure (CVE‑2020‑5968), warned Nvidia.
Another flaw stems from the vGPU plugin validating shared resources before using them, creating a race condition which may lead to DoS or information disclosure (CVE‑2020‑5969). And in another glitch, input data size is not validated in the vGPU plugin, which may lead to tampering or denial of service (CVE‑2020‑5970).
The final vGPU flaw (CVE‑2020‑5971) stems from the software reading from a buffer by using buffer access mechanisms (such as indexes or pointers) that reference memory locations after the targeted buffer. This could lead to code execution, DoS, escalated privileges, or information disclosure.
It’s only the latest slew of patches that Nvidia has issued. Earlier in March, the company fixed several high-severity vulnerabilities in its graphics driver, which can be exploited by a local attacker to launch DoS or code-execution attacks. Last year, Nvidia issued fixes for high-severity flaws in two popular gaming products, including its graphics driver for Windows and GeForce Experience. The flaws could be exploited to launch an array of malicious attacks – from DoS to escalation of privileges. Also in 2019, Nvidia patched another high-severity vulnerability in its GeForce Experience software, which could lead to code-execution or DoS of products, if exploited.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.