Commodity malware backdoor SystemBC has evolved to now automate a number of key activities, as well as use the anonymizing Tor platform. These overarching changes make it both easier for cybercriminals to deploy the backdoor, as well as cloak the destination of the command-and-control (C2) traffic.
SystemBC, a proxy and remote administrative tool, was first discovered in 2019. Researchers believe it is being used by ransomware-as-a-service affiliates due to it being associated with multiple types of ransomware that are deployed in the same way. Once it’s executed, the backdoor is used by ransomware actors to set up a persistent connection on victim systems.
“While SystemBC has been around for over a year, we’ve seen both its use and its features continue to evolve,” said Sivagnanam Gn and Sean Gallagher, researchers with Sophos, in a Wednesday analysis. “The most recent samples of SystemBC carry code that, instead of acting essentially as a virtual private network via a SOCKS5 proxy, uses the Tor anonymizing network to encrypt and conceal the destination of command and control traffic.”
Researchers warn that over the past few months they have detected hundreds of attempted SystemBC deployments globally. The backdoor has been utilized in recent Ryuk and Egregor ransomware attacks, and has also often been leveraged in combination with post-exploitation tools such as Cobalt Strike, they said.
SystemBC Proliferation
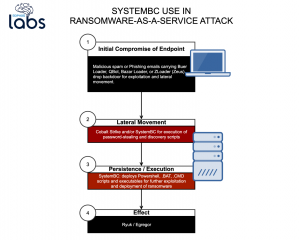
Initially, ransomware groups that leverage SystemBC have been observed first infecting systems using spam or phishing emails. These emails then trick the victim into downloading the Buer loader, QBot, ZLoader or other types of malware, which are used for initial exploitation and lateral movement.
From there, attackers then use SystemBC (along with Cobalt Strike, in some cases) in order to scoop up passwords from victim systems – although in some cases, the SystemBC backdoor was only deployed to servers after attackers gained administrative credentials, and then used it to move deeper into the targeted network, researchers said.
SystemBC is used primarily to gain further persistence on the victim system. In what’s now a more automated process, the backdoor can deploy PowerShells; .CMD scripts (A CMD script file features one or more commands in plain text format that are executed in order to perform various tasks); Windows commands; malicious executables and dynamic link libraries (DLLs).
Researchers said, these key activities have been automated now so that operators can launch multiple attacks without the need for hands-on-keyboard activity. They are used for further exploitation and the deployment of the final ransomware (which in recent cases have been Ryuk or Egregor).
SystemBC Updates
The backdoor also acts both as a network proxy for concealed communications; here a primary change exists in how SystemBC has evolved.
Before, SystemBC primarily set up SOCKS5 proxies on victim computers, which could then be used by threat actors to tunnel/hide the malicious traffic associated with other malware. A SOCKS5 proxy server creates a Transmission Control Protocol (TCP) connection to another server behind the firewall on the client’s behalf, then exchanges network packets between the client and the actual server.
“With the proxies initialized, the client now begins to retrieve data requested from the C2 via HTTPS,” researchers with Proofpoint said in a writeup in 2019, after the malware was discovered. “The use of SOCKS5 is not a major differentiator; it’s just another potential technology malware authors can use for this purpose and the primary proxy protocol,” they noted at the time.
Most of the C2 communications with the more recent versions of SystemBC, however, are over a Tor connection: “The Tor communications element of SystemBC appears to be based on mini-Tor, an open-source library for lightweight connectivity to the Tor anonymized network,” said Sophos reserchers. “The code of mini-Tor isn’t directly duplicated in SystemBC. But the bot’s implementation of the Tor client closely resembles the implementation used in the open-source program, including its extensive use of the Windows Crypto Next Gen (CNG) API’s Base Crypto (BCrypt) functions.”
These changes to the backdoor “are likely an effort to make it more difficult to detect the network traffic associated with command and control of SystemBC,” Sophos’ Gallagher told Threatpost.
“I can’t say if it’s more effective to use Tor instead of a SOCKS5 proxy, but it gives the attacker a more obfuscated and encrypted way of sending commands, scripts, and more malware to the bot,” Gallagher explained. “A single SOCKS5 proxy could be quickly blocked, while Tor is more resilient in its routing.”
SystemBC proves to be another useful tool for cybercriminals who have been launching increased levels of ransomware attacks. This past year, in fact, ransomware attacks more than doubled year-over-year (up 109 percent).