After a two year absence, IBM X-Force is reporting [iss.net] a significant spike in image-based spam.
“Since March 20th, we have been witnessing a rebirth of image-based spam. At first, we saw a small trial of image-based spam, reaching 5-10%. Then, in late April, we saw another blast (this time a much bigger effort) reaching 15-22% of all spam, according to researchers Ralf Iffert and Holly Stewart.
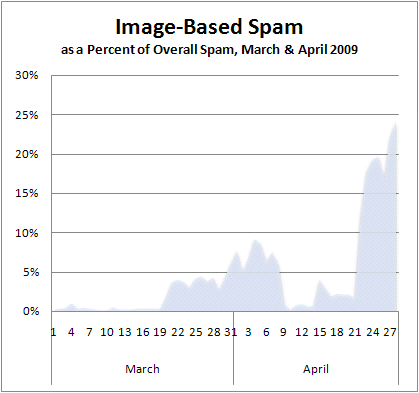
One interesting side note: In the last spike in 2007, the overwhelming majority of image-spam content was pushing penny stocks [zdnet.com] as part of pump-and-dump schemes. Today, the cybercriminals behind image-spam runs are selling drugs.
Some characteristics:
- Most of them are of pharmaceutical nature, advertising drugs, pills, etc.
- Only a few of them use random pixels, and many of them even have identical binaries.
- Many of these spam messages contain random text below the image.
- Most of them do not contain any web links that the user can click.
- Most of them ask the user to visit a .com Web site with a domain name consisting of six digits like 123456.com, and the user has to manually type that URL into the browser.









