In a world where everything is an “as-a-service,” it’s no surprise that ransomware-as-a-service (RaaS) is a hot ticket on the Dark Web. FortiGuard Labs has observed at least two significant ransomware families – Sodinokibi and Nemty – now being deployed as RaaS solutions.
Meanwhile, cybercriminals are also refining existing malware to evade detection and deliver increasingly sophisticated and malicious payloads, such as we’ve seen in the evolution of the Emotet malware, a popular and successful banking trojan.
Let’s explore the recent discoveries made by the Fortiguard Lab teams on the transformation of these malware families and ways to safeguard networks.
The New Face of Ransomware
With significant financial incentives to spur them on, cybercriminals continually invent more sophisticated forms of ransomware – and ways of distributing it. For instance, the cybercriminals behind the prolific GandCrab ransomware strain reportedly made more than $2 billion in less than two years before saying that they were “retiring” recently (a claim that some researchers refute). Many of those illegitimate gains came from their use of a RaaS model to distribute the malware. By establishing a network of affiliate partners, GandCrab’s authors were able to spread their ransomware widely and scale earnings dramatically in the process.
We noticed last quarter that Sodinokibi and Nemty, two other significant ransomware families, were being deployed in a similar manner, suggesting the RaaS model is gaining ground. Sodinokibi (a.k.a. Sodin, REvil) surfaced shortly before GandCrab’s authors supposedly retired; it quickly became one of the biggest ransomware threats in Q3. It was used in multiple targeted attacks on major organizations, including nearly two dozen local governments in one state.
Cybercriminals distributed Sodinokibi in a number of ways, including exploit kits, phishing and the exploitation of software vulnerabilities. We believe it is unique among ransomware strains in exploiting a remote code-execution vulnerability to infect systems.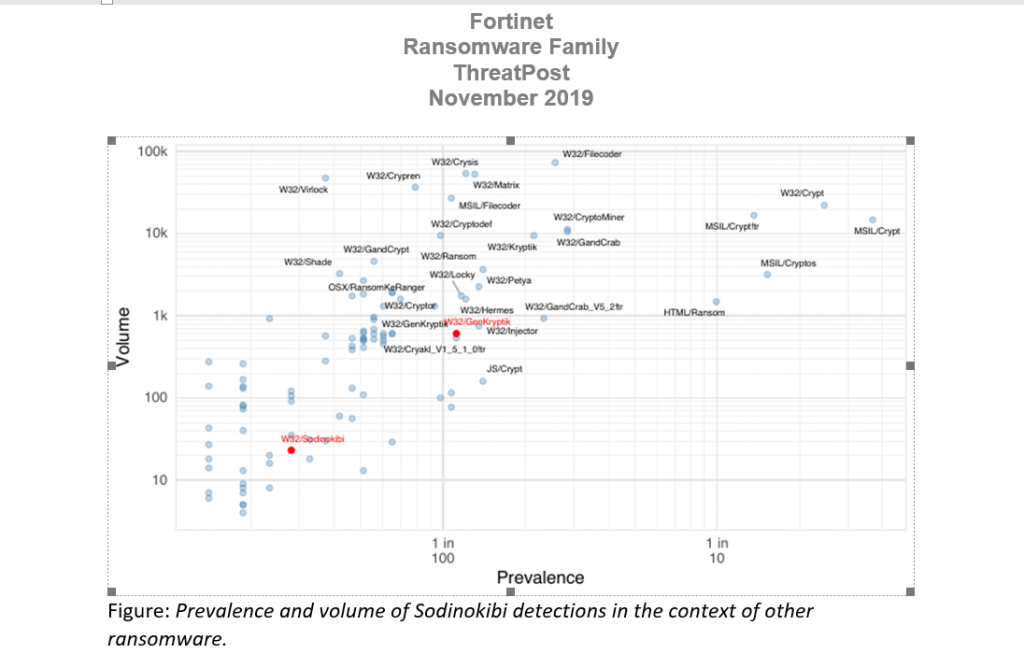
These examples demonstrate that ransomware continues to be a clear and present danger to enterprise organizations. Many threat actors have eschewed mass-volume spray-and-pray consumer attacks for more carefully planned, targeted ones aimed at maximizing disruption for companies. By using an RaaS model, the authors of malware such as Sodinokibi and Nemty are significantly lowering the bar for launching such attacks. That lowered bar makes this particular form of cybercrime accessible and profitable for a larger pool of bad actors.
10 Ways to Take Action
How can you protect your organization from increasingly sophisticated ransomware? Here are 10 practical steps to implement now.
- Maintain patching and updating for your operating systems, devices and software.
- Consistently run the latest updates for your device and network antivirus, IPS and anti-malware tools.
- Back up your systems regularly, and store that backup offline on a separate device as part of a recovery plan.
- Employ security tools that check email attachments, websites and files for malware, which can block potentially compromised advertisements and social media sites that have no business relevance. These tools should include sandbox functionality, so that new or unrecognized files can be executed and analyzed in a safe environment.
- Use permissions and privileges so that the fewest number of users have the potential to infect business-critical applications, data or services.
- Create and enforce a bring-your-own-device security policy that inspects and blocks devices that do not meet your standards for security.
- Make use of application whitelisting, which prevents unauthorized applications to be downloaded or run, where possible.
- Keep in mind that human beings are the most vulnerable link in your security chain, and you will need to plan around them.
- To prevent an infection in one area from easily spreading to another, segment your network into security zones.
- Use forensic analysis tools so that post-attack, you can identify a) where the infection came from, b) how long it has been in your environment, c) that you have removed all of it from every device and d) that you can ensure it doesn’t come back.
Prepare to Protect
As cybercriminals continue launching new malware services to expand their earning potential, enterprises have to stay on their toes. The latest threat data reveals that bad actors are focusing their attacks for maximum impact and profit using increasingly stealthy and unexpected methods. Use the steps listed above to protect your organization from the new crop of ransomware threats.
Derek Manky is chief of security insights and global threat alliances, Fortinet.
Enjoy additional insights from Threatpost’s InfoSec Insider community by visiting our microsite.










